1. Installation
Introduction
Visual Guard is a robust application security system that helps safeguard your data and systems from unauthorized access and potential breaches. It integrates seamlessly with your existing software applications and provides granular control over security, user permissions, and access rights.
Visual Guard provides two consoles for managing security settings:
- WinConsole: A Windows application that needs to be installed on your system.
- WebConsole: A web-based application that can be accessed from any web browser.
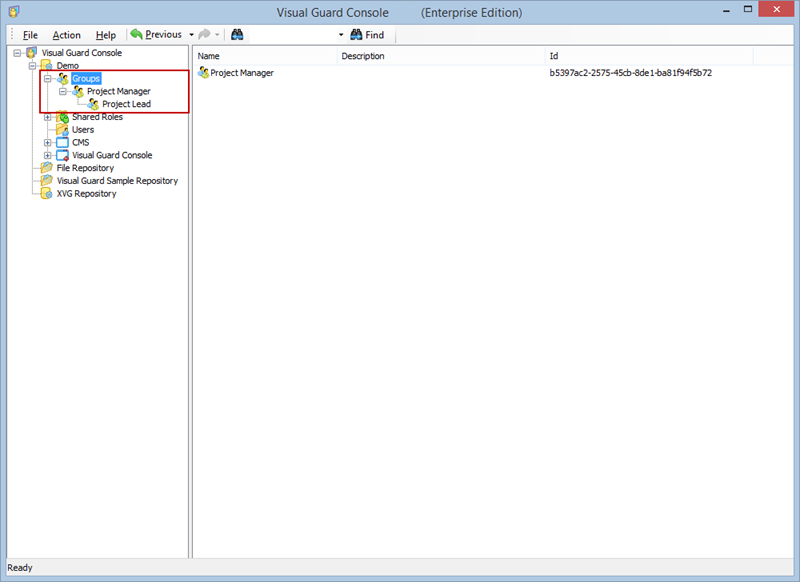
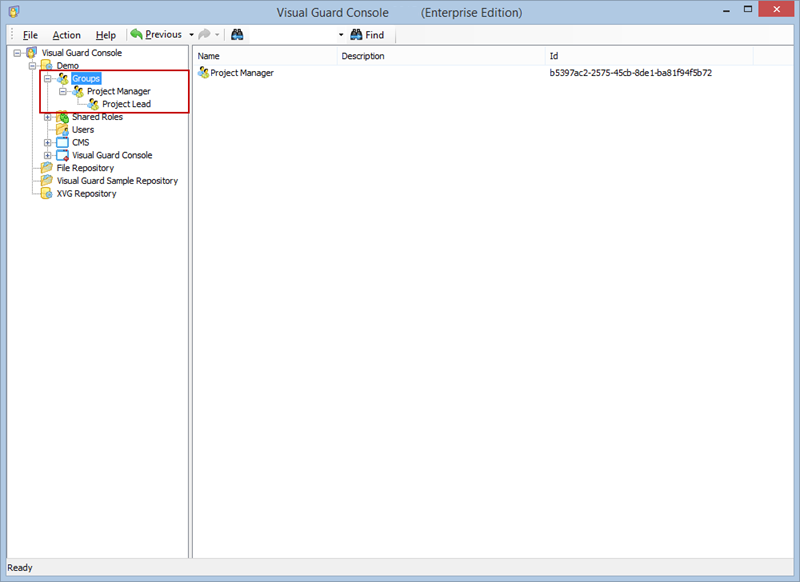
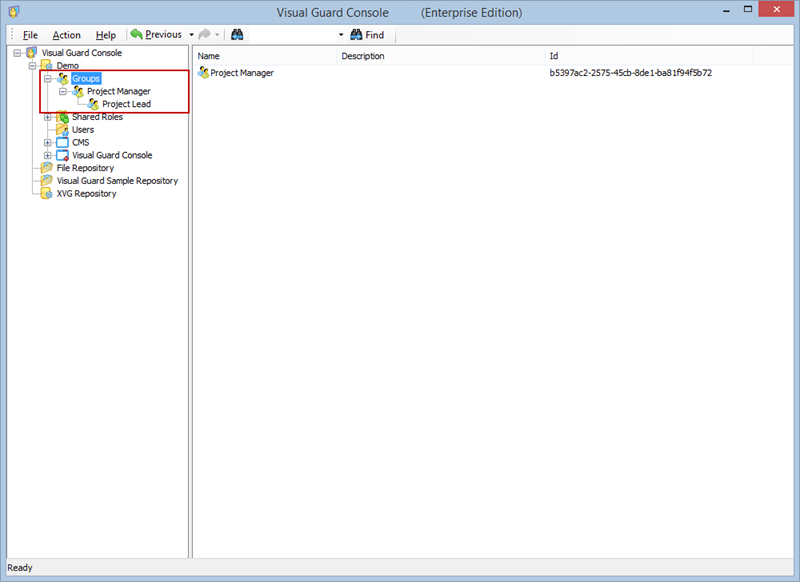
Additionally, Visual Guard incorporates a notion of groups, allowing you to manage multiple roles and users under one group for easier management of permissions.
Visual Guard also includes the VGIdentityServer component that supports the OAuth 2.0 and OpenID protocols. This component allows client applications to perform user authentication and authorization operations.
Getting Started
Installation
To install Visual Guard, WinConsole, and VGIdentityServer, follow the steps below:
- Download the Visual Guard installation package.
- Run the installer and follow the on-screen prompts.
- Restart your system after installation completes.
The WebConsole does not need to be installed and can be accessed directly from your web browser.
Configuration
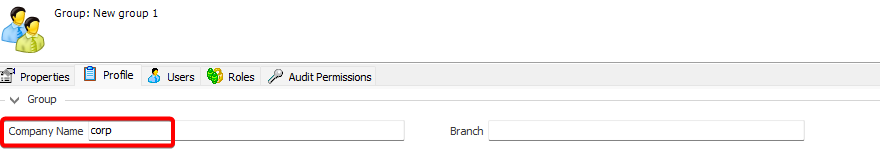
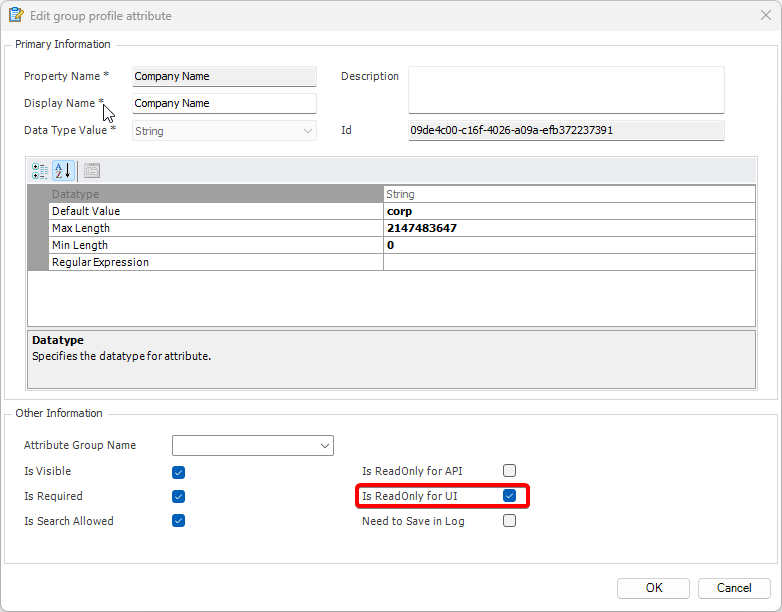
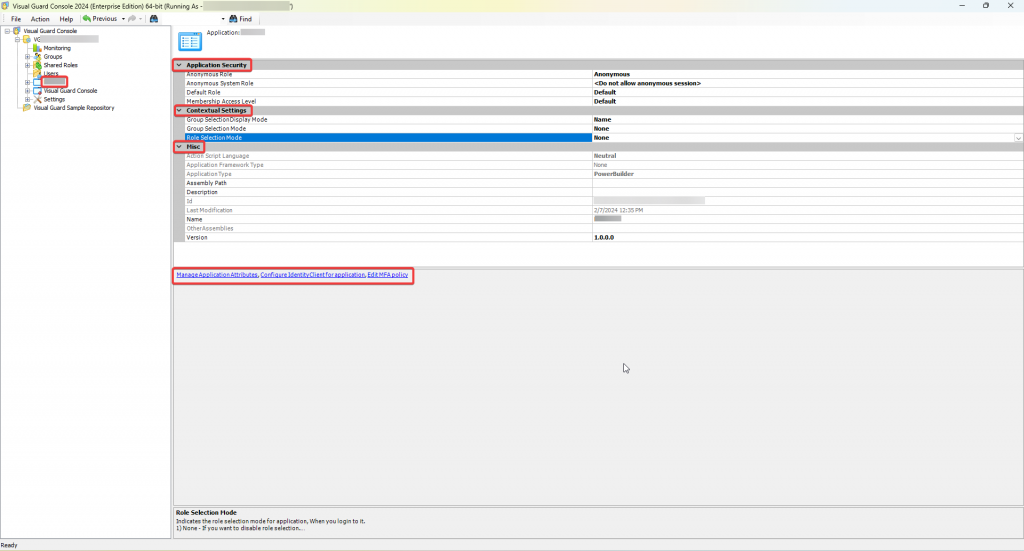
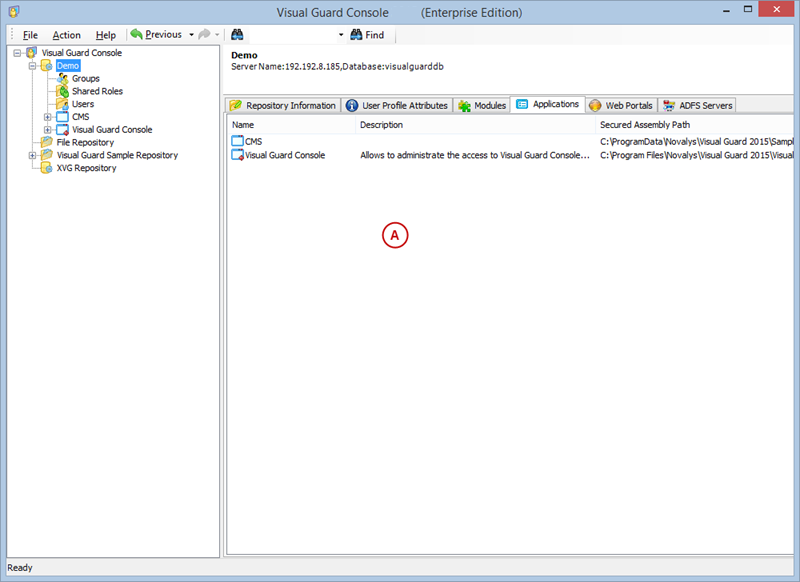
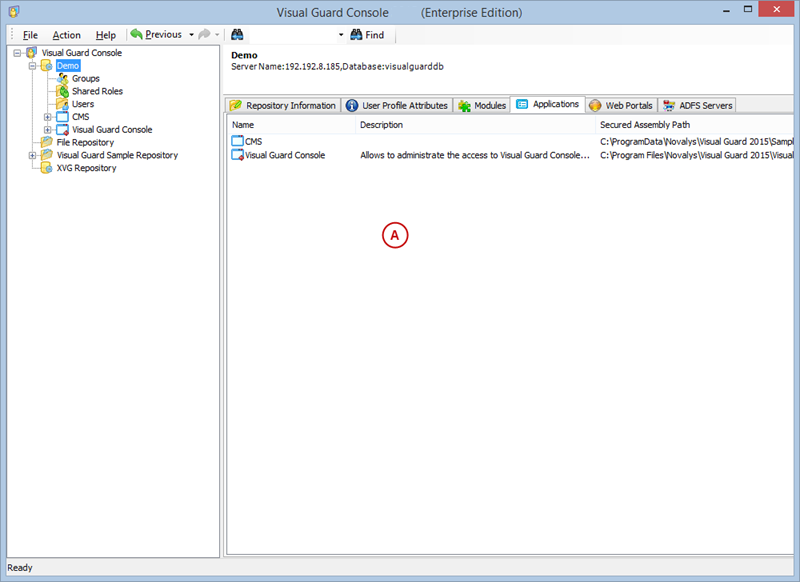
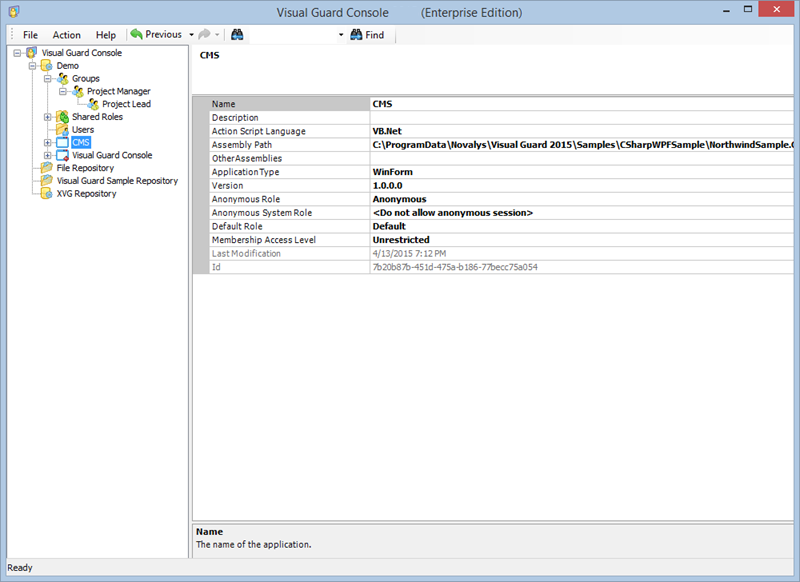
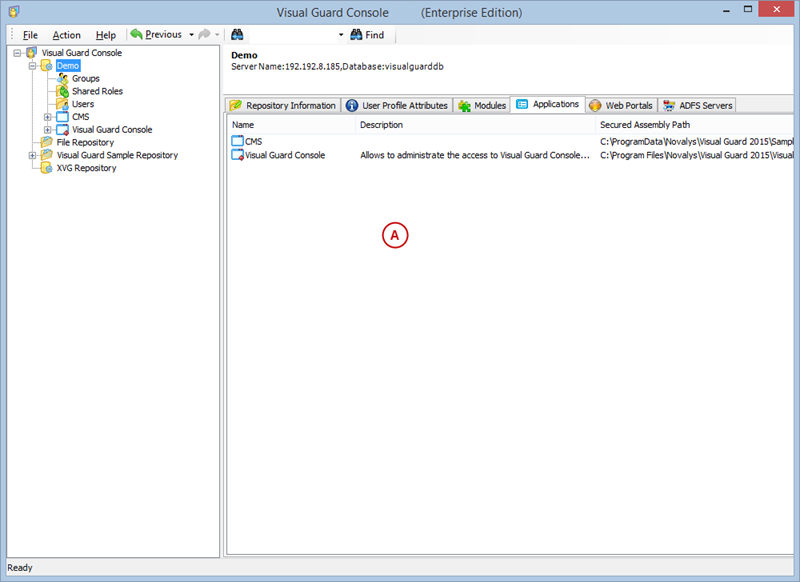
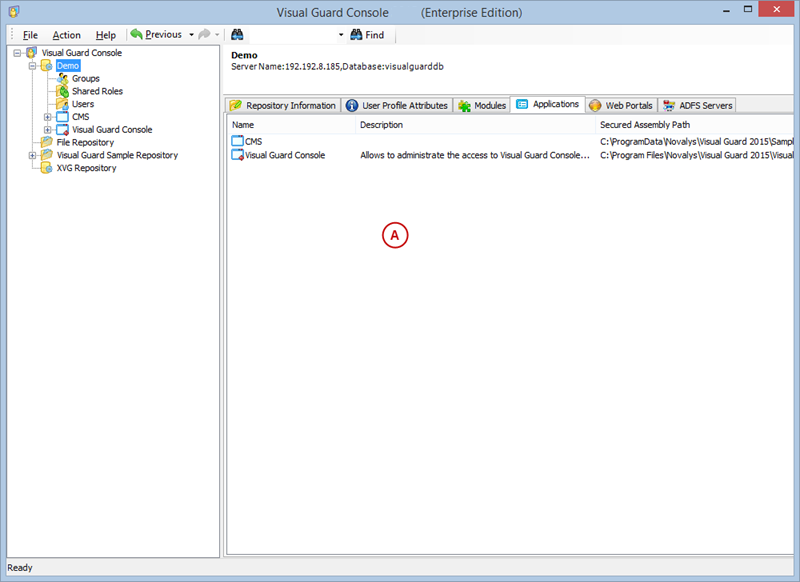
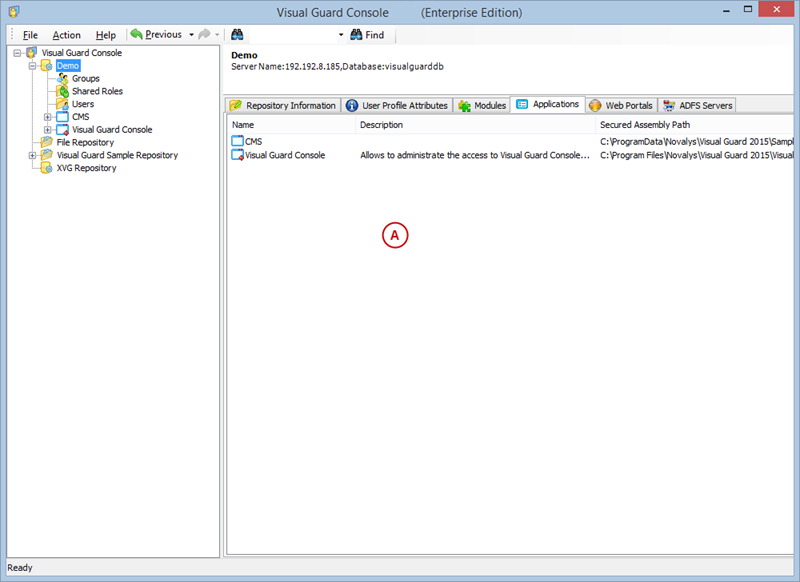
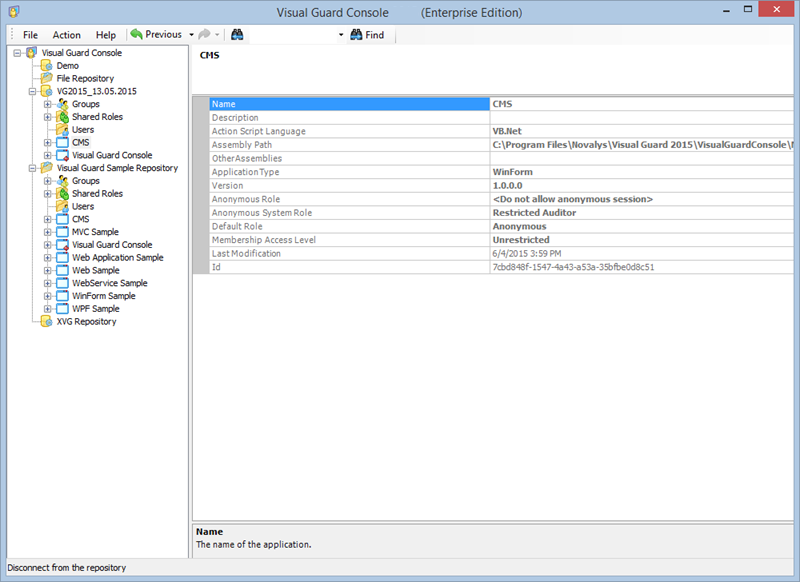
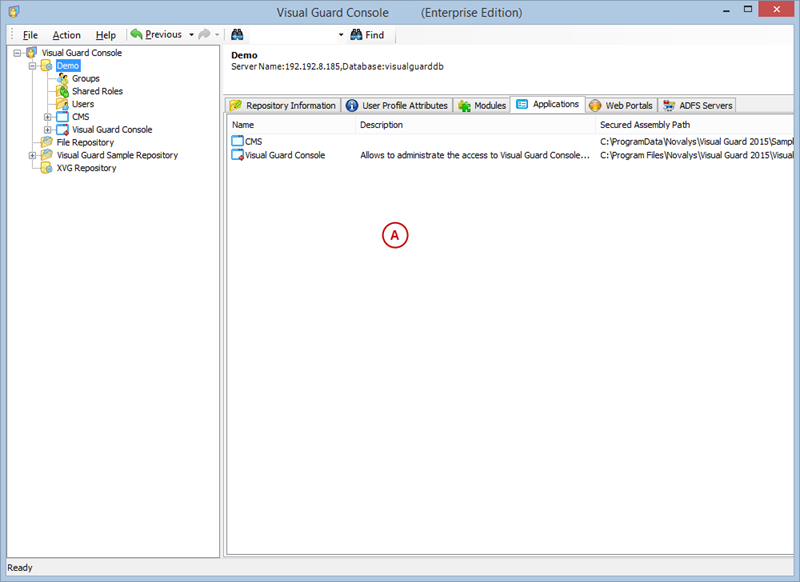
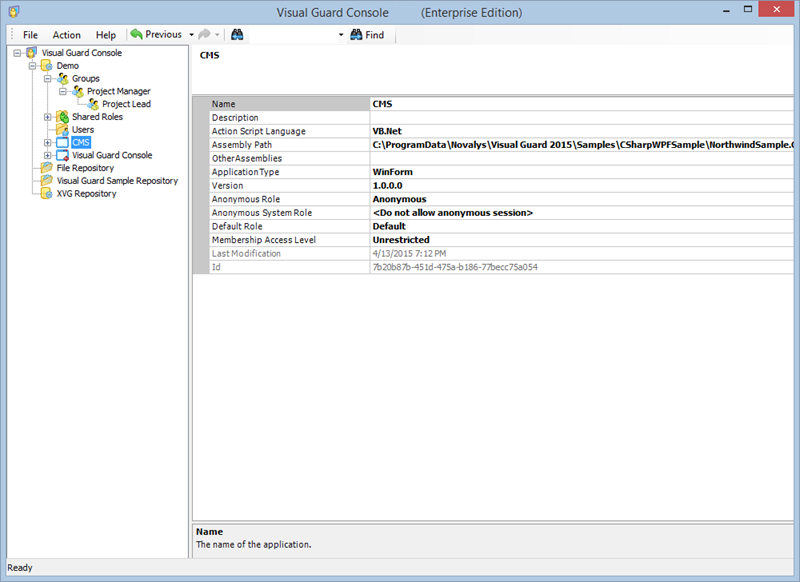
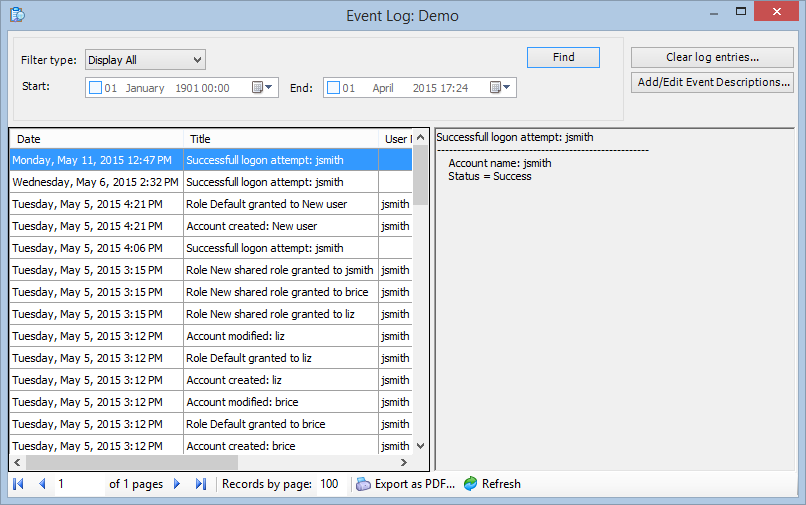
After installation, you will need to configure Visual Guard to suit your application needs. This involves setting up a VGRepository, defining user roles, assigning permissions to these roles, and setting up groups.
