1. Installation setup
System requirements
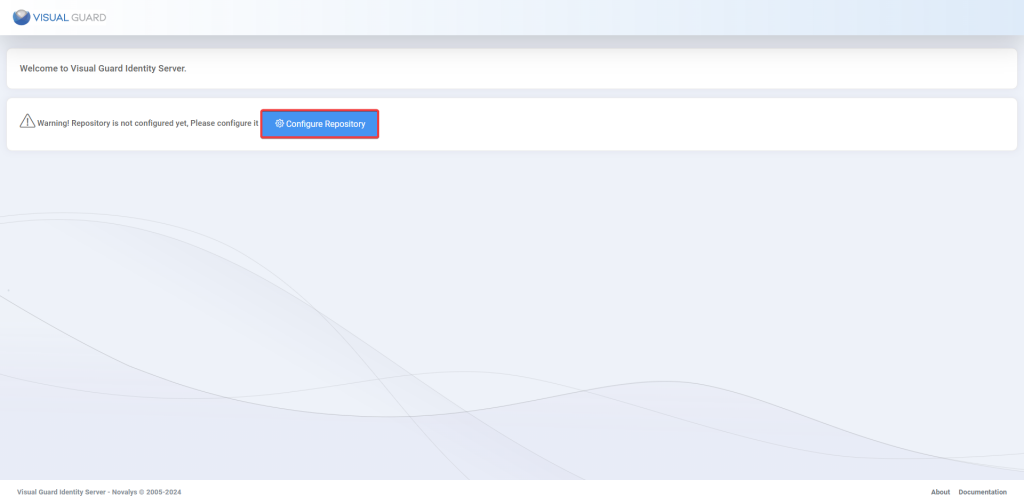
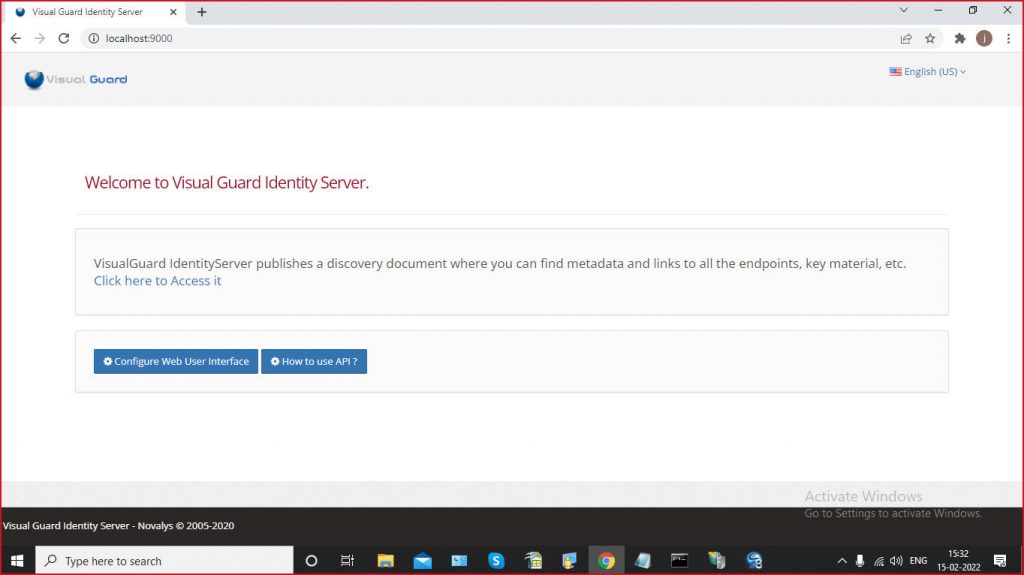
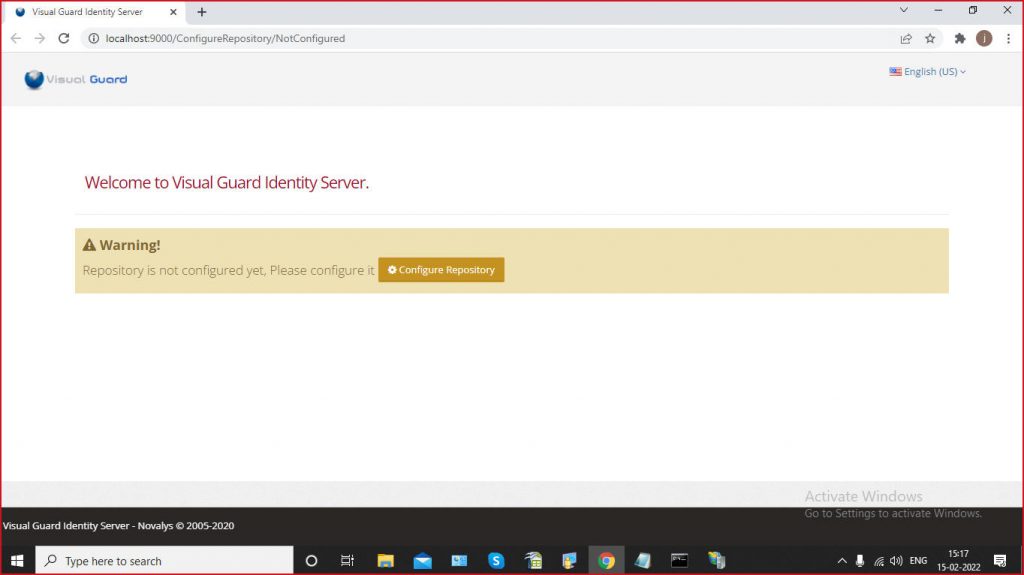
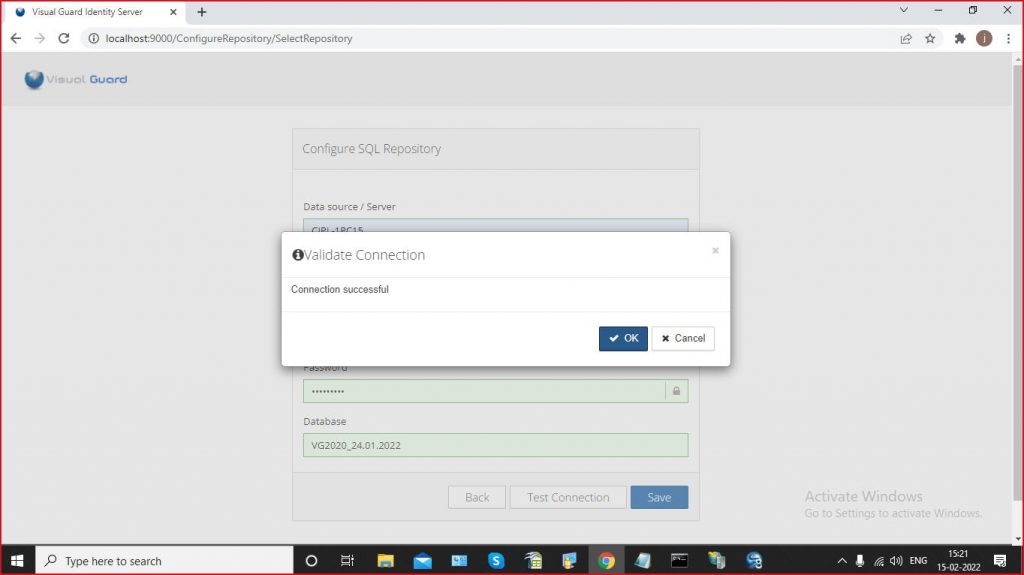
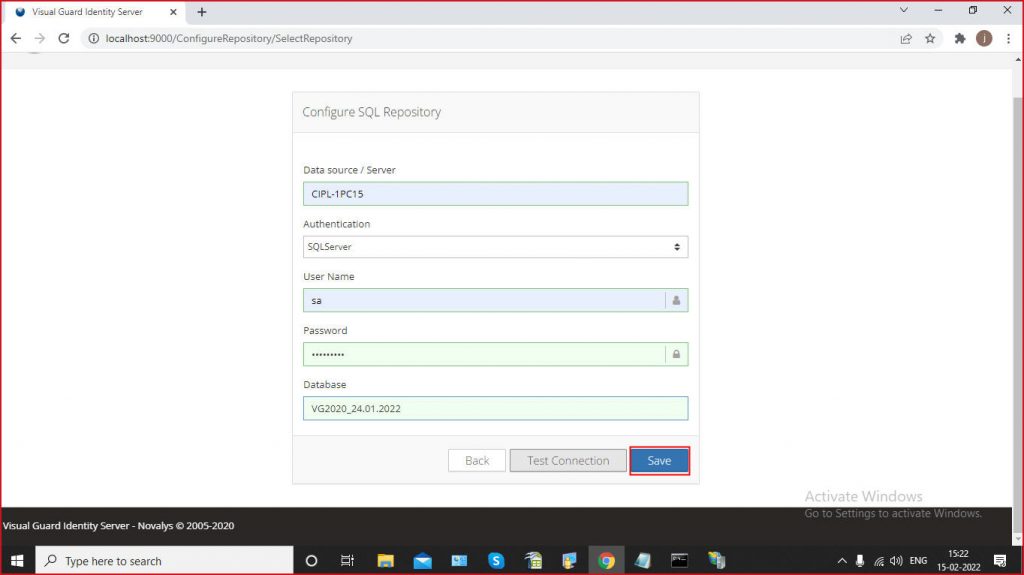
Please check the following requirements before installing Visual Guard Identity Server.