Creating a VGRepository
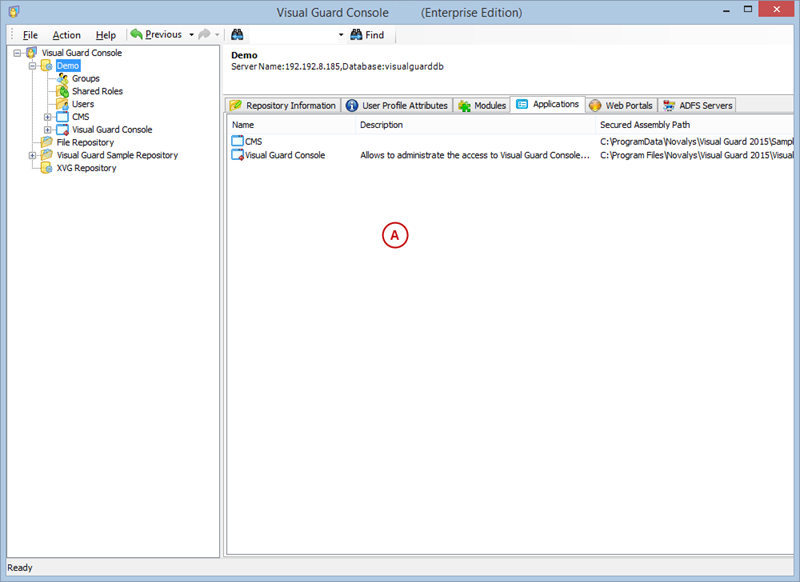
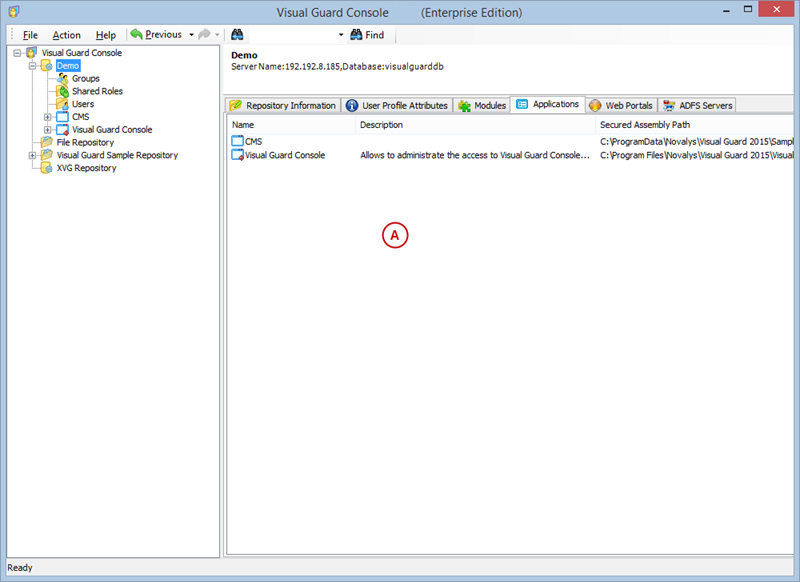
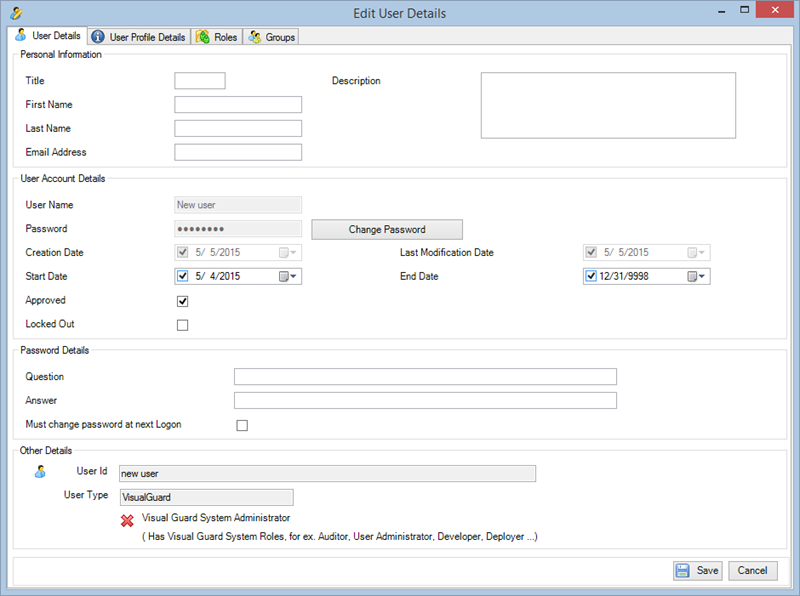
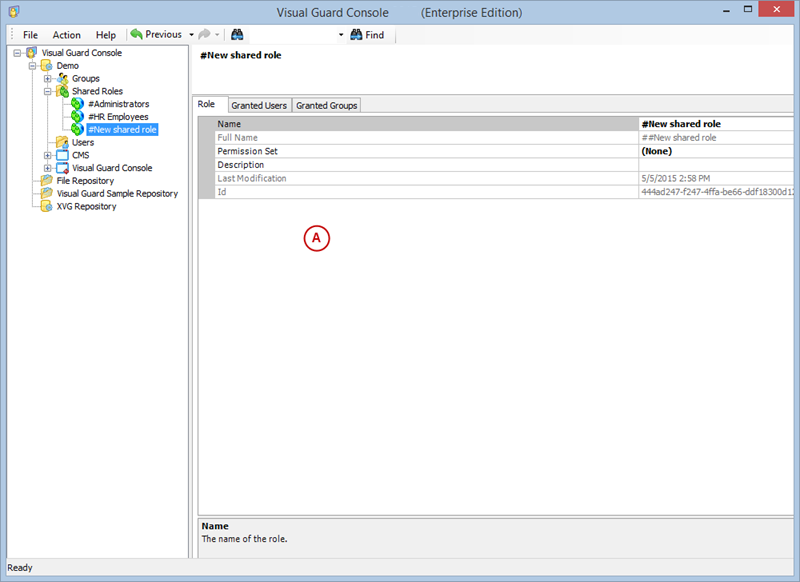
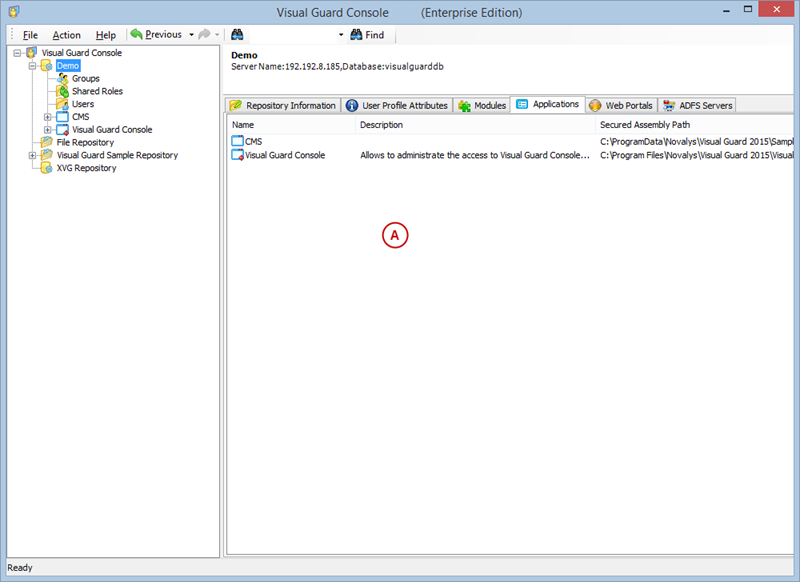
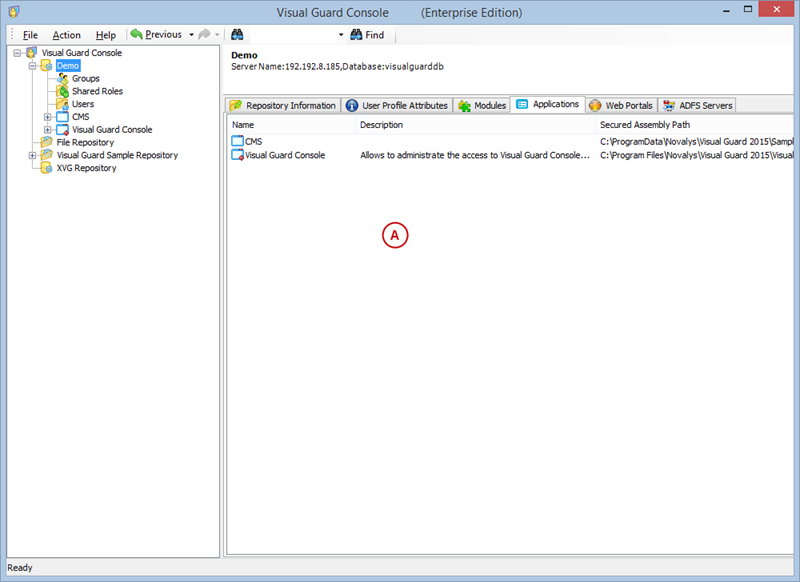
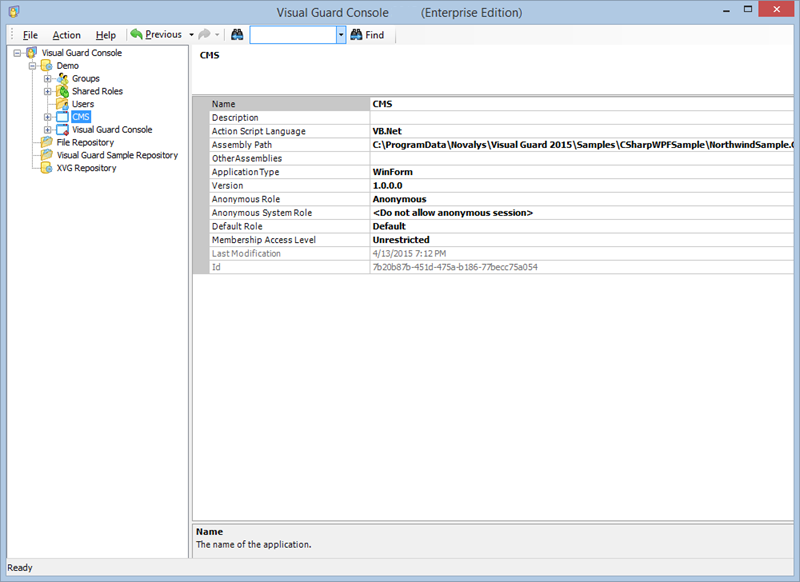
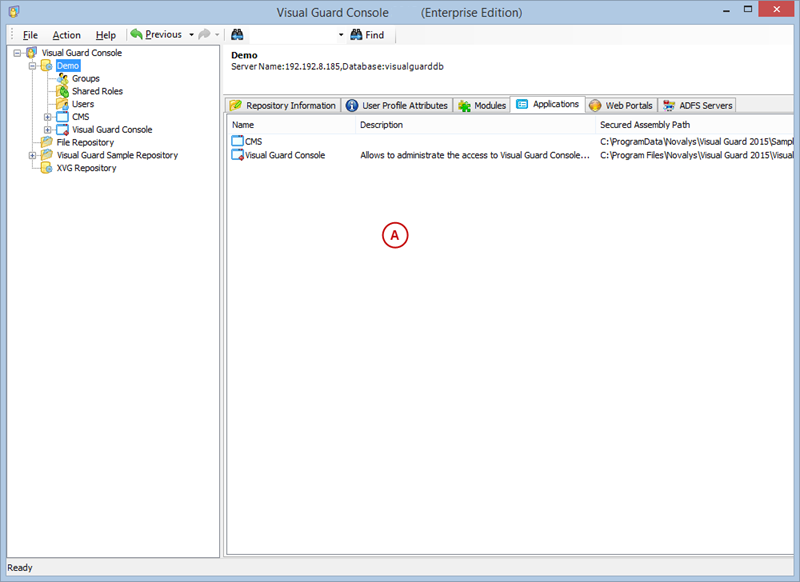
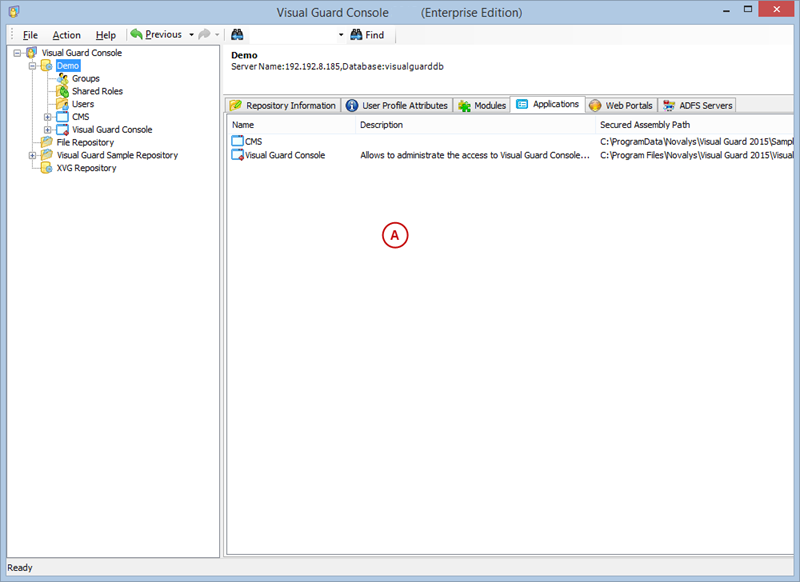
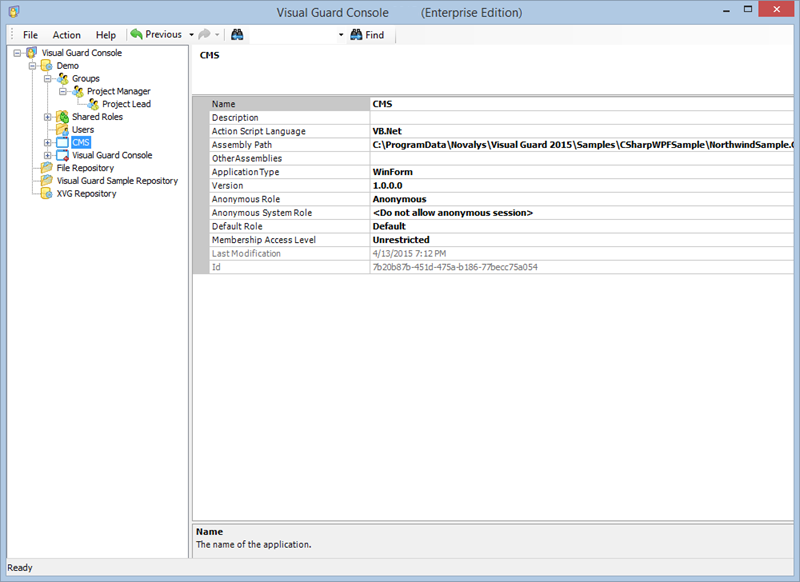
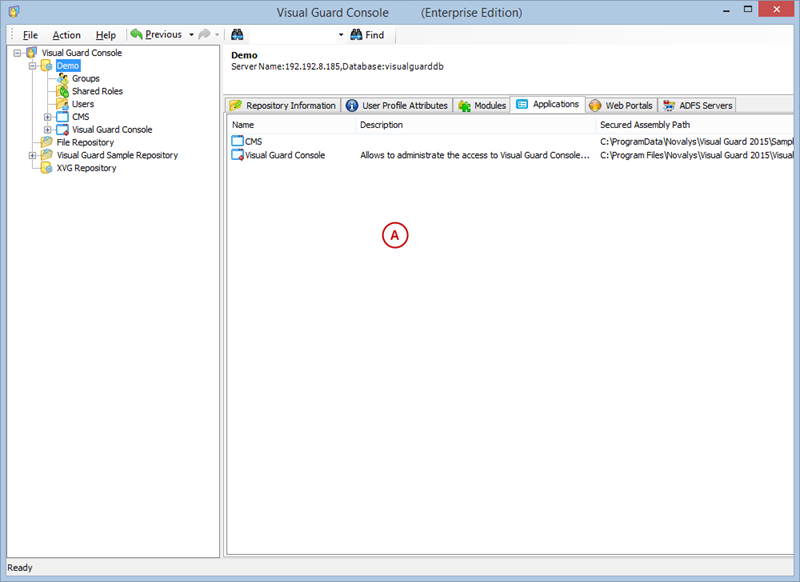
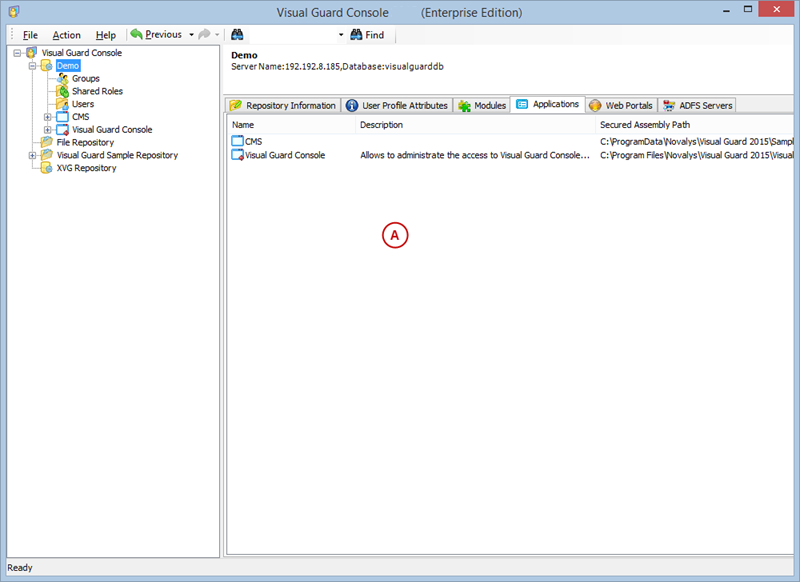
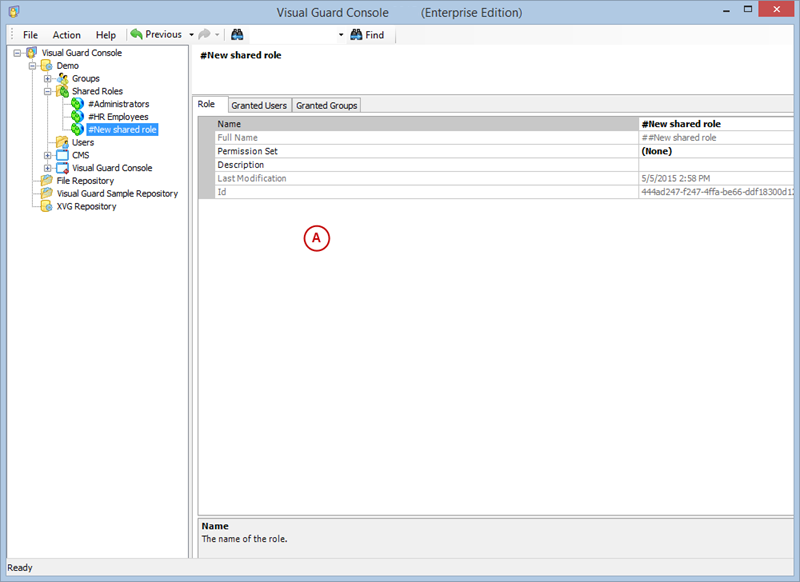
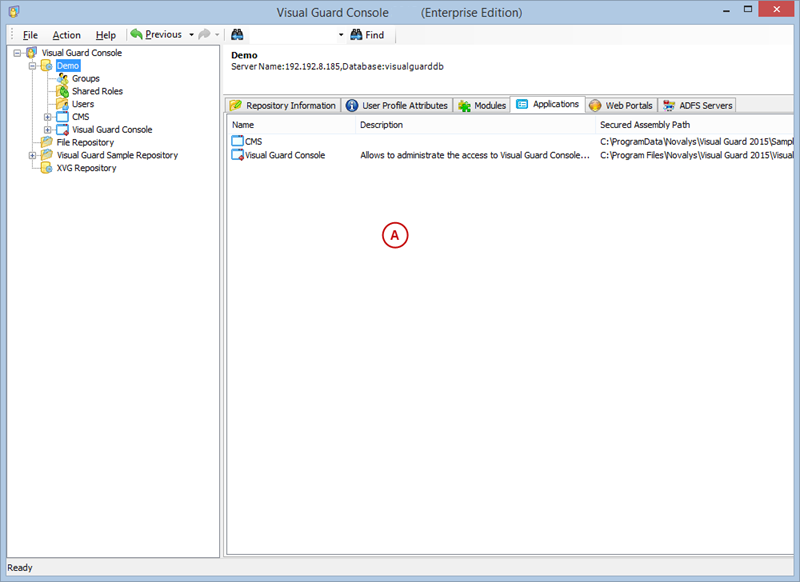
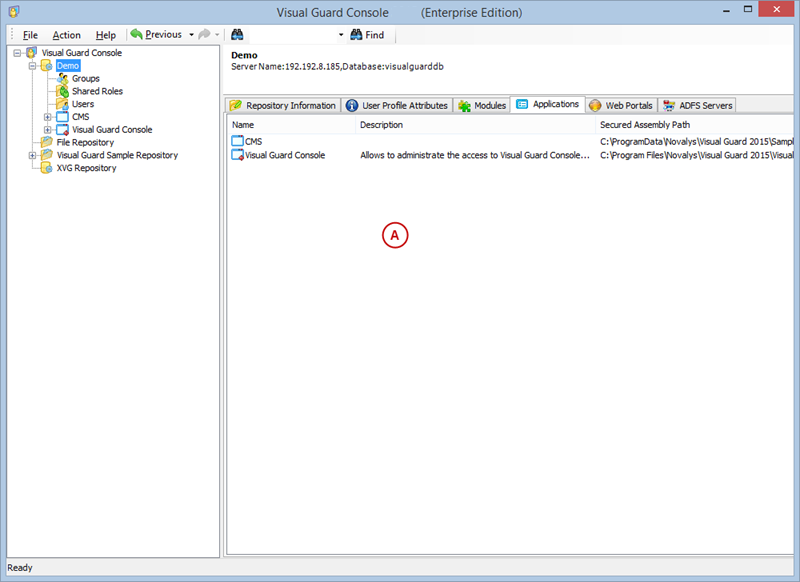
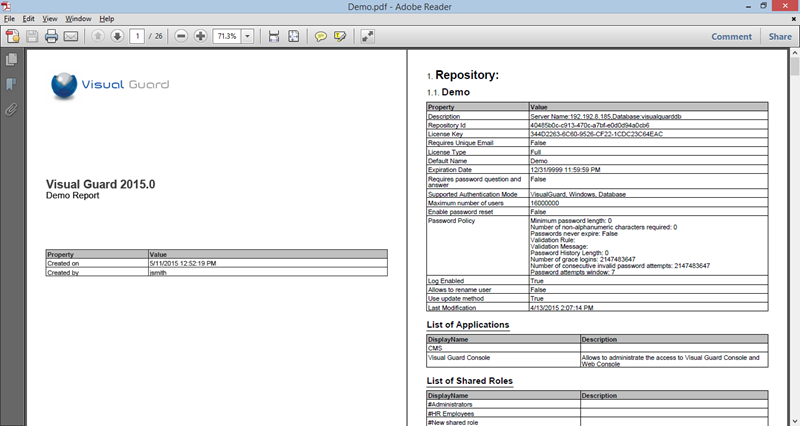
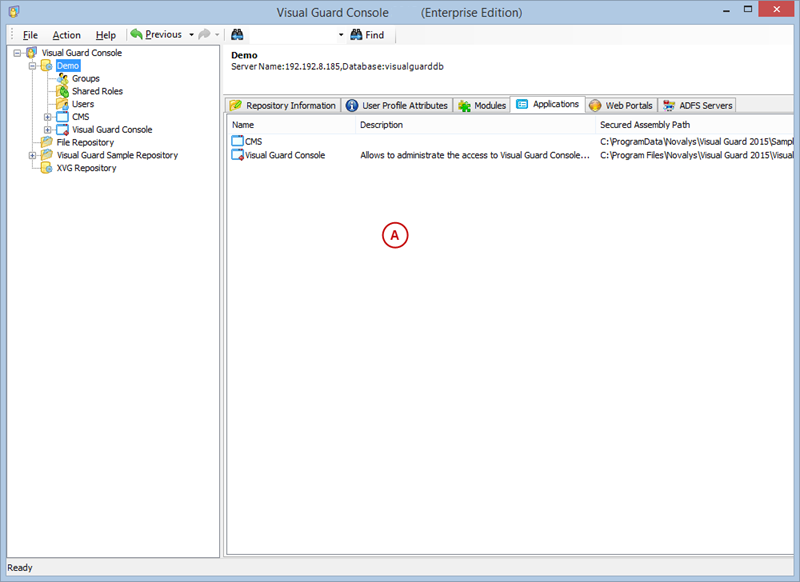
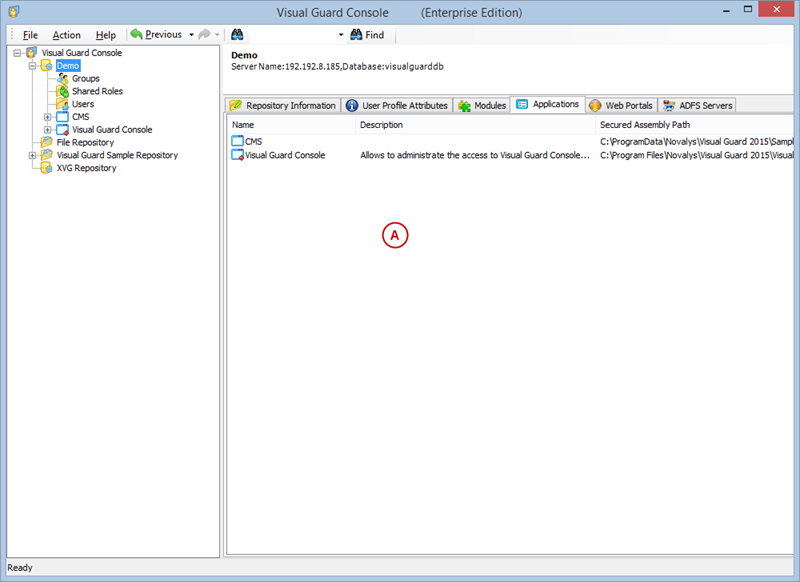
A VGRepository (Visual Guard Repository) is a centralized database for Visual Guard that stores all security-related information for your application, including user roles, permissions, groups, and other security data.
Here is a basic guide on how to create a VGRepository:
- Launch Visual Guard WinConsole or WebConsole.
- Navigate to the configuration settings.
- Create a new VGRepository that will store all your configurations.
- Save your settings and exit.
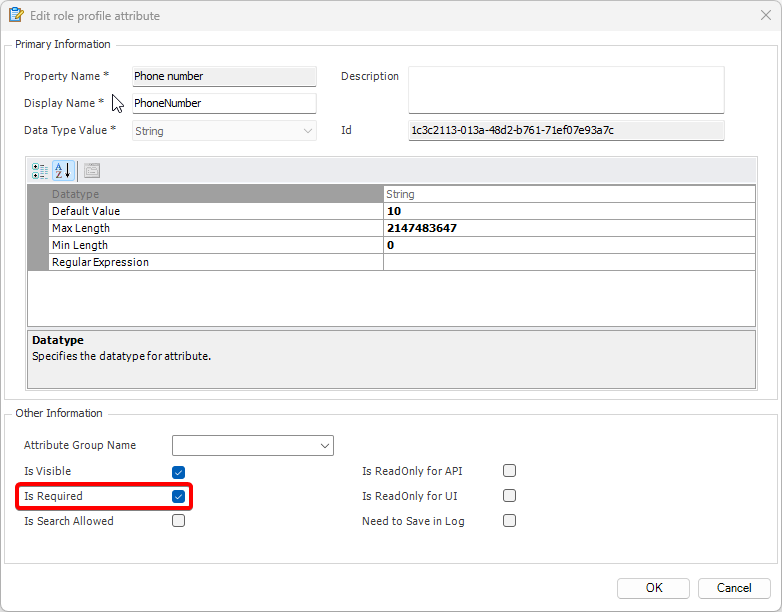
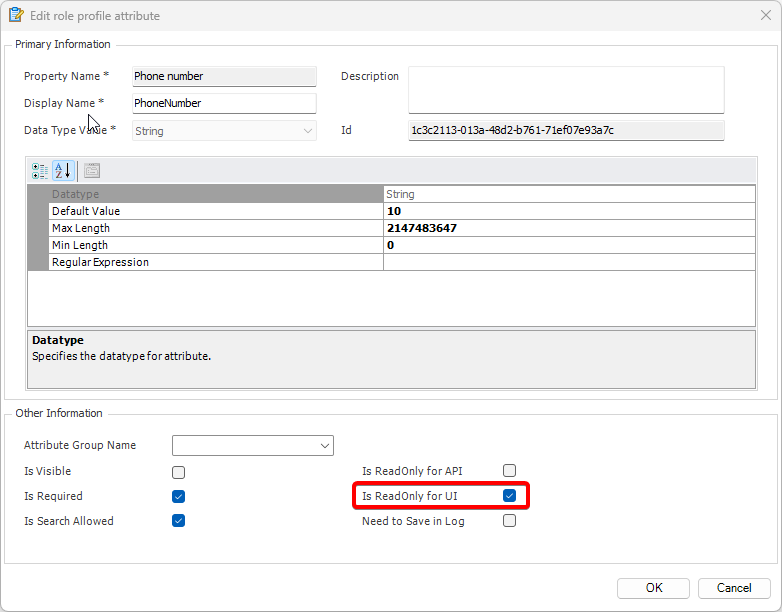
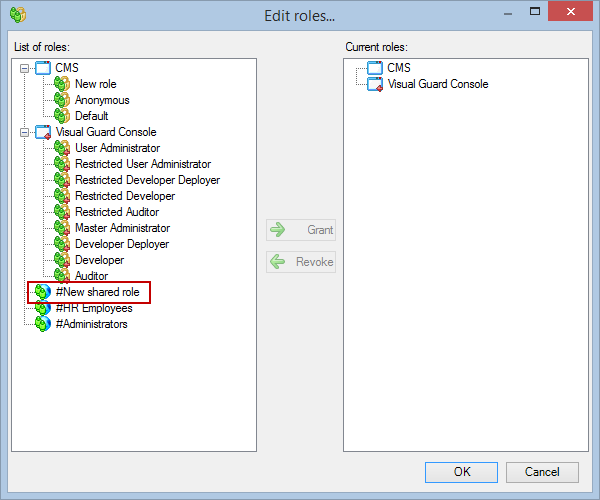
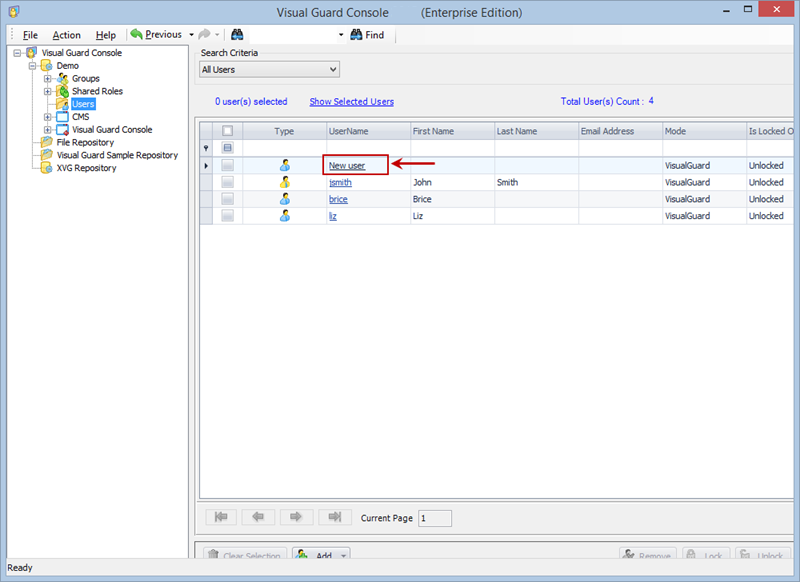
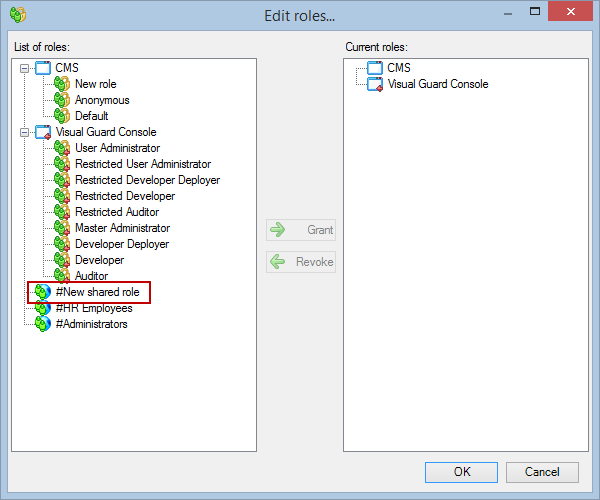