Visual Guard 2024.0
- Operating System: Windows Server 2012, 2016, 2019, 2022
- Hard Drive: 512 GB to 1 TB – Fast drive recommended, ideally SSD
- CPU: 4 core min – 3 Ghz or higher
- RAM: 8 GB
- Software:
- Web browser with JavaScript support.
- .Net Core hosting bundle 6.0.You can download the hosting bundle (dotnet-hosting-6.0) from the official Microsoft website. (https://dotnet.microsoft.com/en-us/download/dotnet/thank-you/runtime-aspnetcore-6.0.26-windows-hosting-bundle-installer)
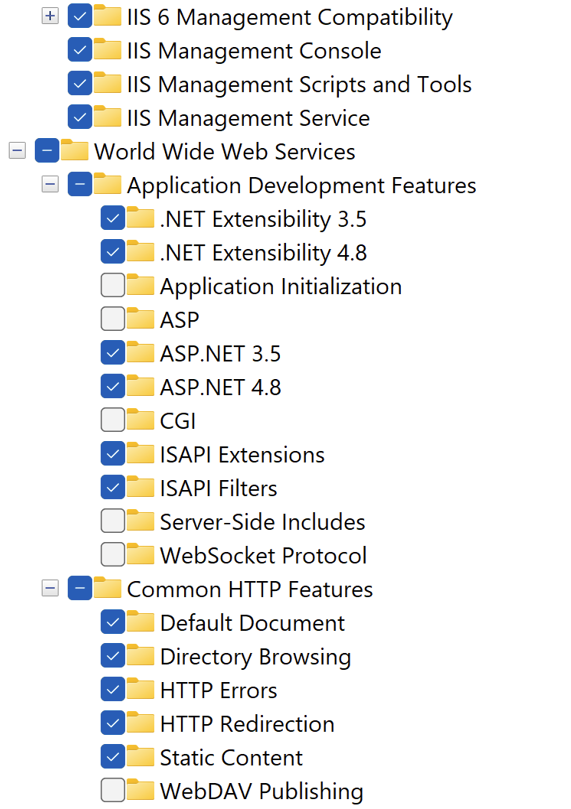