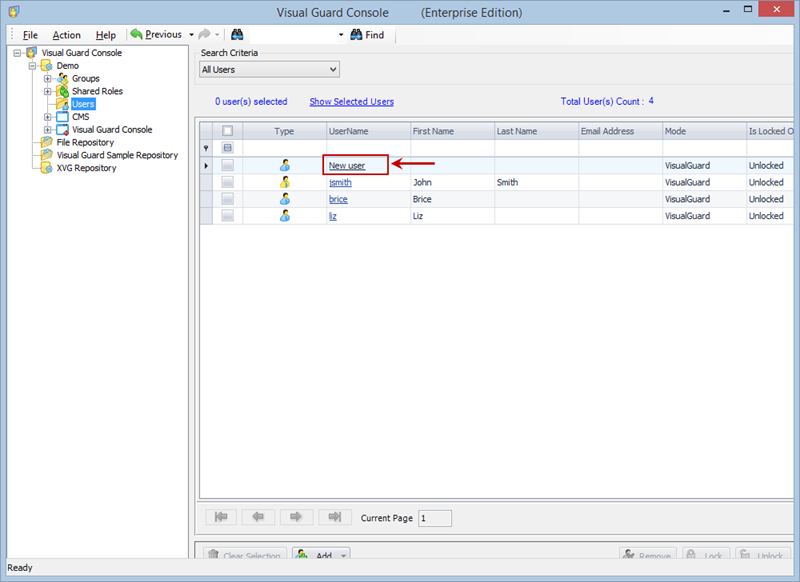
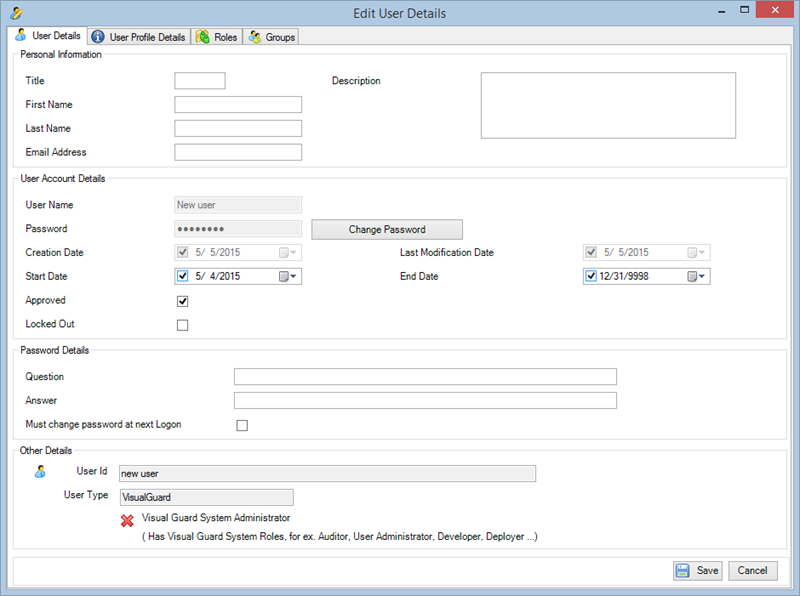
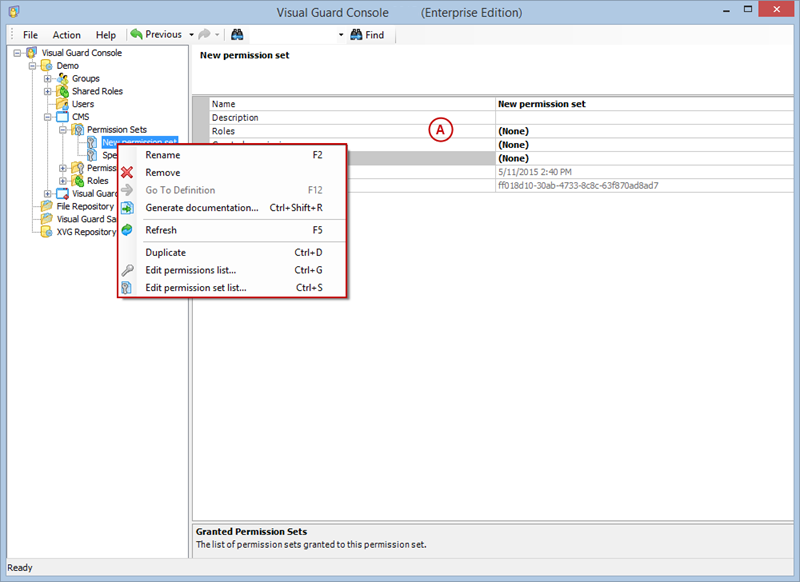
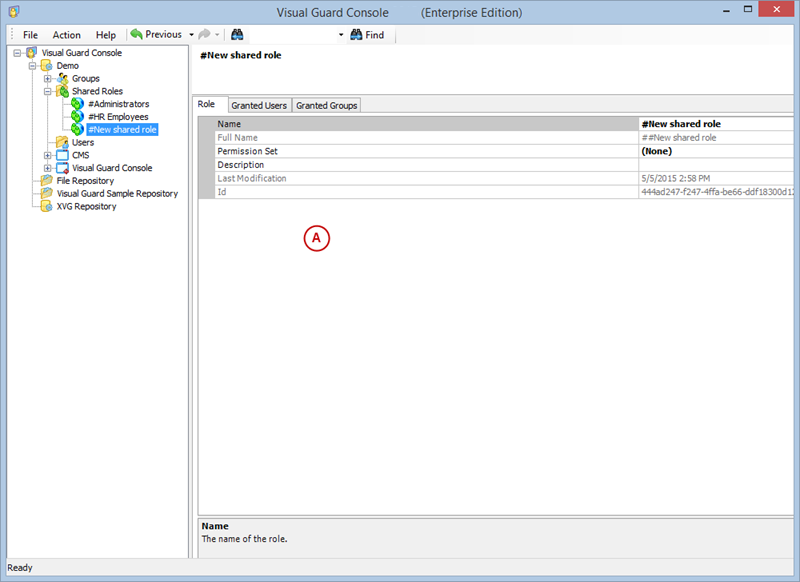
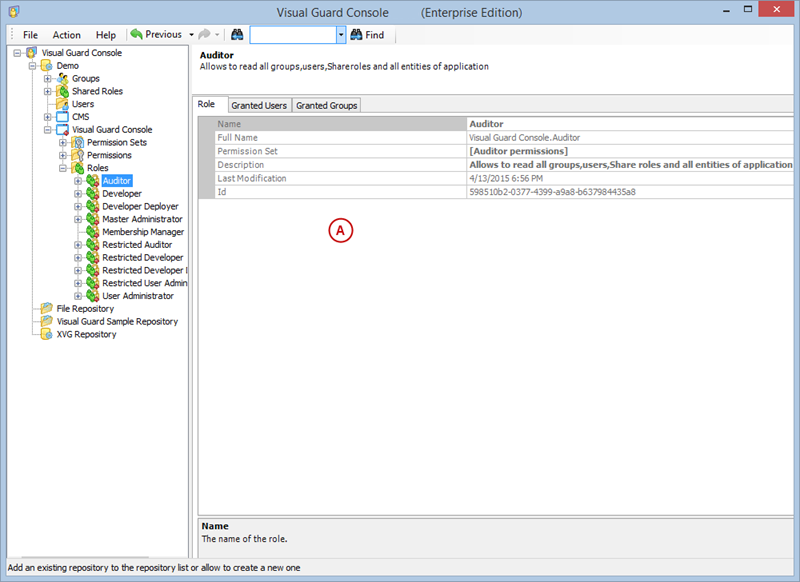
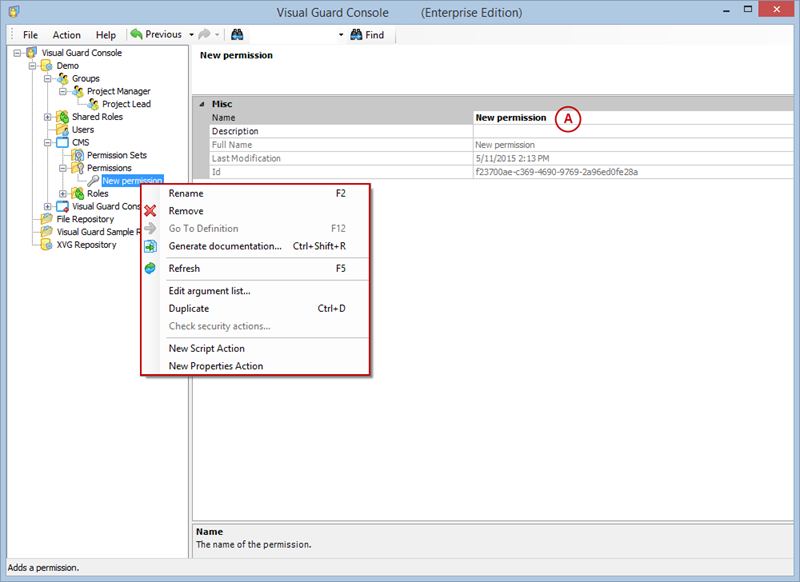
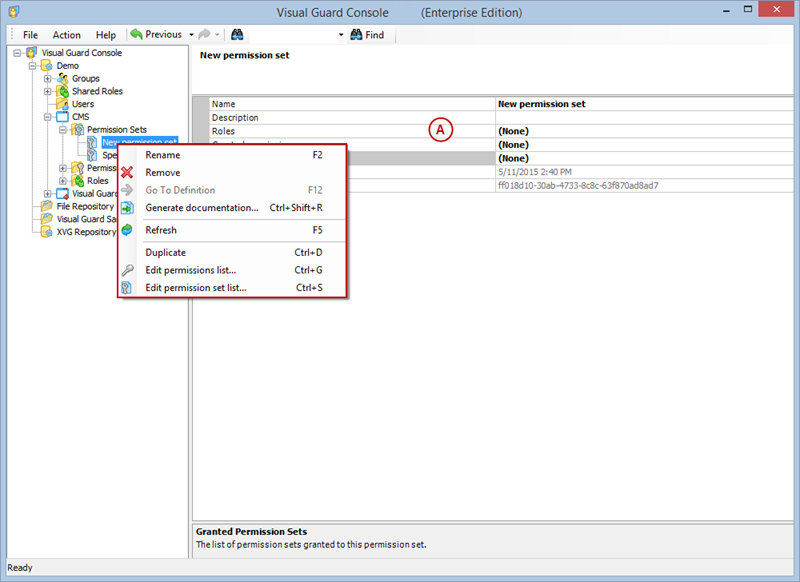
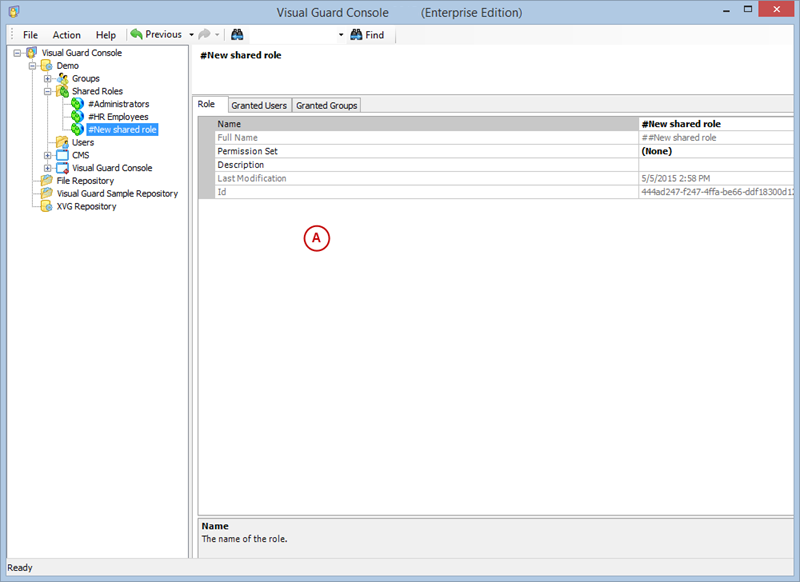
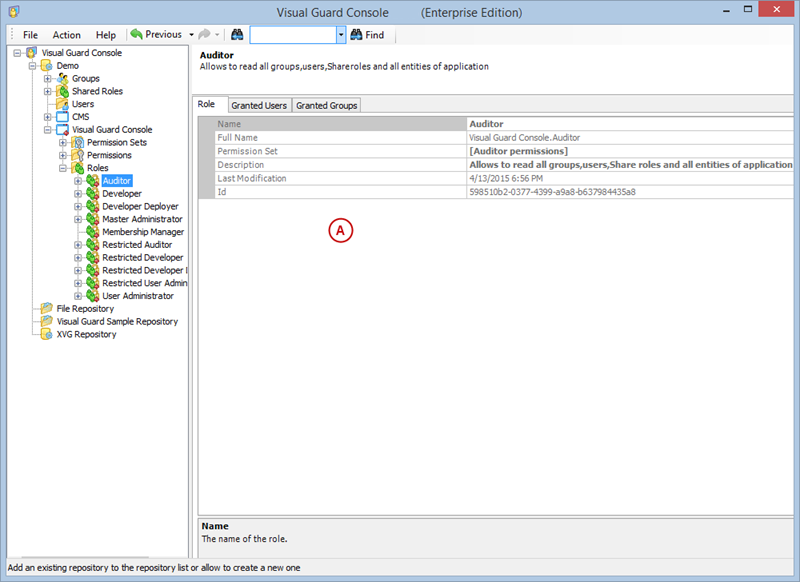
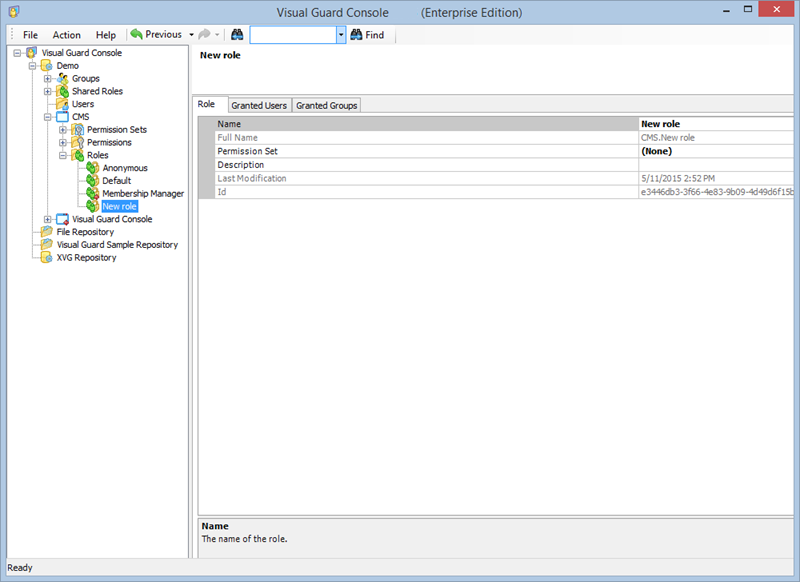
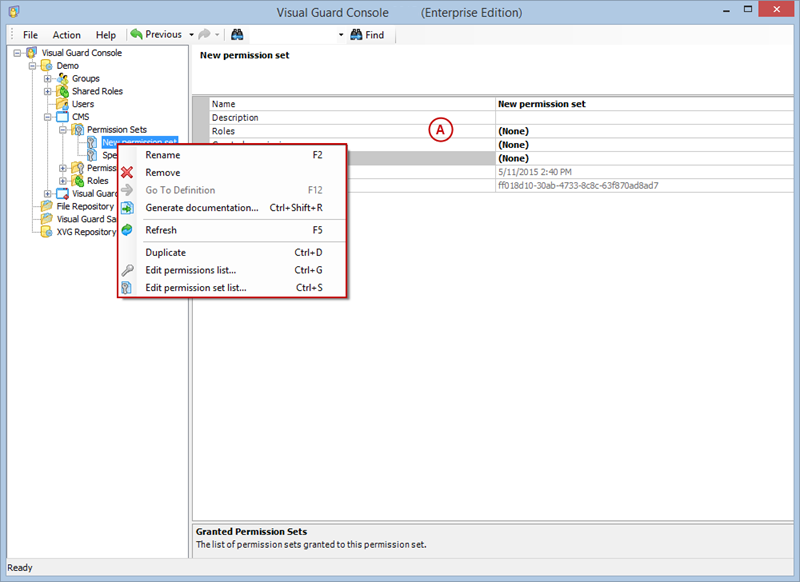
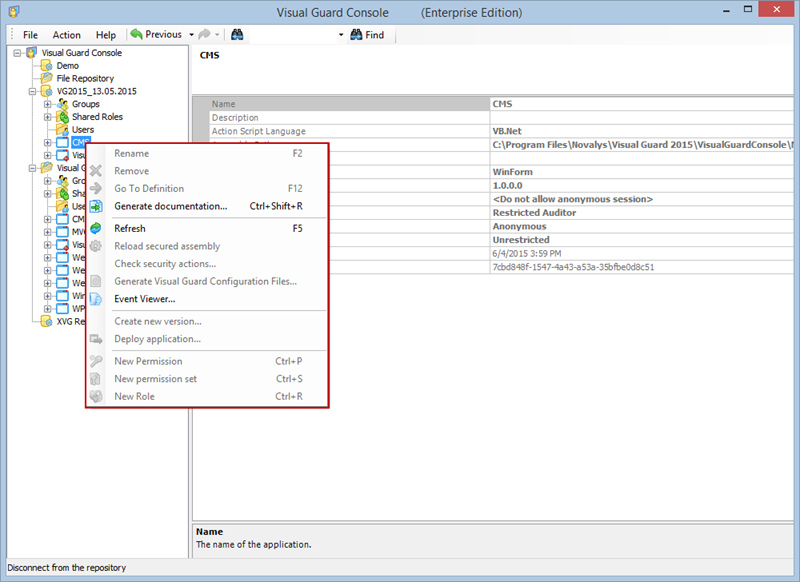
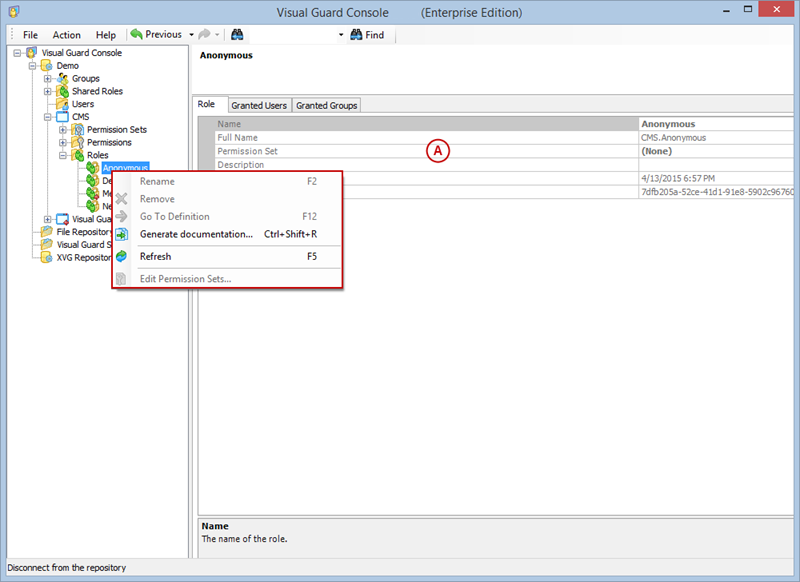
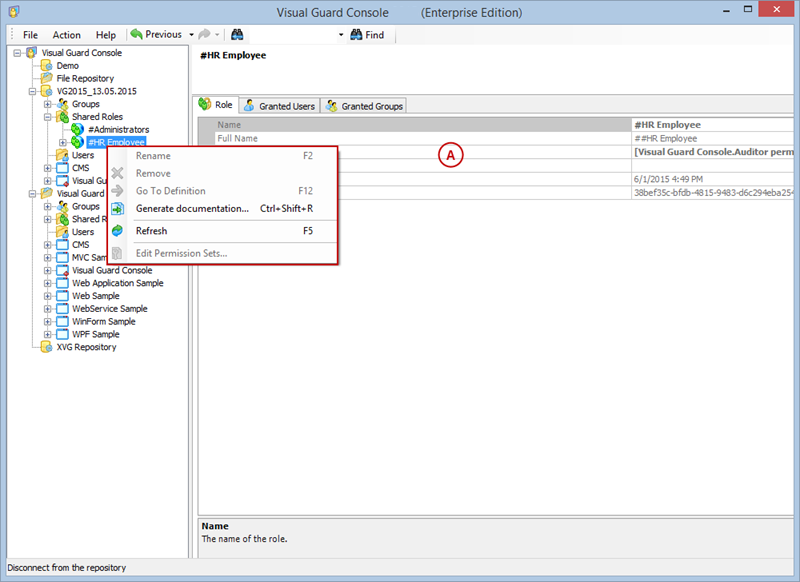
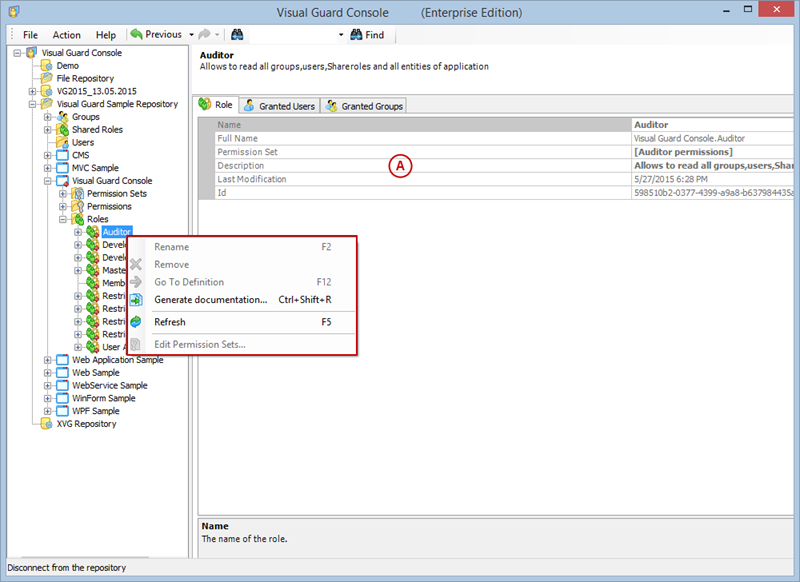
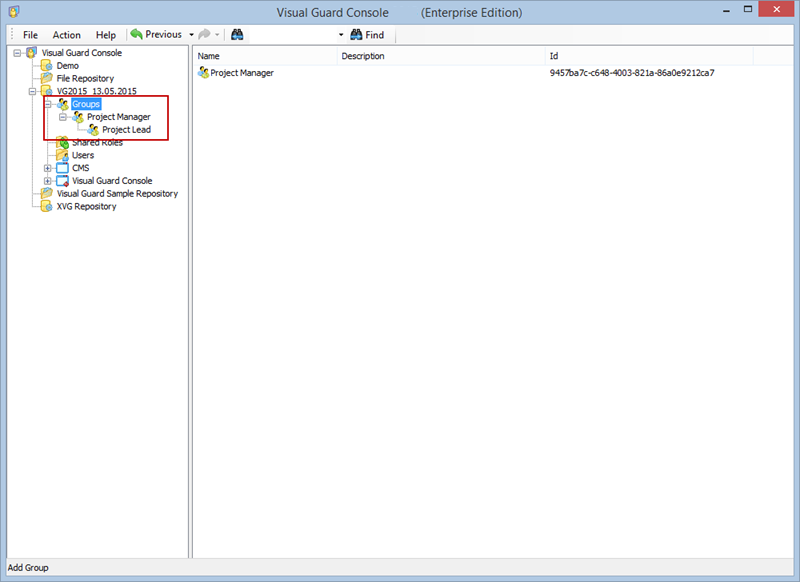
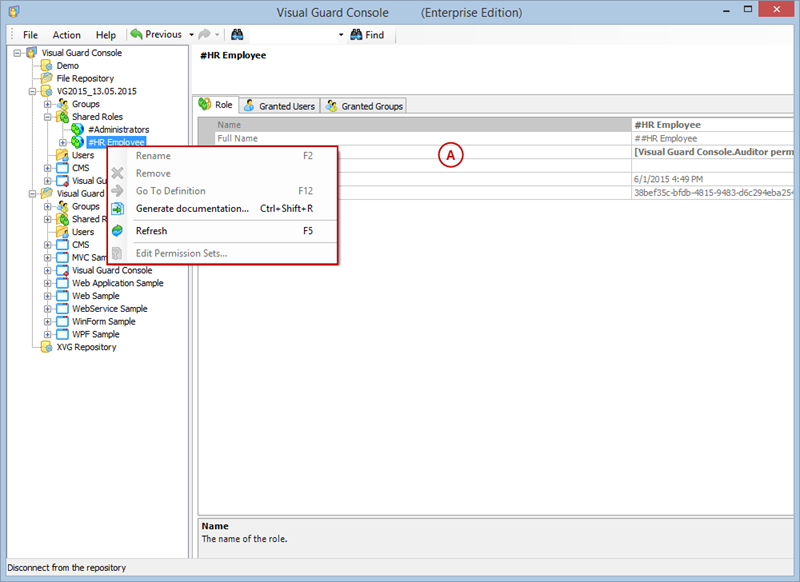
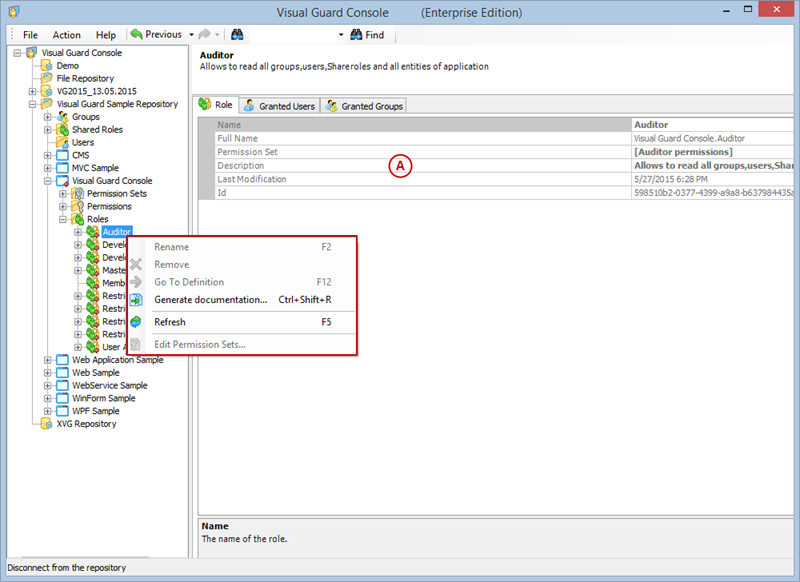
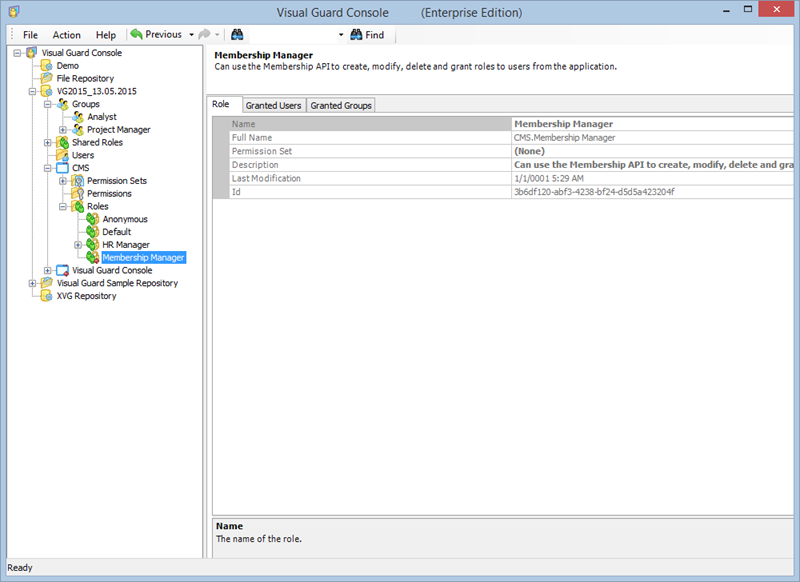
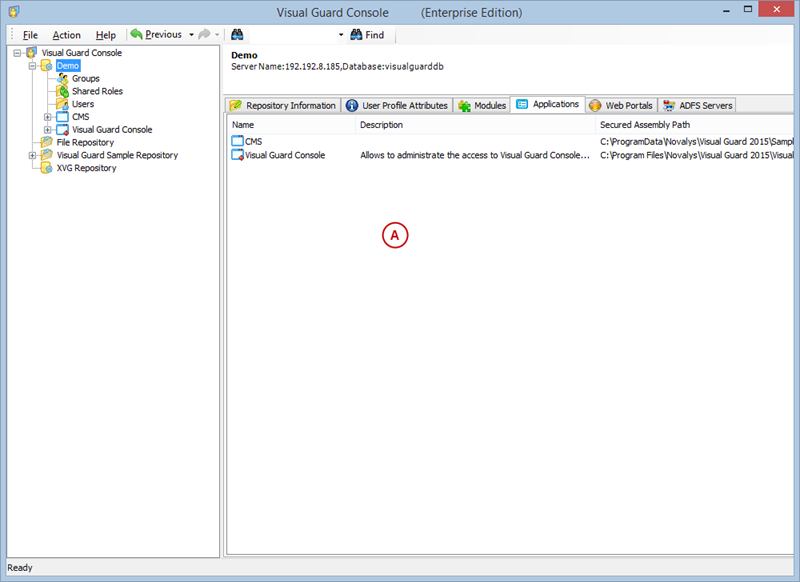
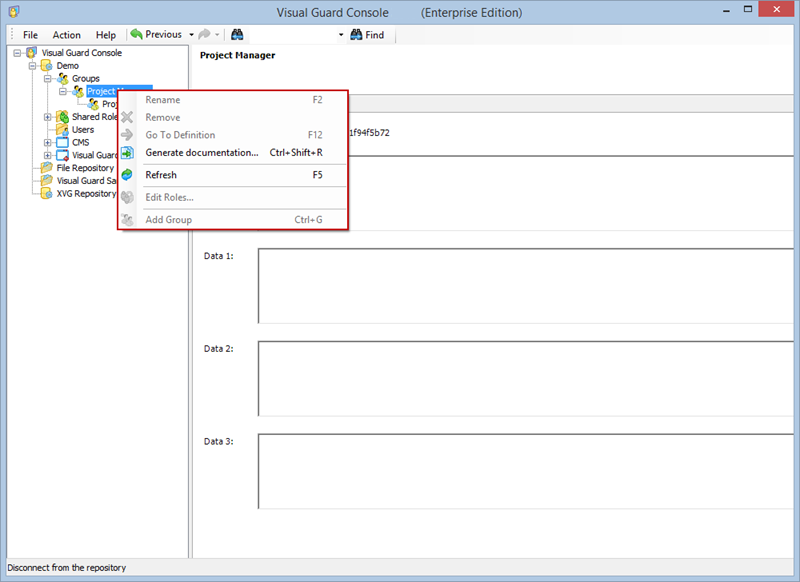
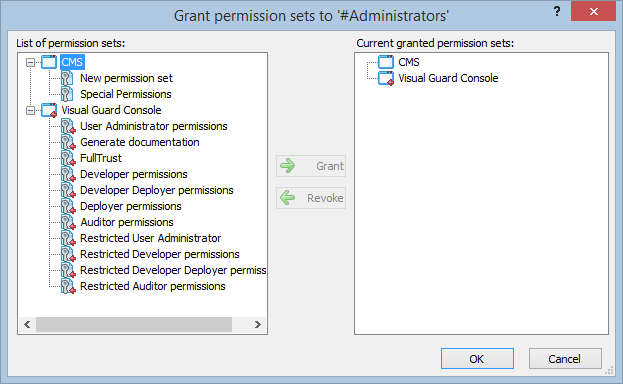
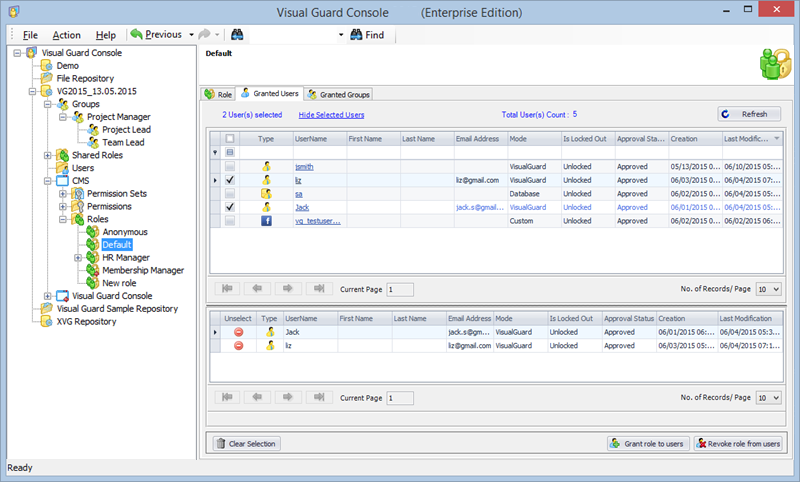
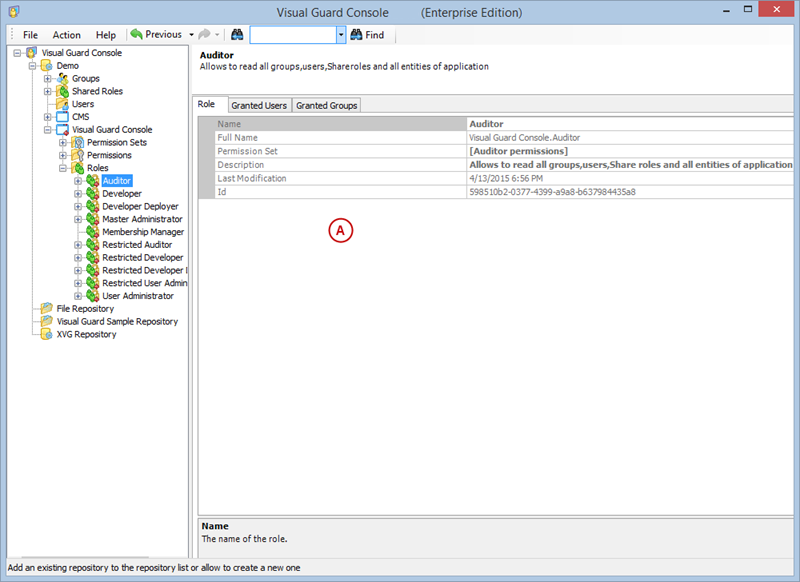
Setting User Roles, Permissions and Groups
Once the VGRepository is set up, you can proceed with setting up user roles, assigning permissions to these roles, and creating groups to manage multiple roles and users:
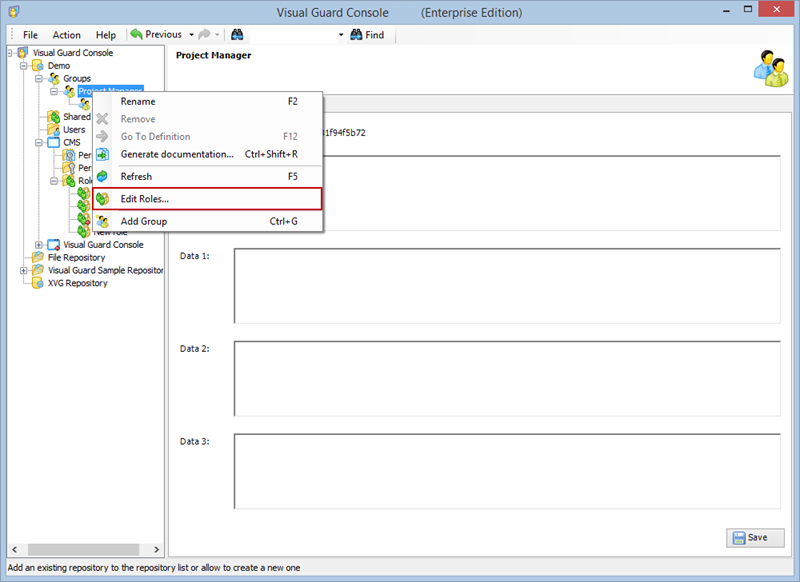
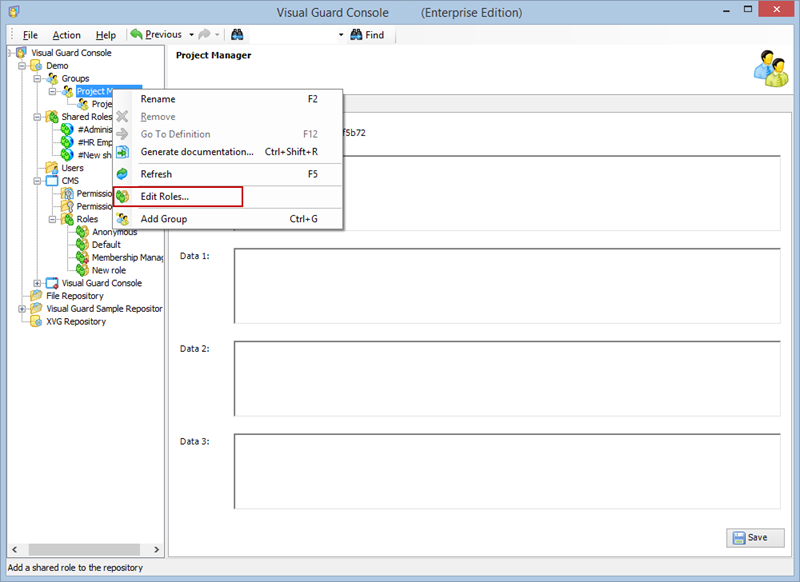
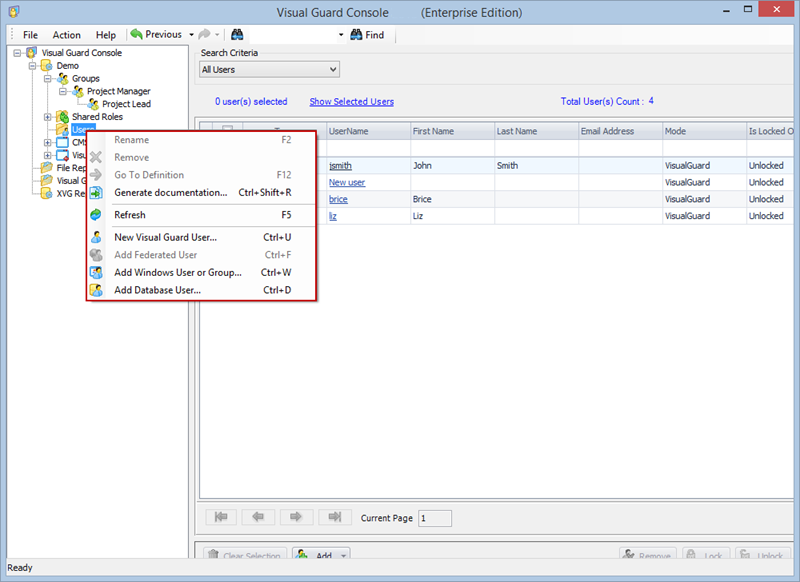
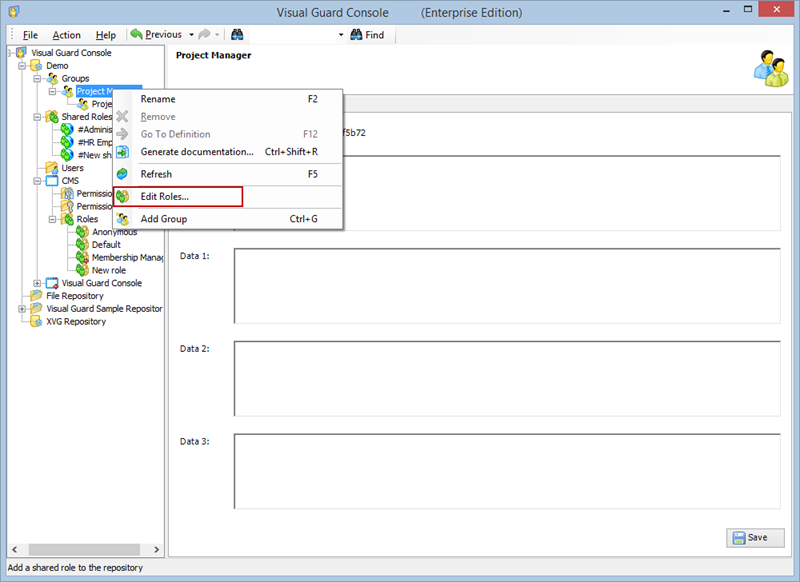
- Open Visual Guard WinConsole or WebConsole.