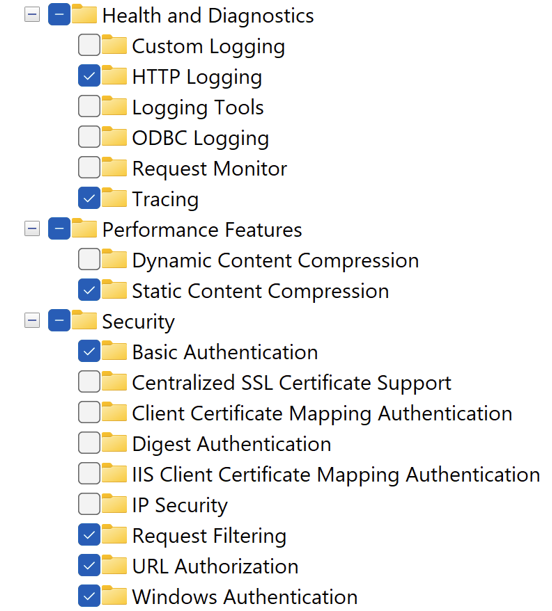
- IIS with the necessary Windows features should be installed as described below.
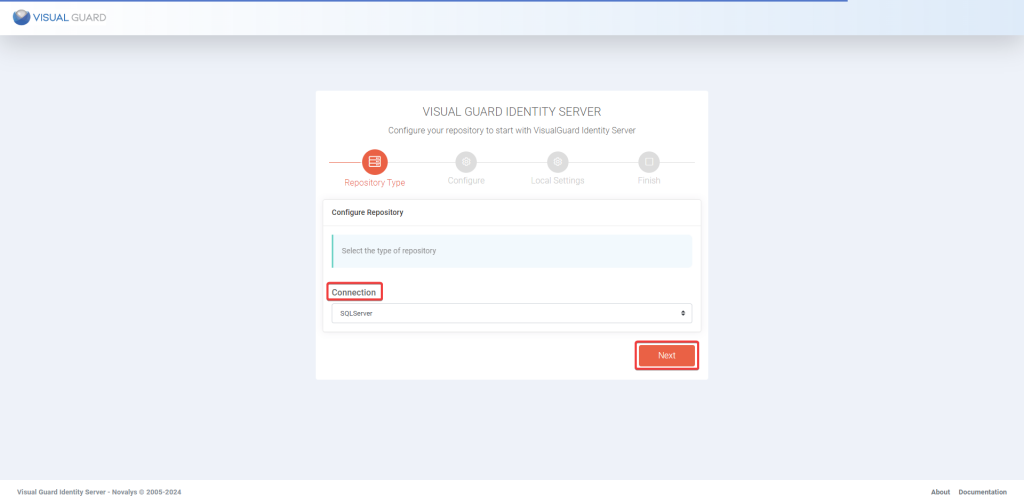
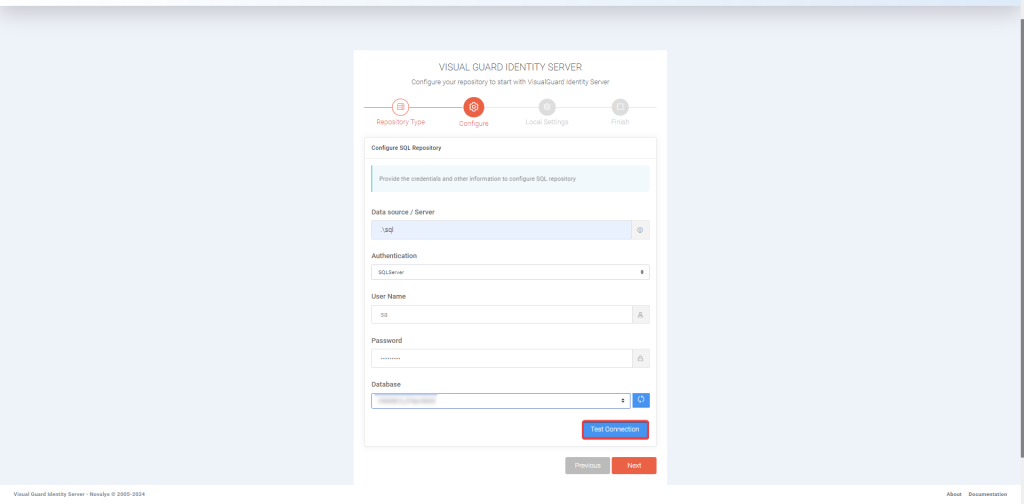
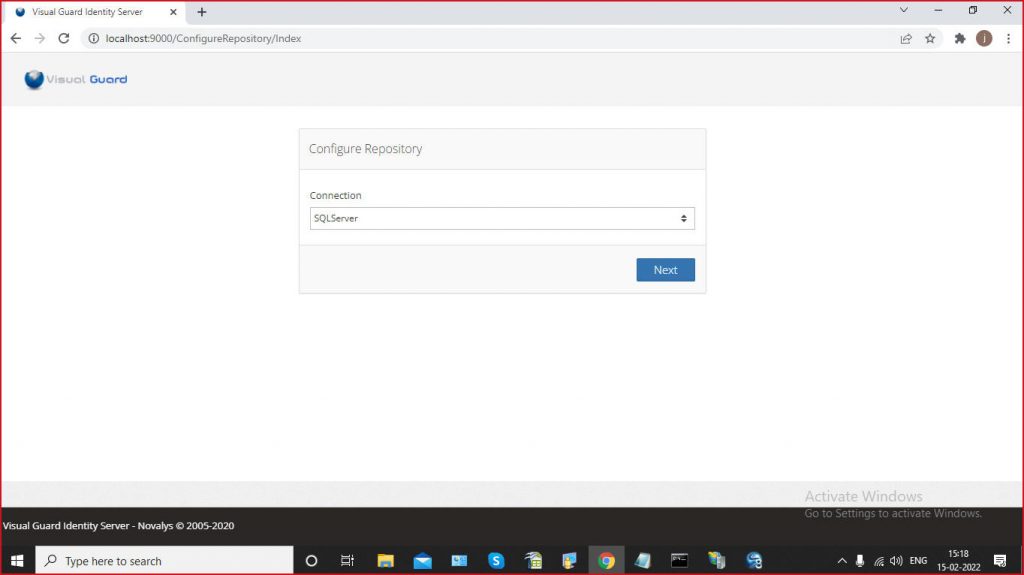
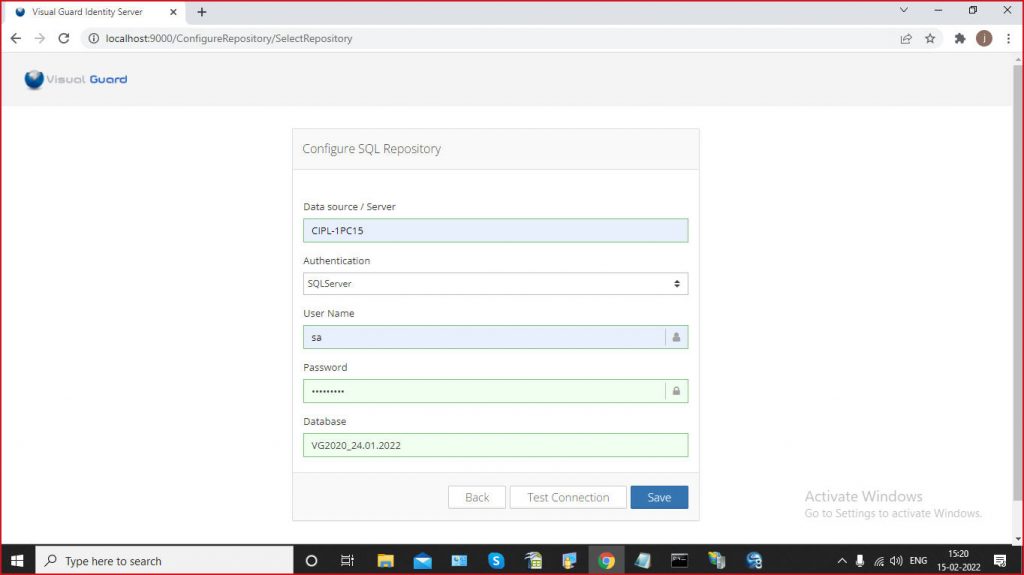
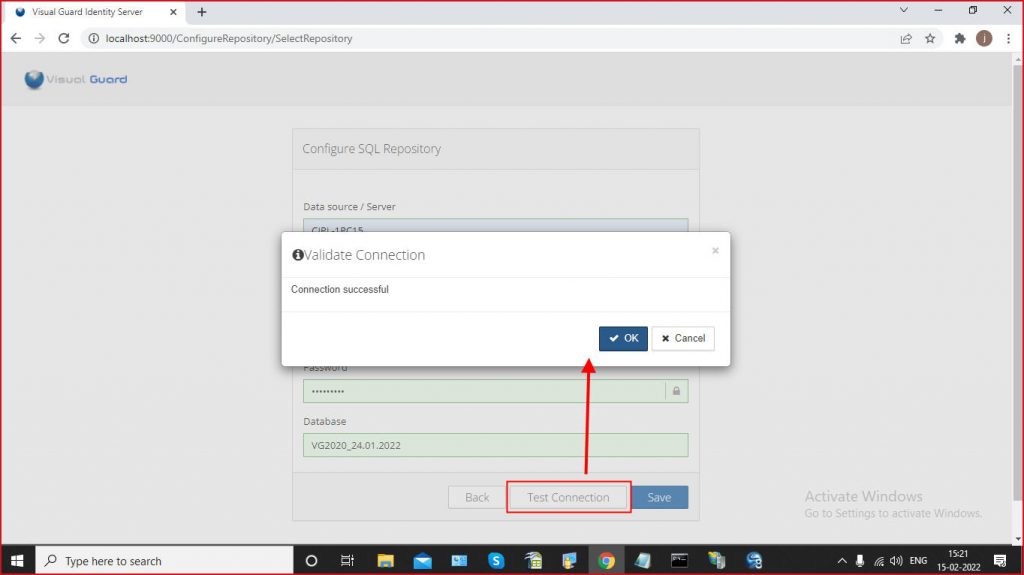
- VGRepository
- Require SQL Server 2012 or later, with a minimum of the Standard Edition.
- Require Oracle Database with Oracle9i or later. Please ensure the Oracle Driver is installed.