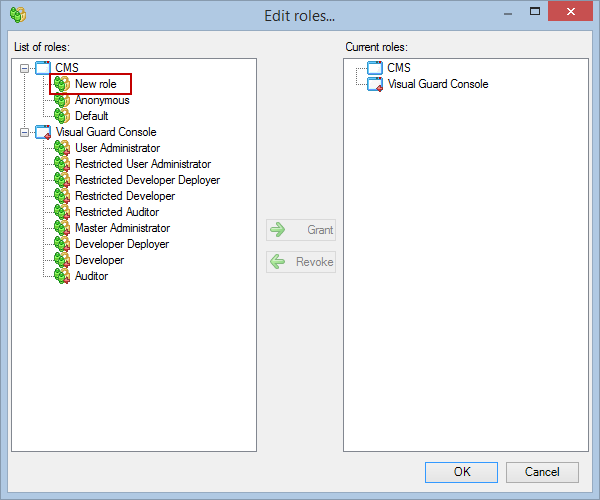
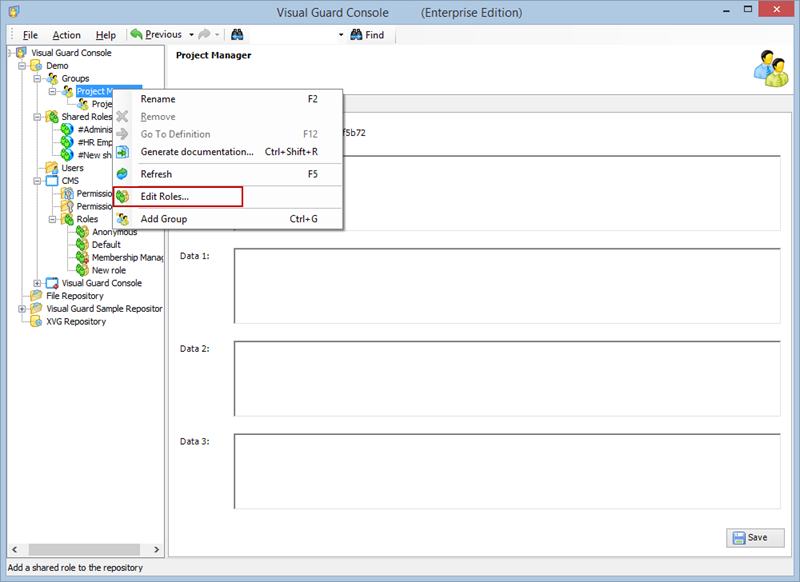
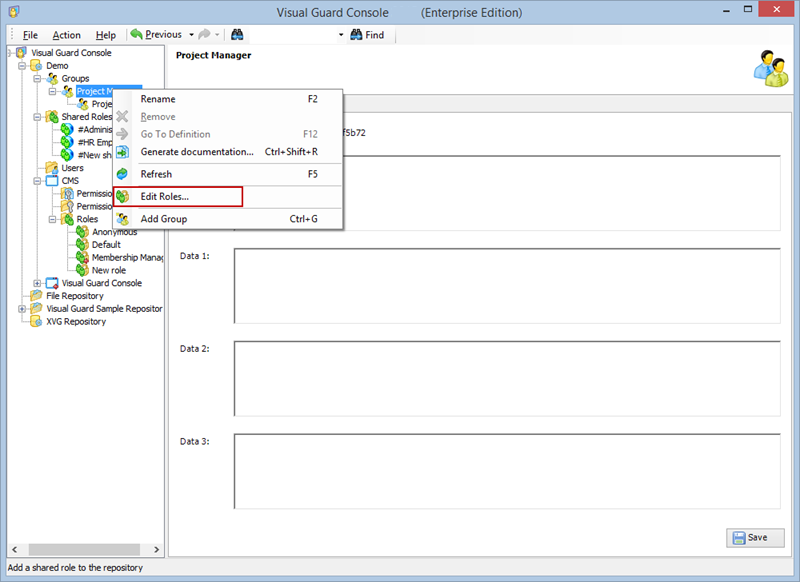
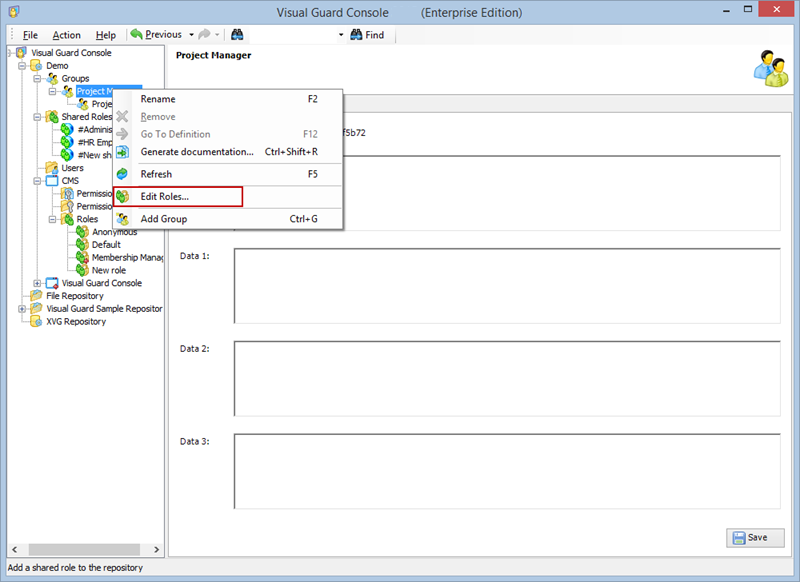
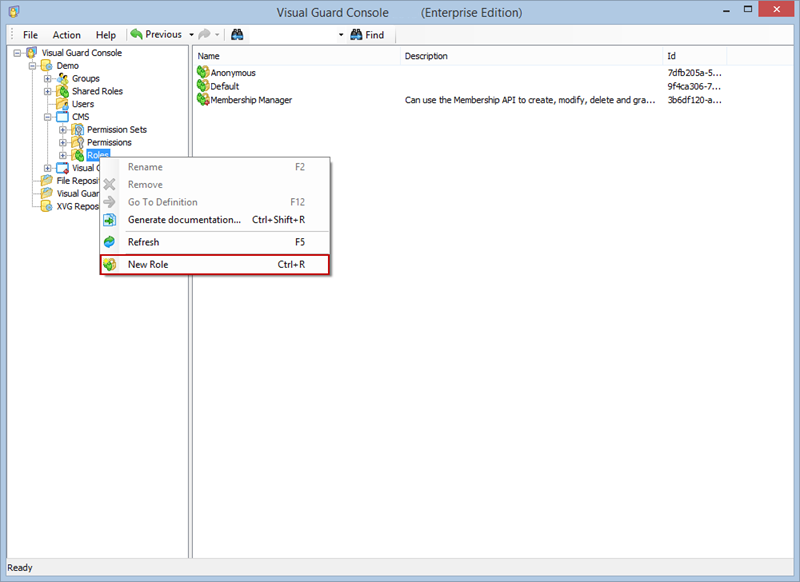
- Navigate to the user roles section.
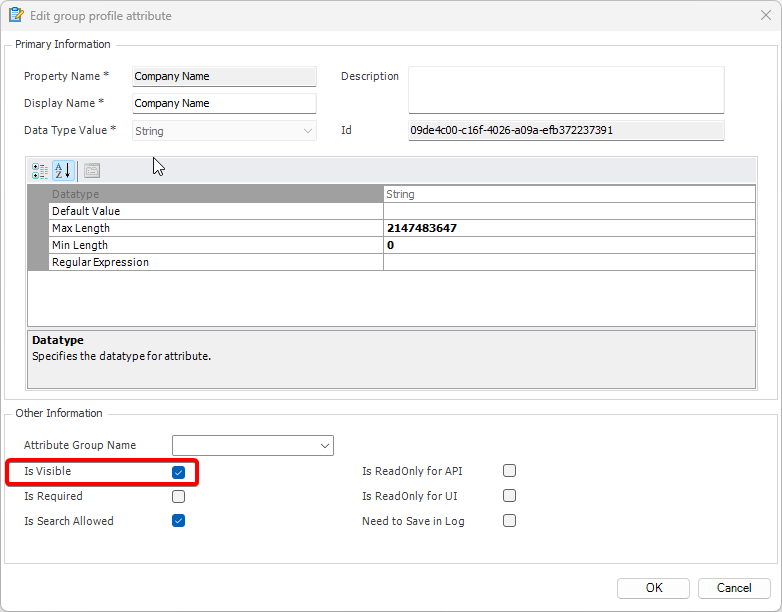
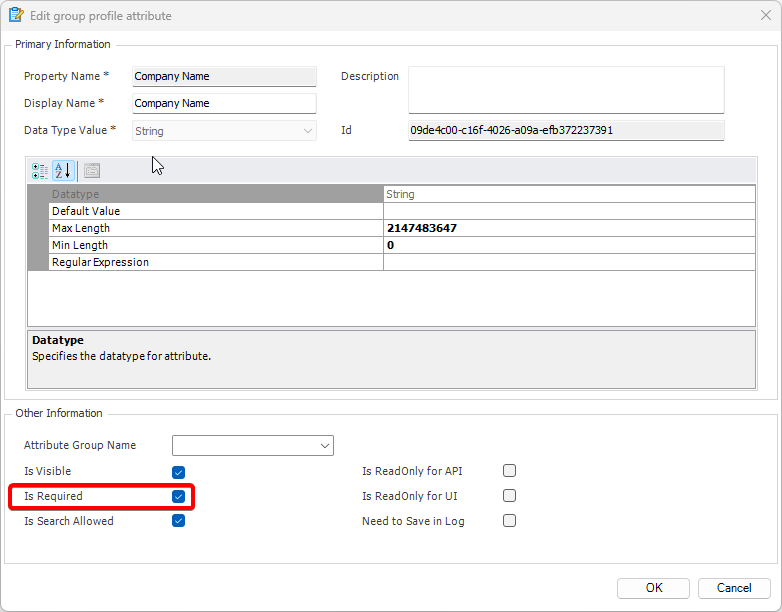
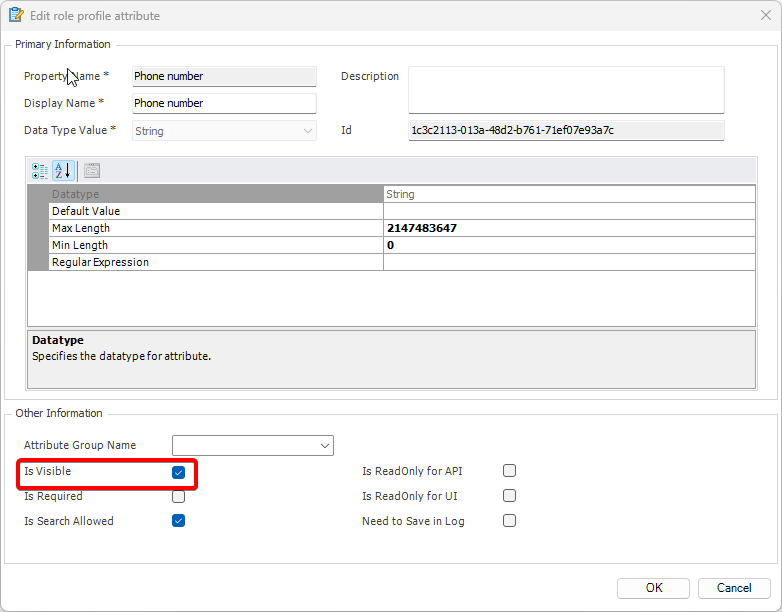
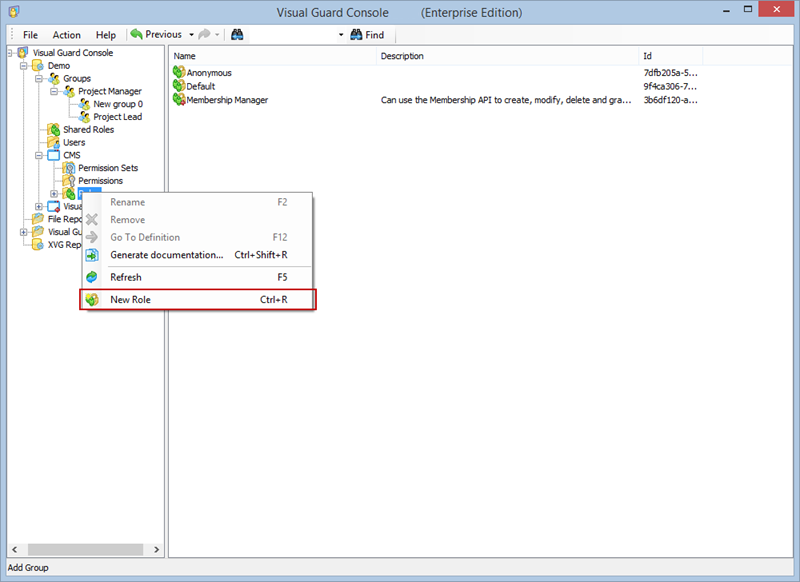
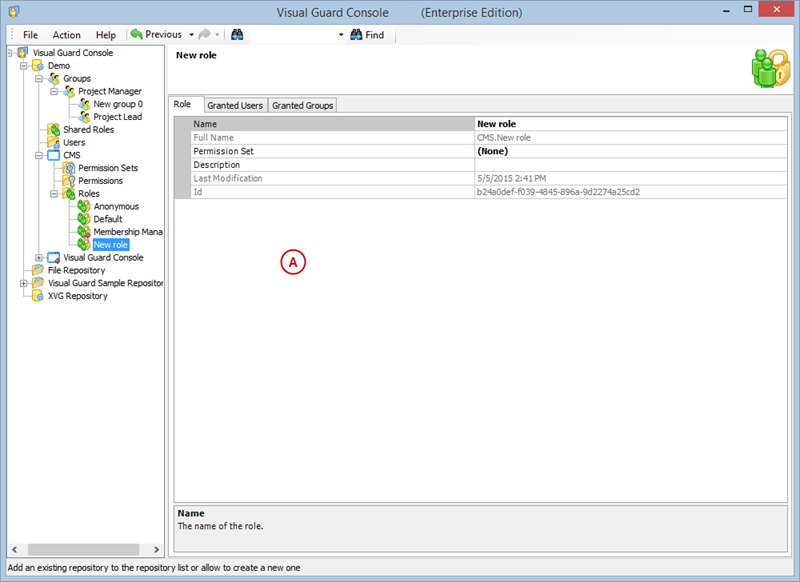
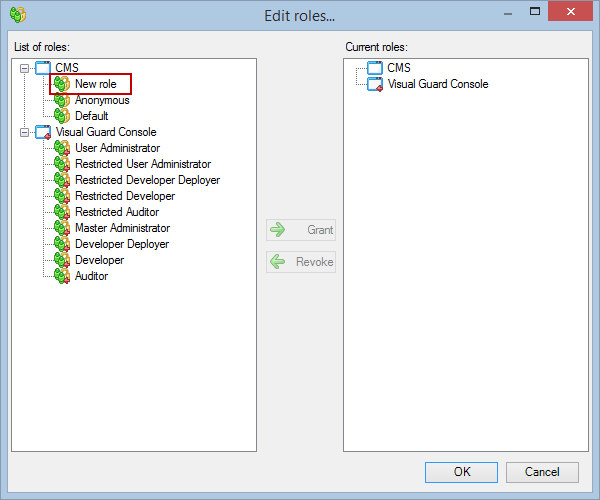
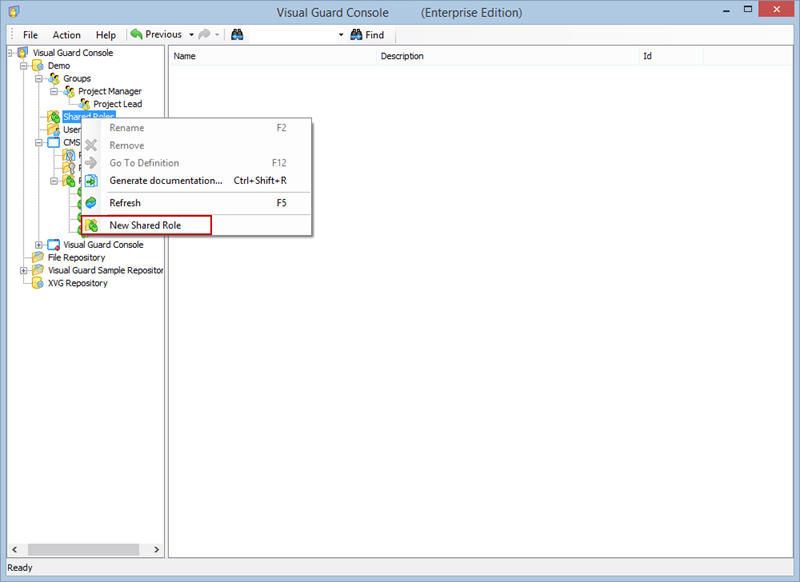
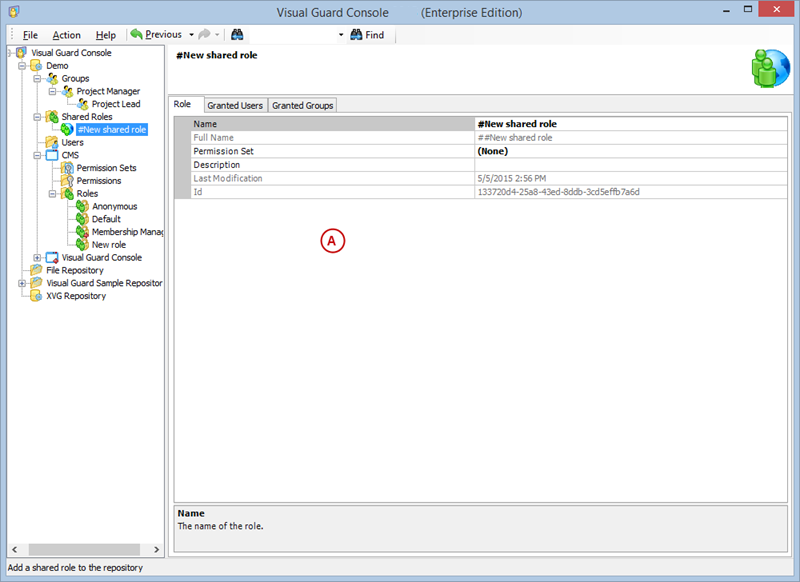
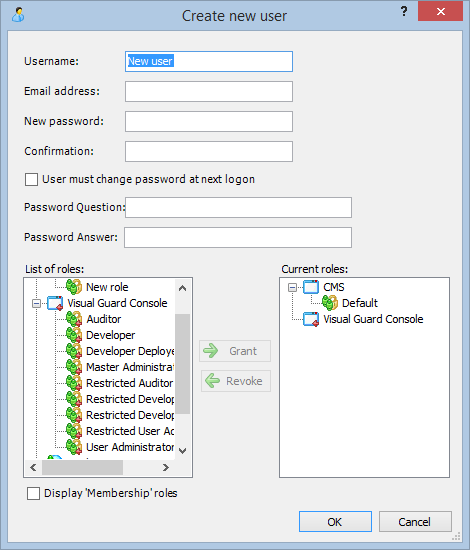
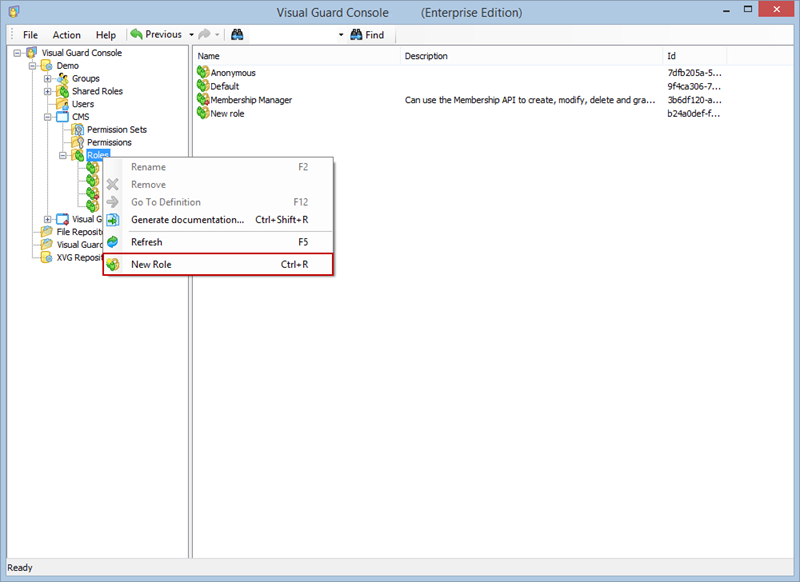