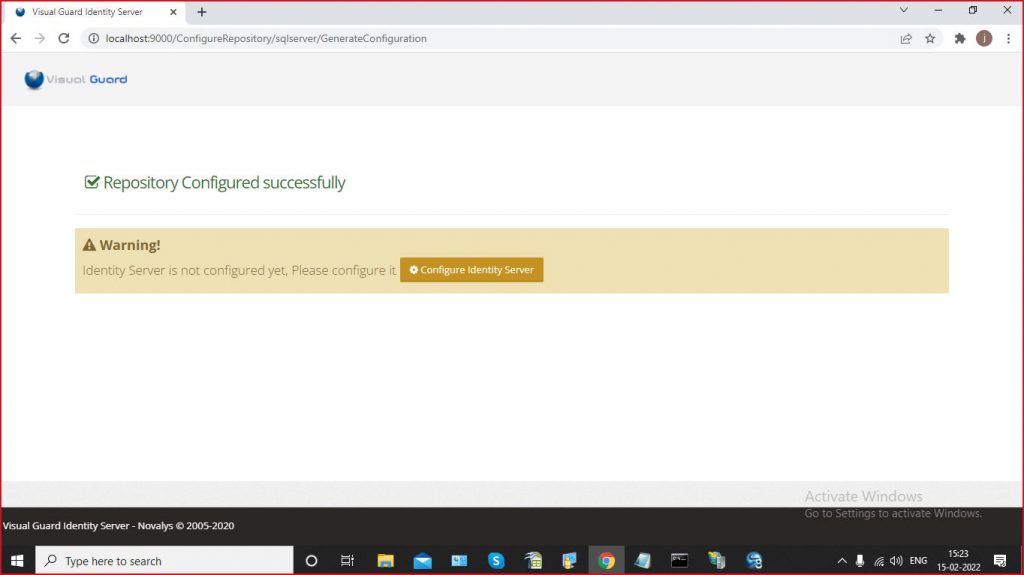
- Install the VGIdentityServerSetup. [Link available in the table above]
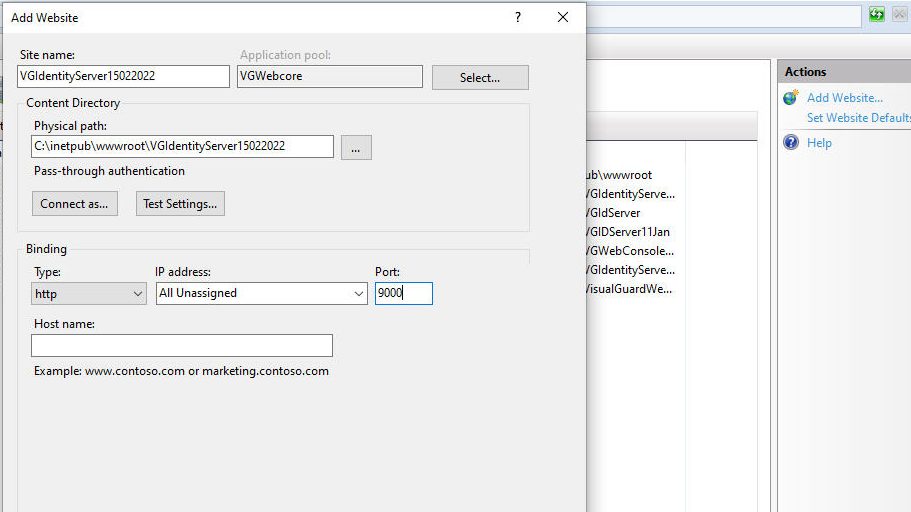
- Doing so, will create a ‘VisualGuardIdentityServer’ website.
- It will also create an application pool ‘AspNetCore’ ‘with – .Net CLR Version – “No Managed Code”.
(If not created, please create it manually)
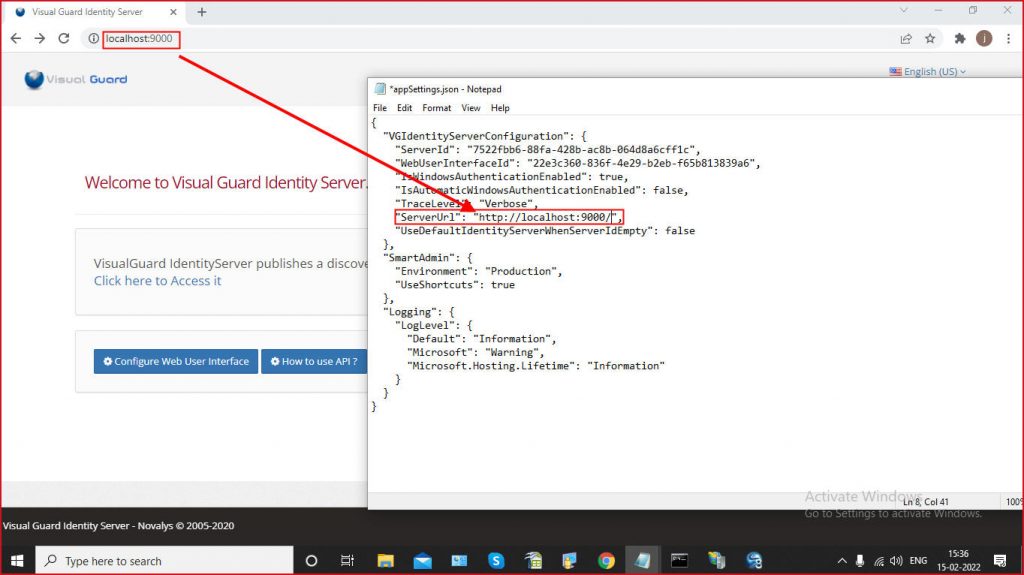
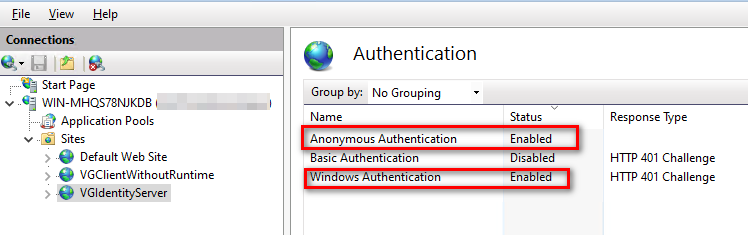
- Check the list of websites, select ‘VisualGuardIdentityServer’.
Go to ‘Advanced Settings’, and select application pool – ‘AspNetCore’. - Check ‘permissions’, and assign full permissions to ‘IIS_IUSRS’.
- Check the application root path.