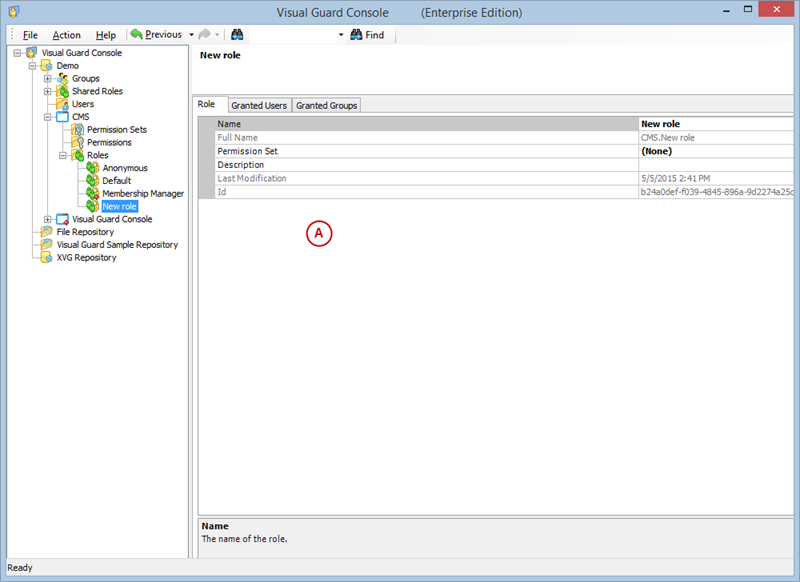
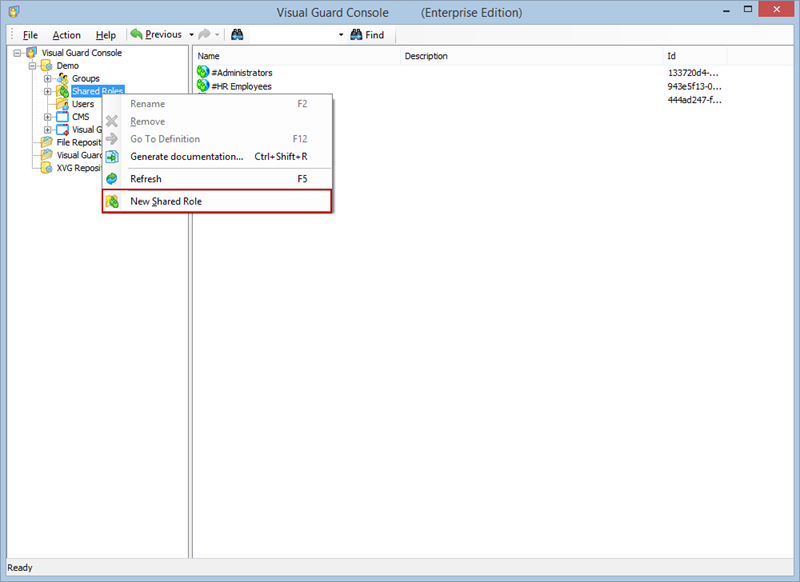
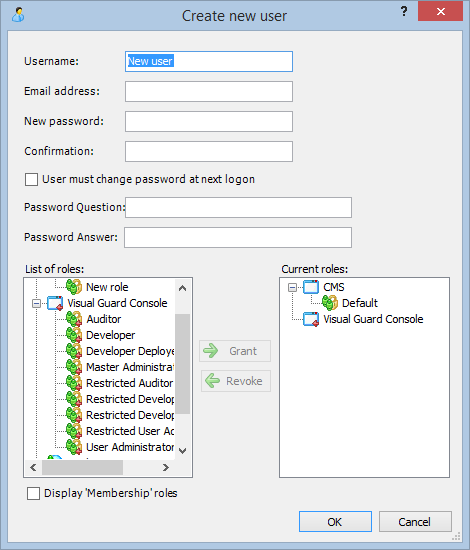
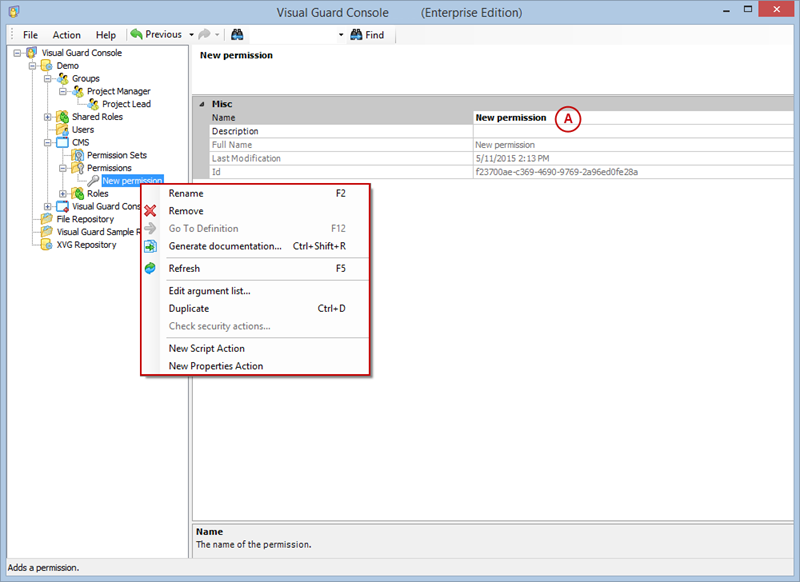
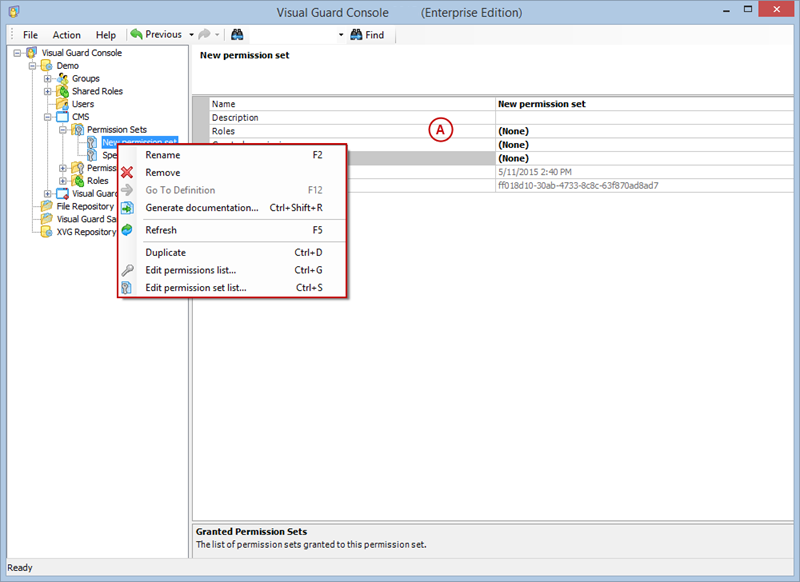
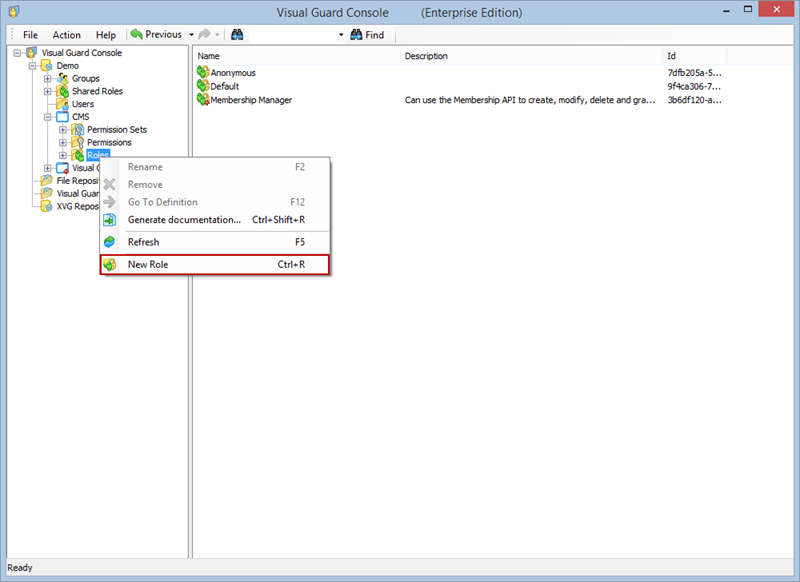
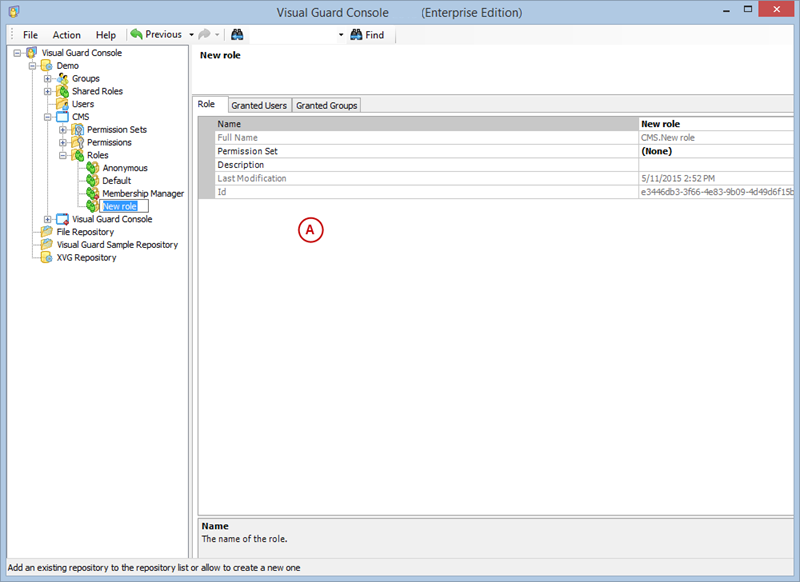
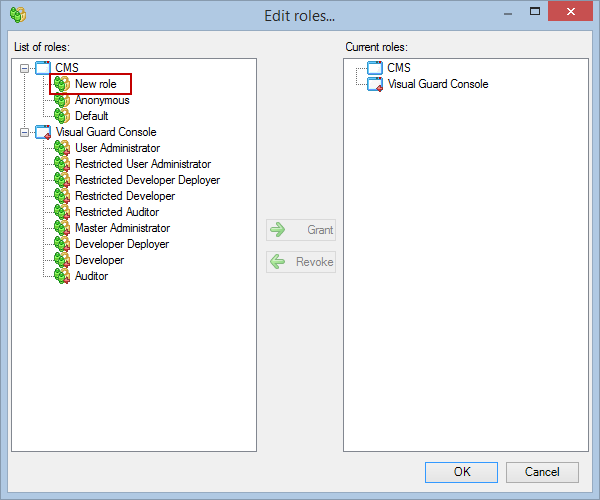
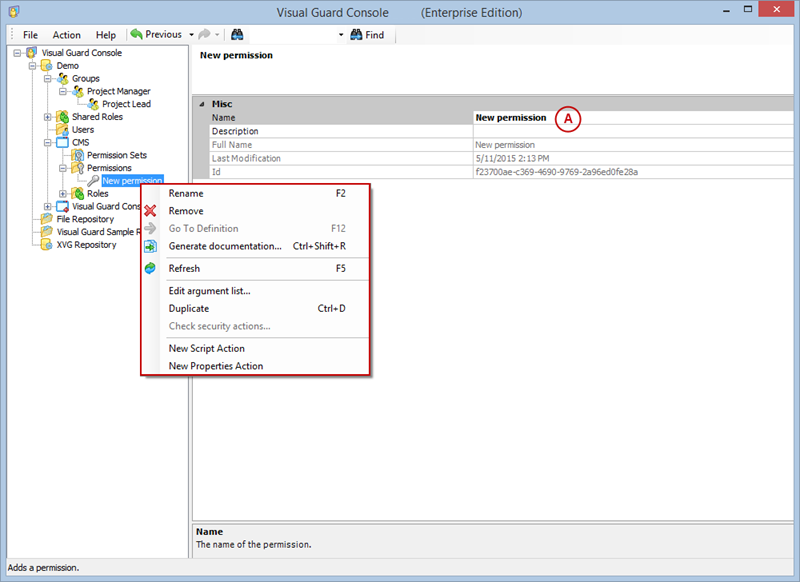
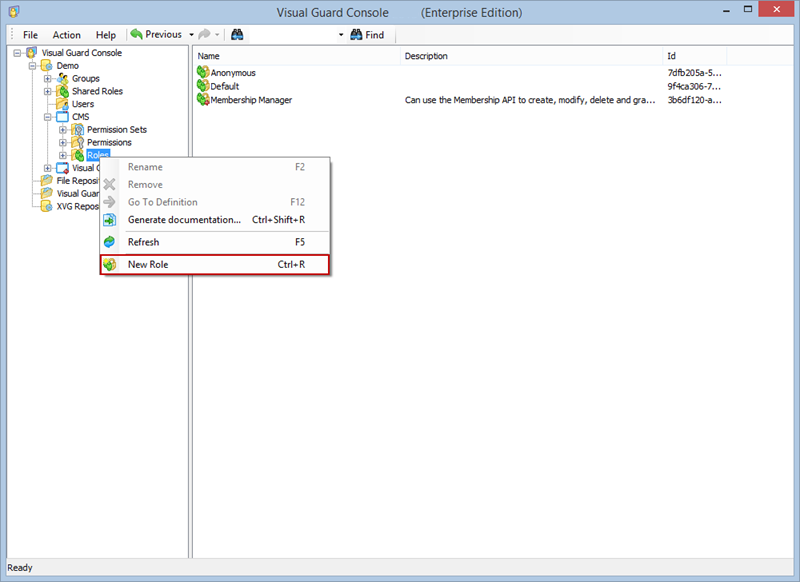
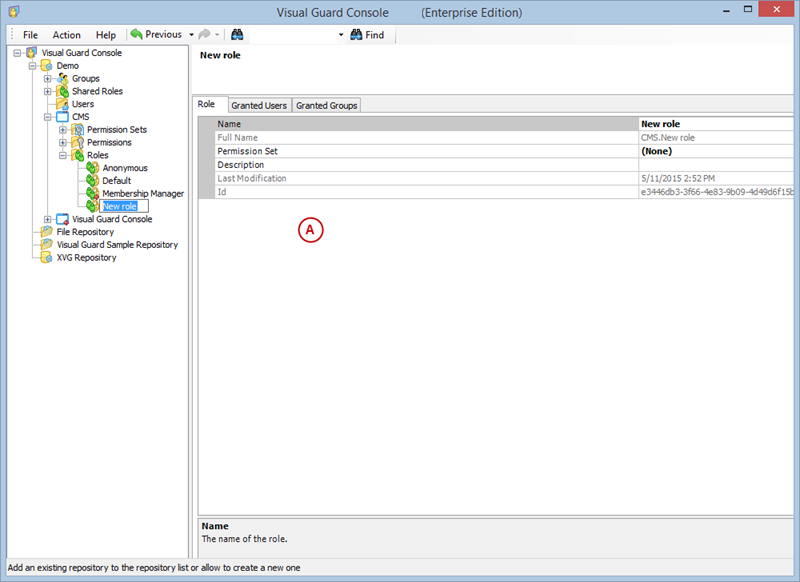
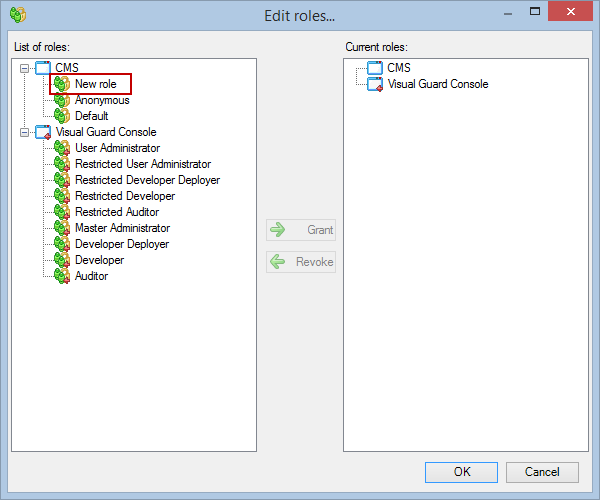
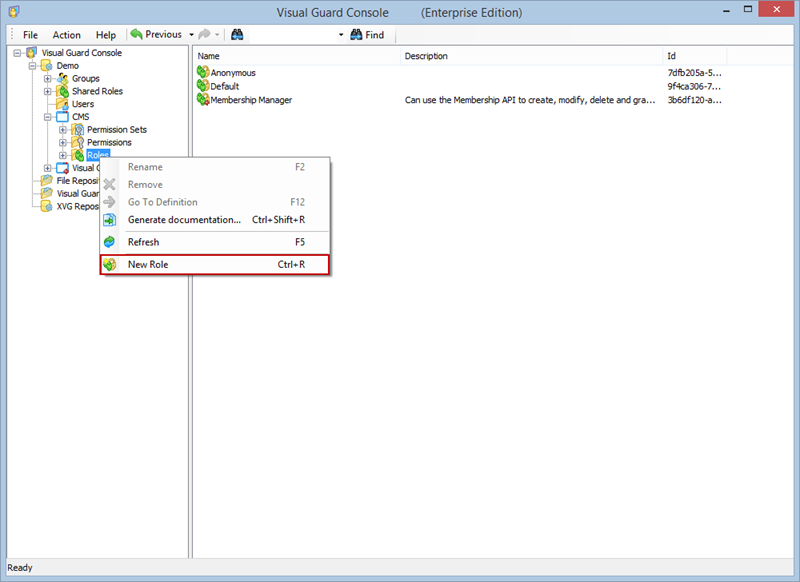
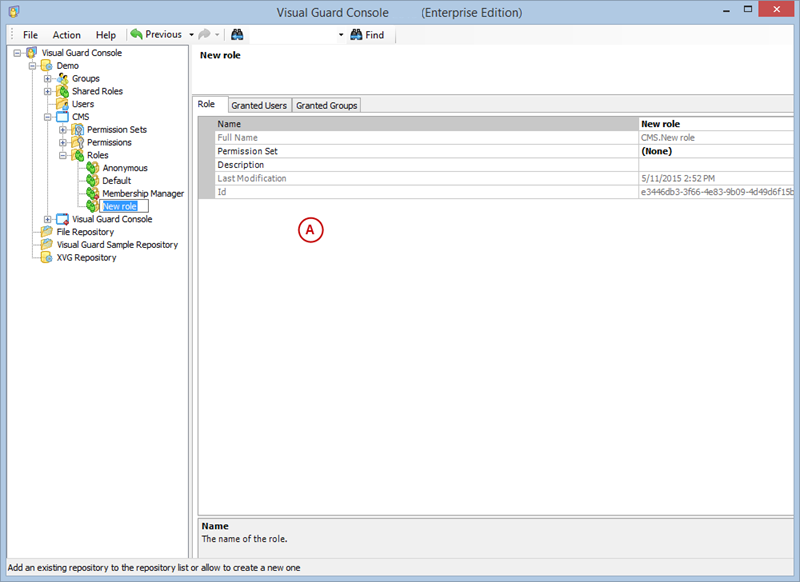
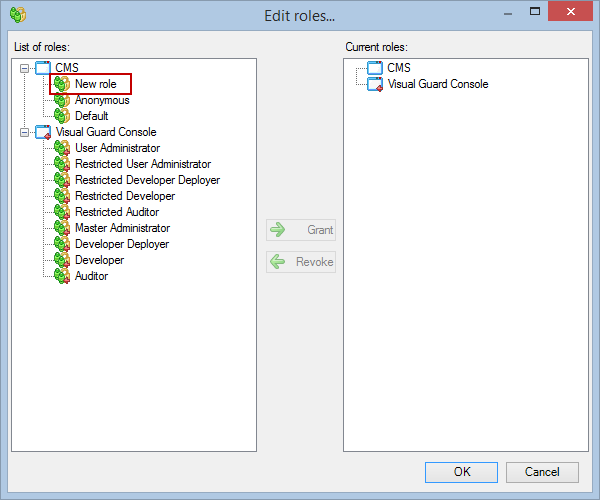