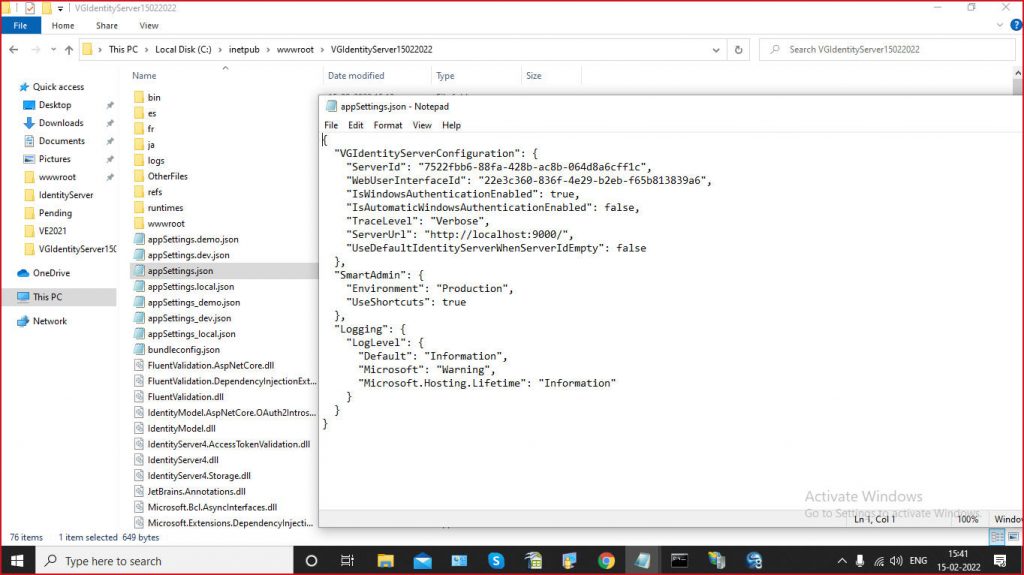
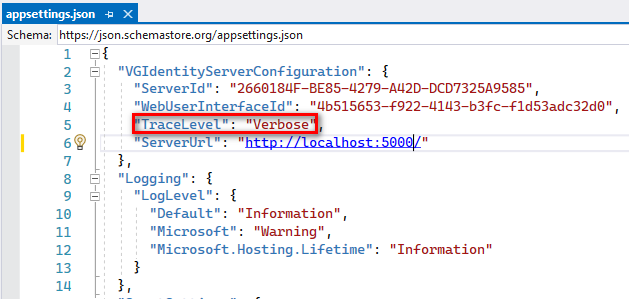
Select ‘web.config’ , please make sure it contains the following values:
<aspNetCore processPath="dotnet" arguments=".\Novalys.VisualGuard.Tools.VGIdentityServer.dll" stdoutLogEnabled="false" stdoutLogFile=".\logs\stdosut">
<environmentVariables />
</aspNetCore>
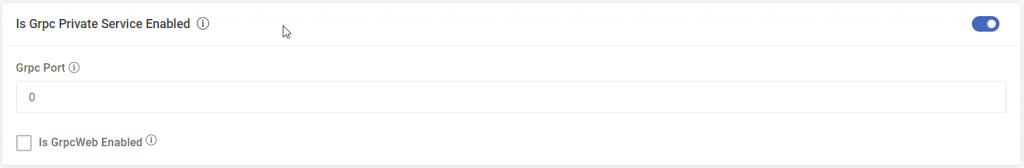
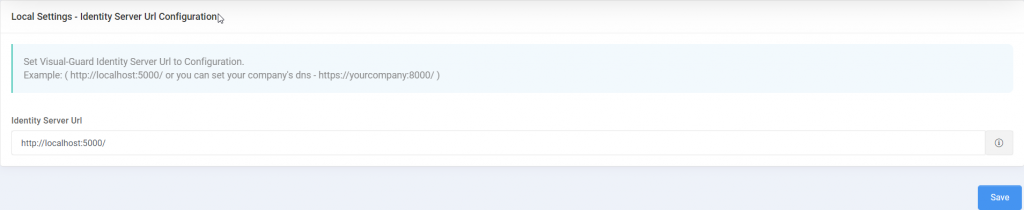
Private mode Communication
- Windows Server 2022 Build 20348 or later.
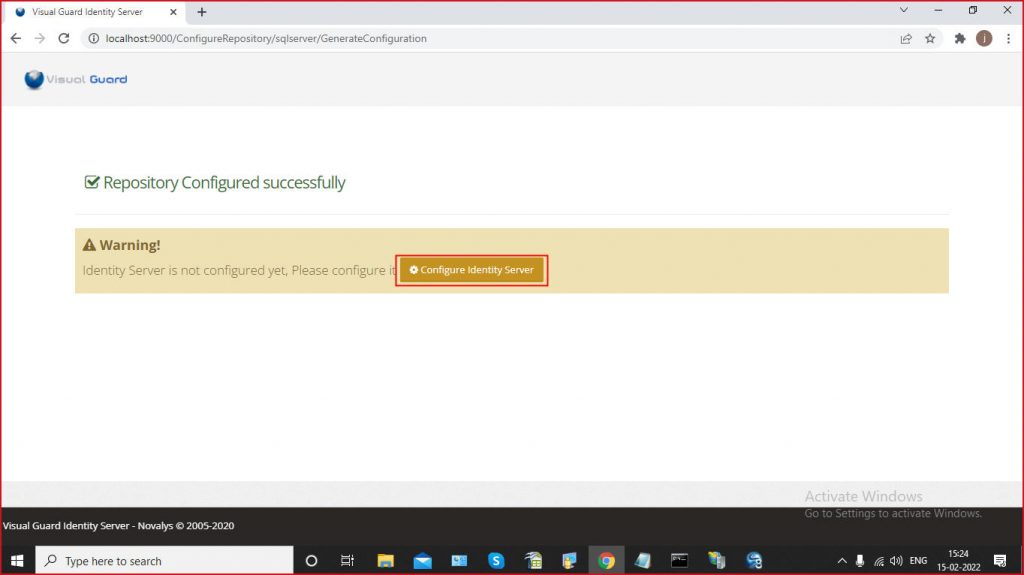
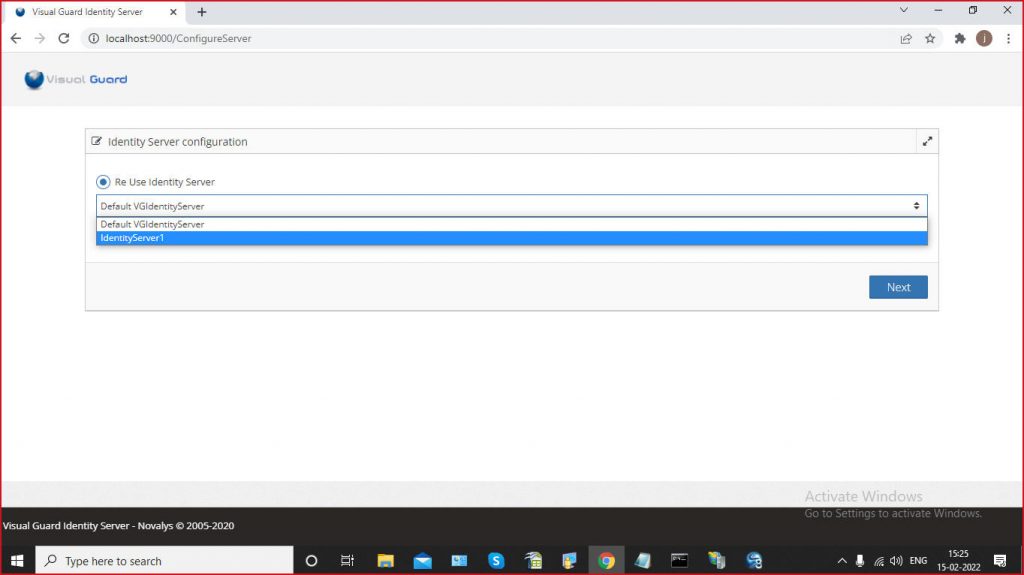
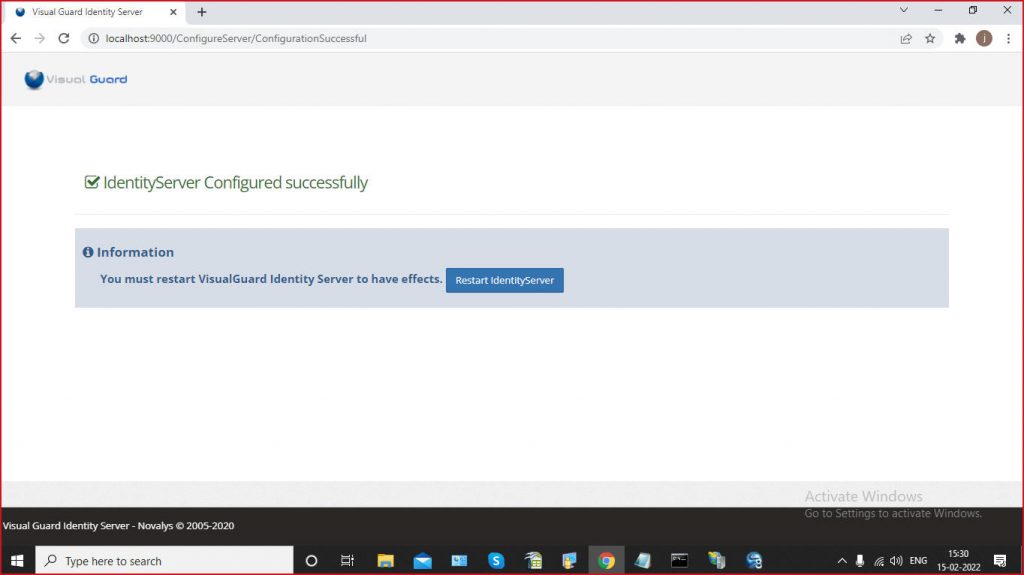
Installation Steps
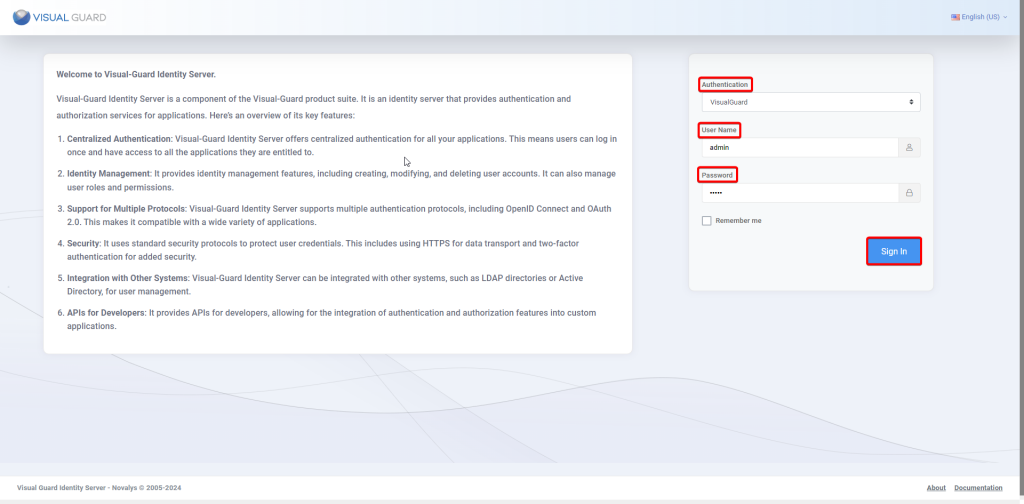
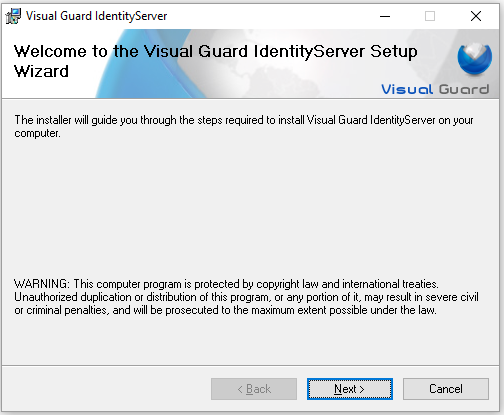
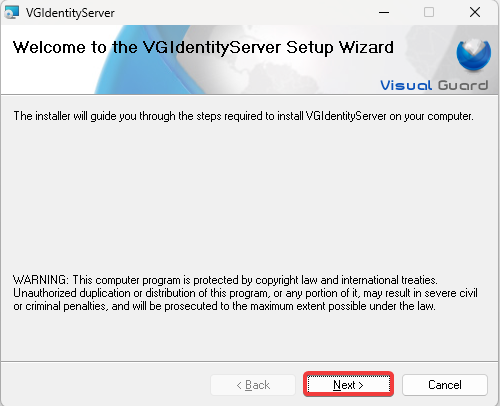
Step 1: Download Visual Guard Identity Server setup and follow the installation wizard
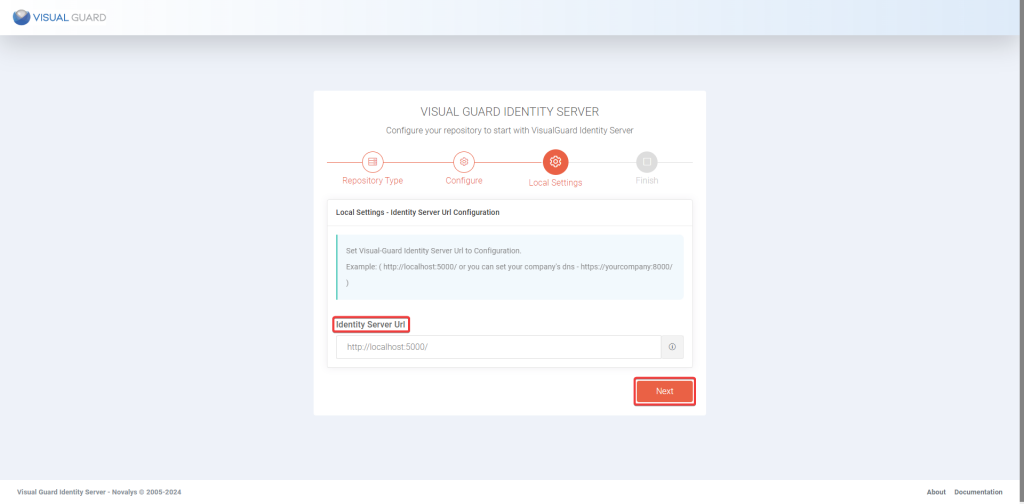
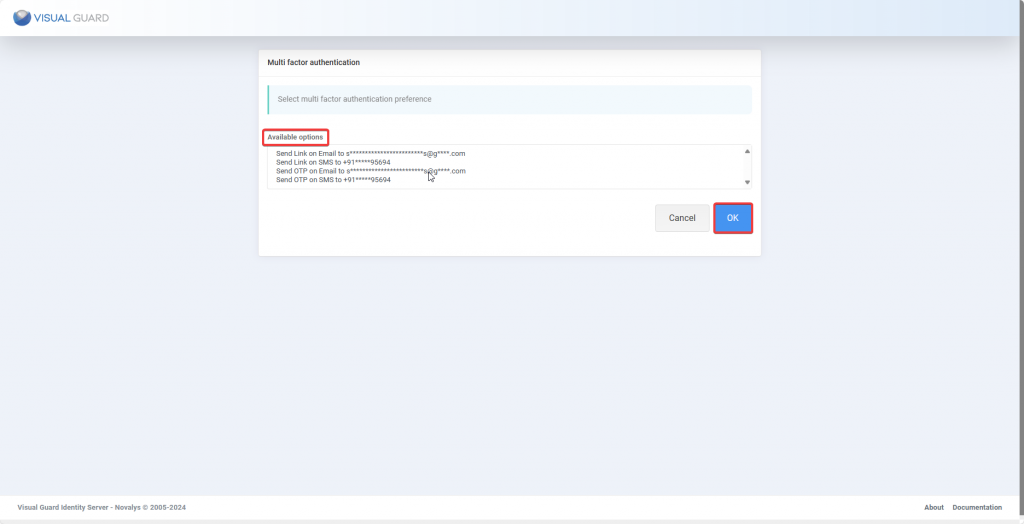
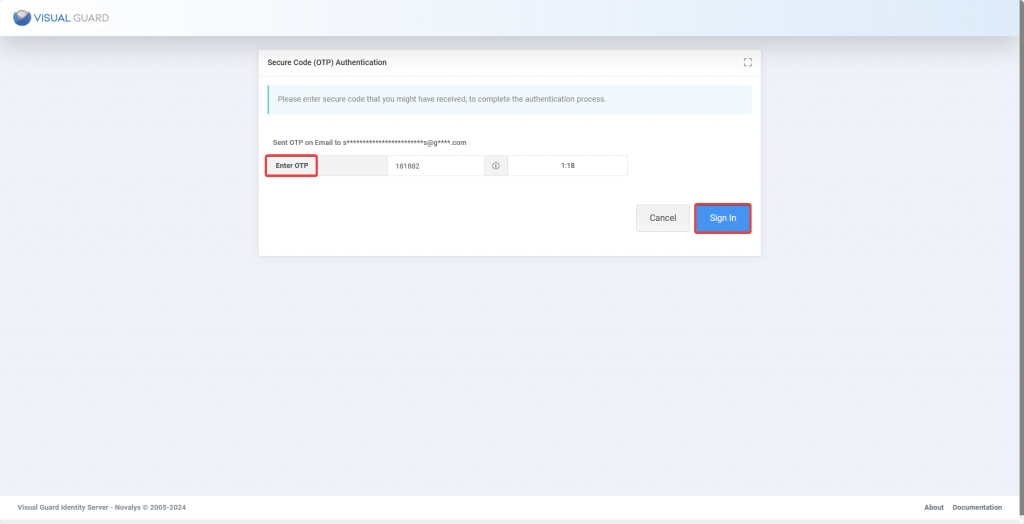
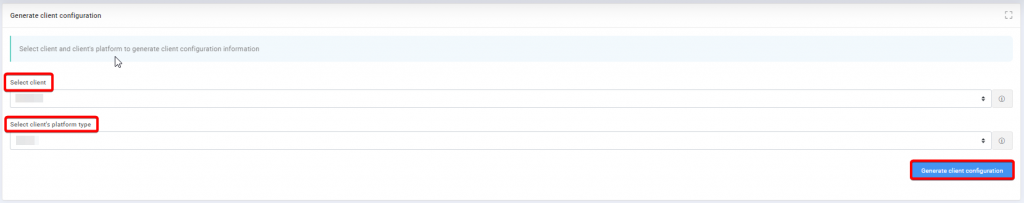
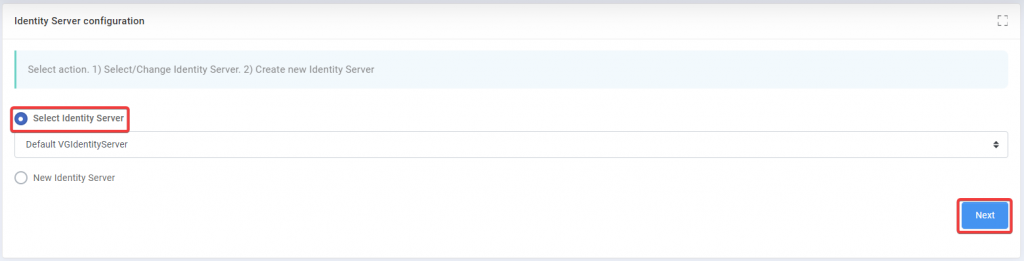
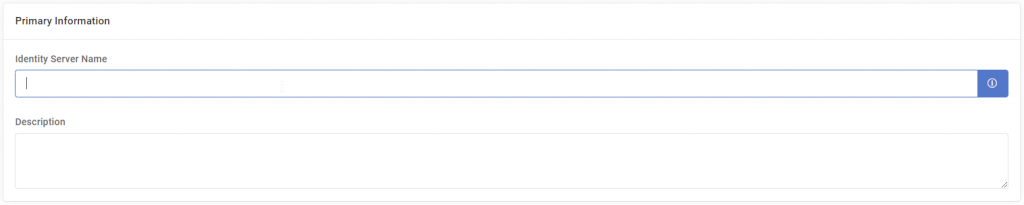
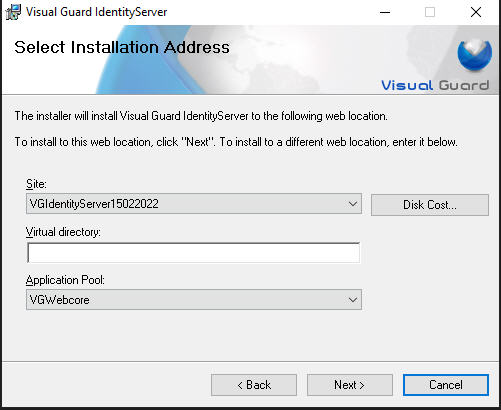
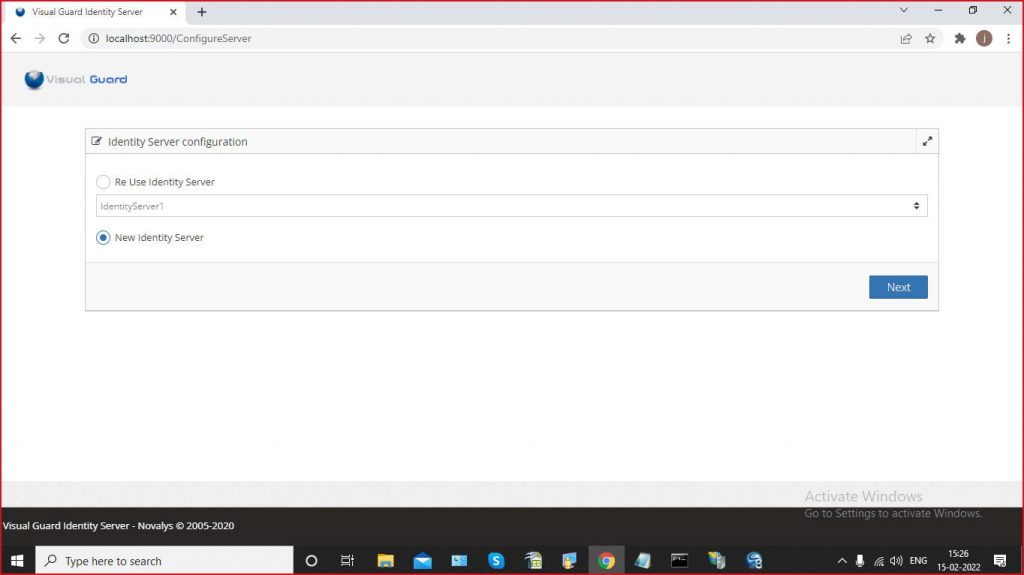
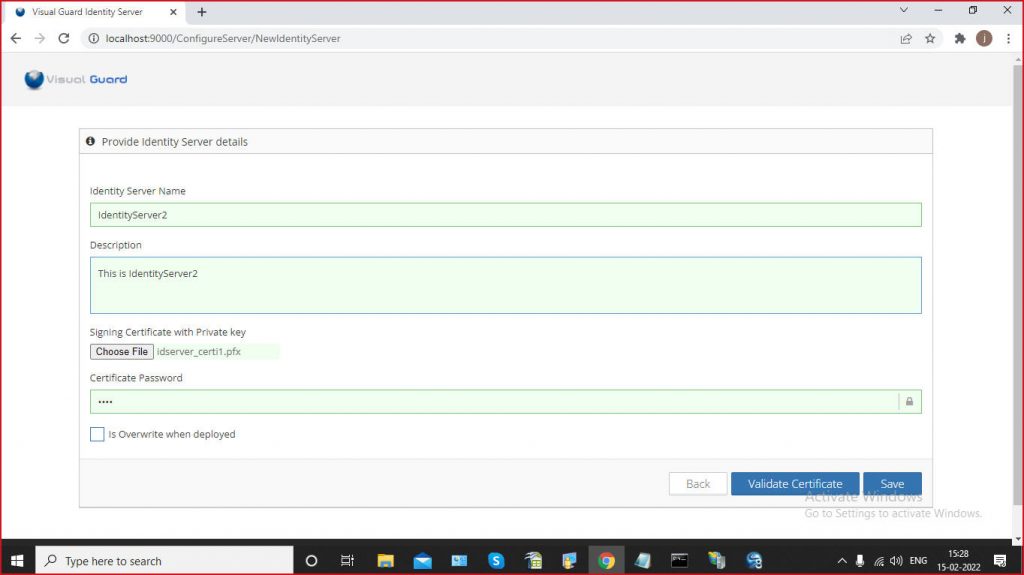
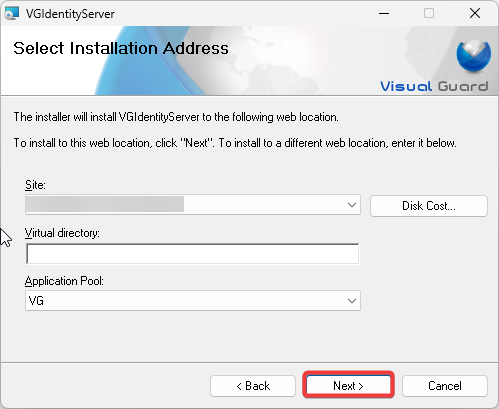
Step 2: Enter the required information, Site, Application pool and click Next
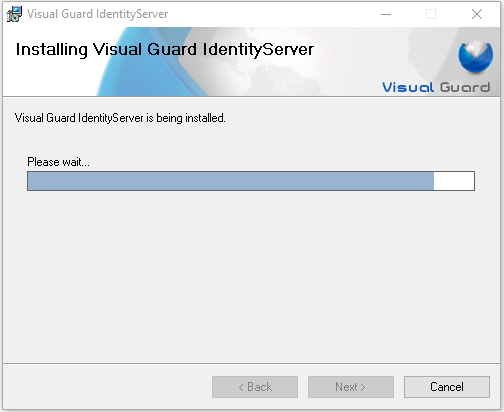
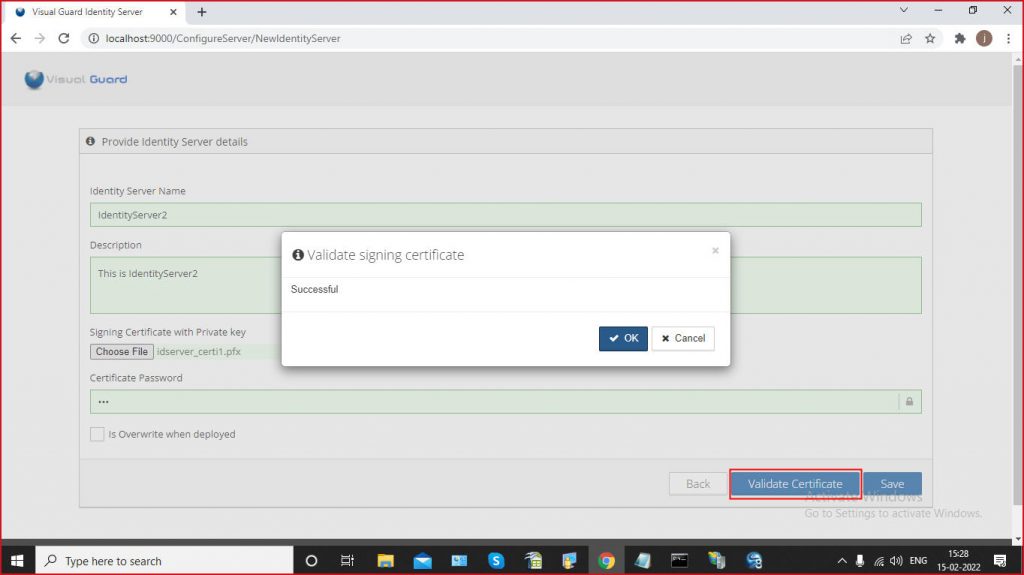
Step 3: Installation process will begin
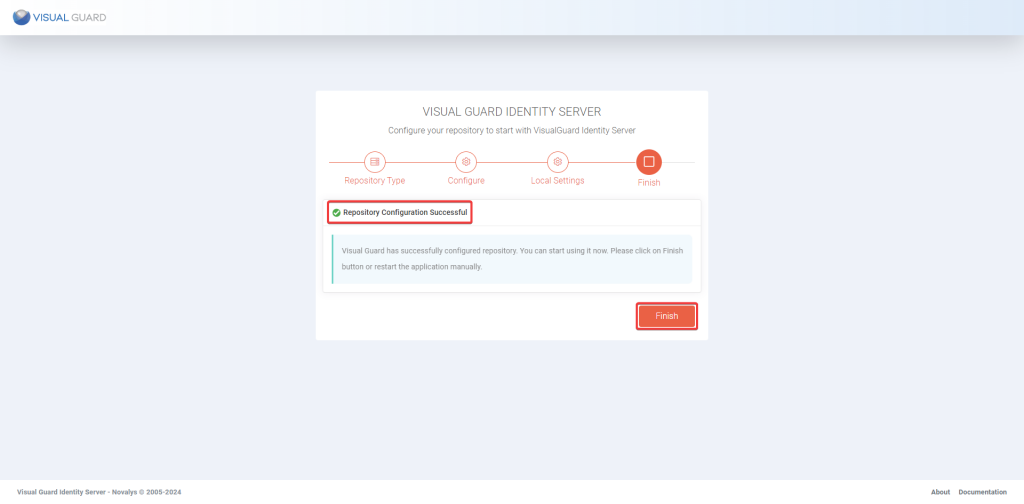
Step 4: Once installation is complete, you will be notified with a message confirming the successful setup. Please click “Close” to exit the setup.
1.1 How to migrate from VGServer ?
The VGServer has been replace by Visual-Guard Identity Server.
VG Identity Server works with the bearer Token, the VGToken, which is contained inside of the claims.
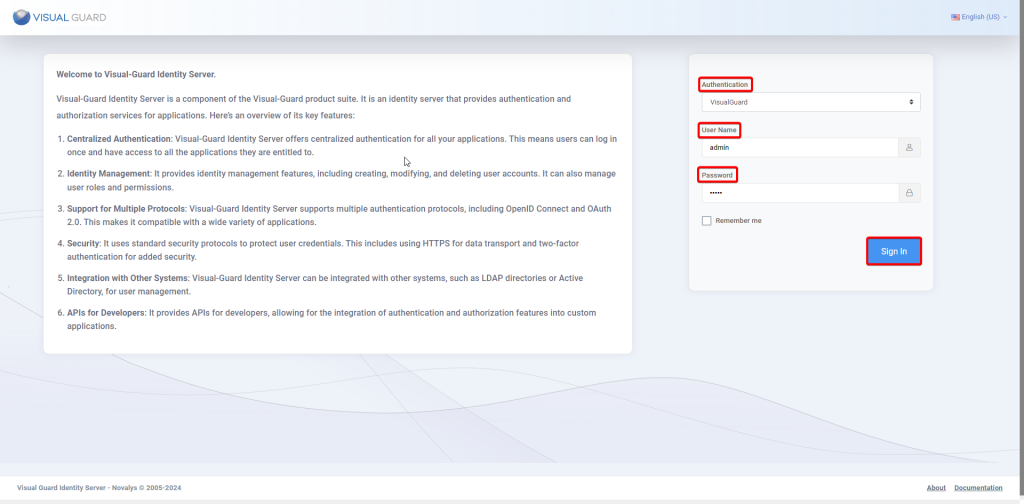
We need to authenticate from VG Identity Server
The API has been updated.
Please refer to the following list to find out how to update the API:
- /Security/Principal/GetIdentity replace by /api/Principal/GetIdentity
- /Security/GetRoles replace by /api/Principal/GetCurrentRoles
- /Security/IsInRoleByName/ replace by /api/Principal/IsInRoleByName
- /Security/HasPermissionByName/ replace by /Security/HasPermissionById/
- /Security/GetPermissions replace by /api/Principal/GetCurrentPermissions