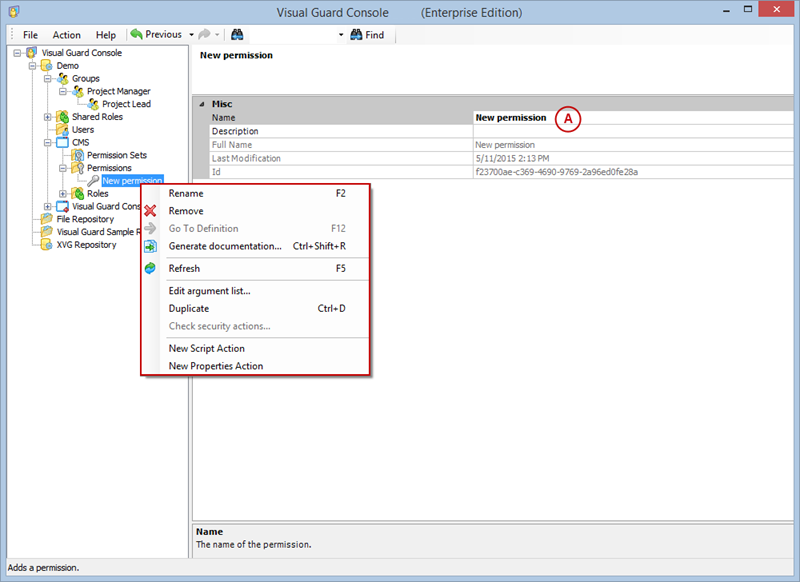
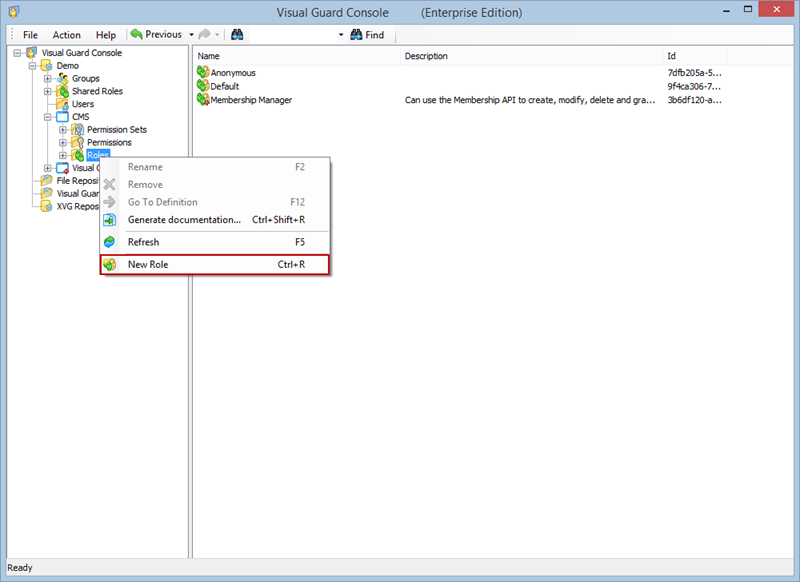
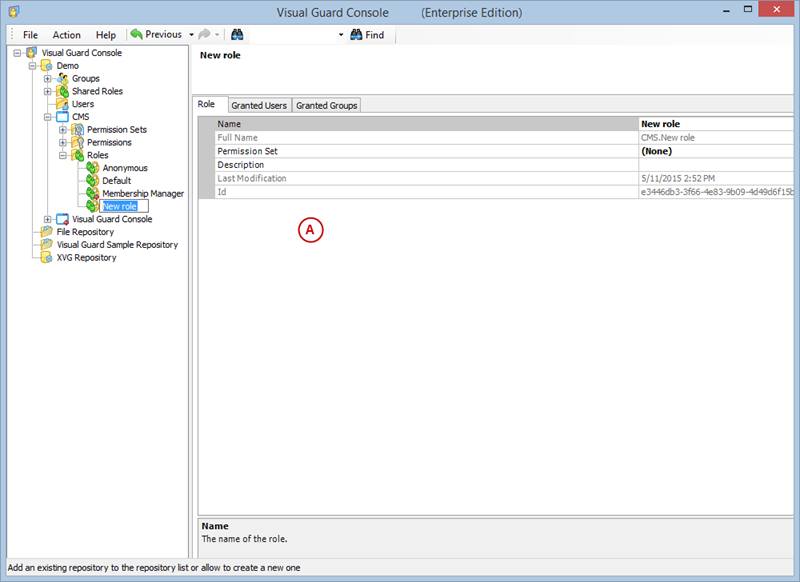
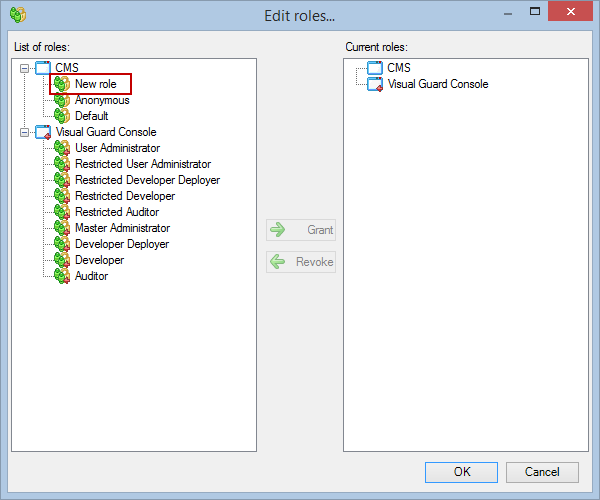
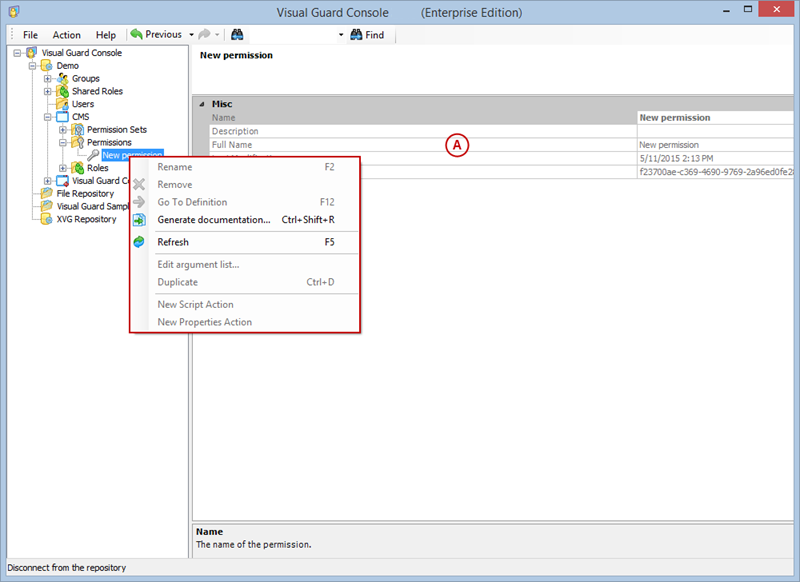
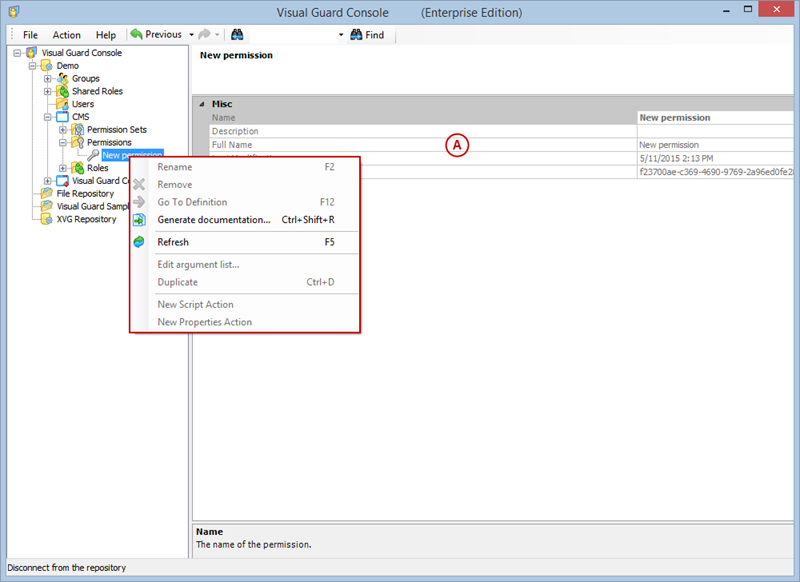
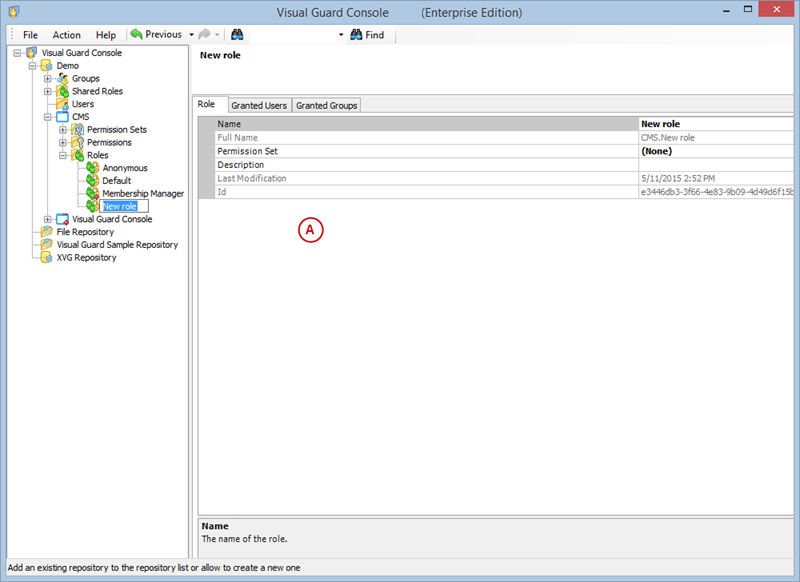
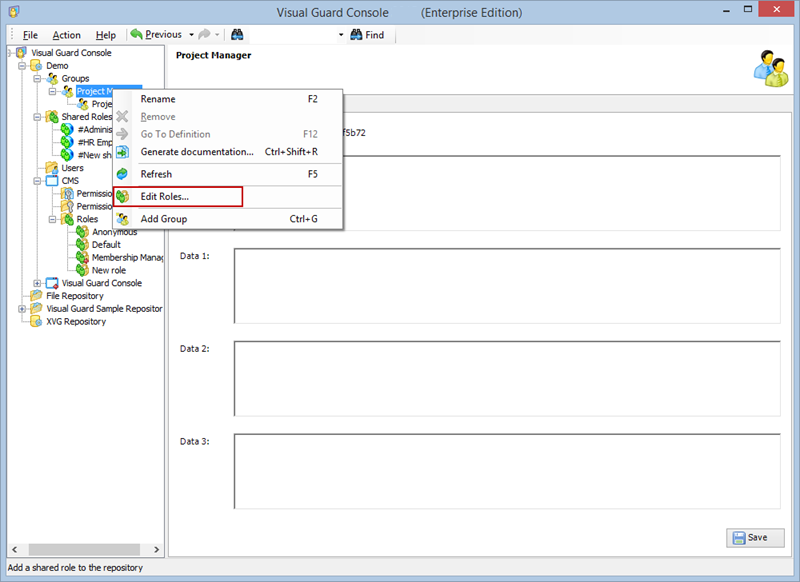
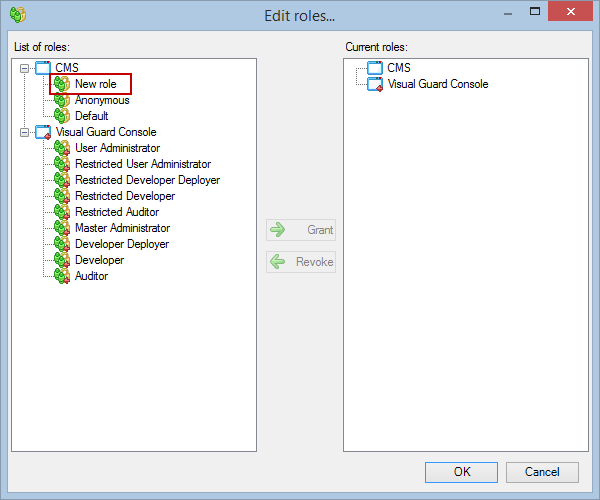
- Click on ‘Add new role’ and name the role.
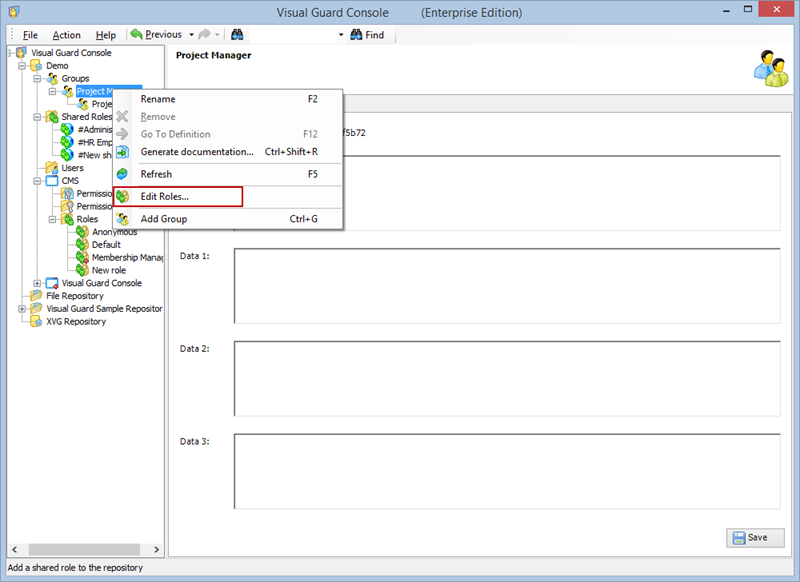
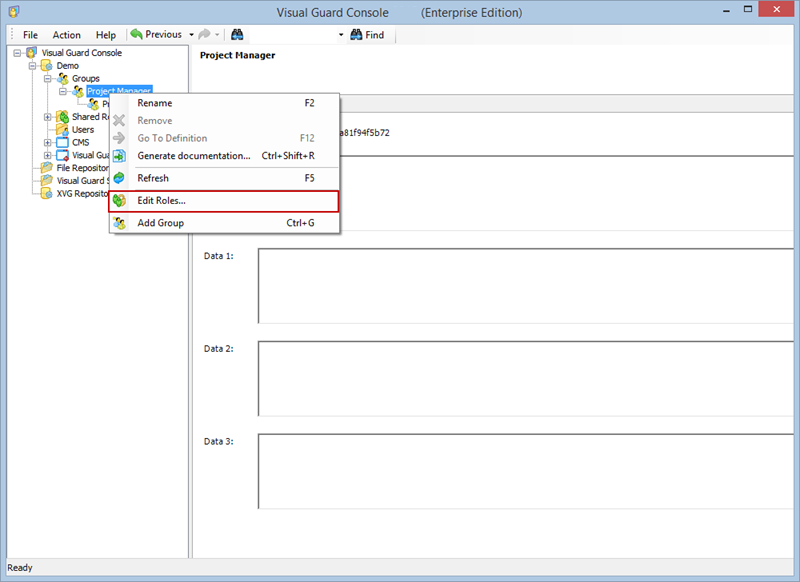
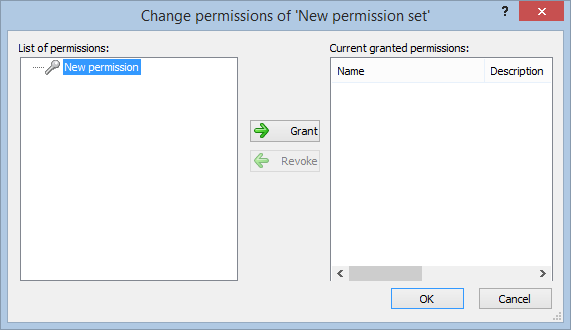
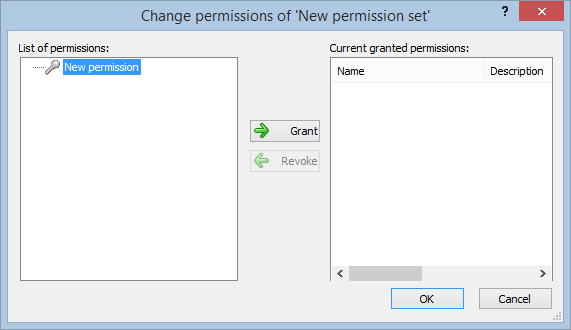
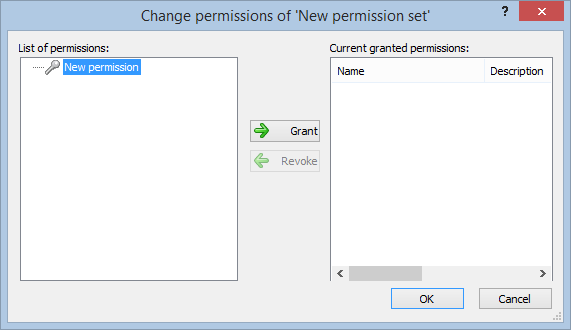
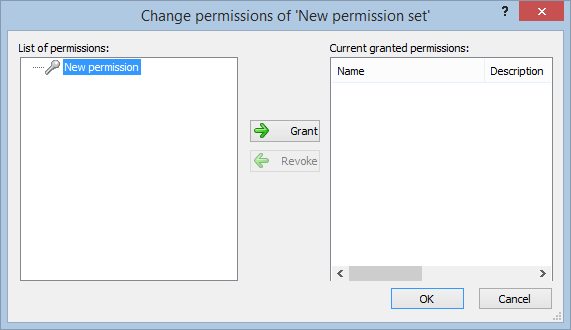
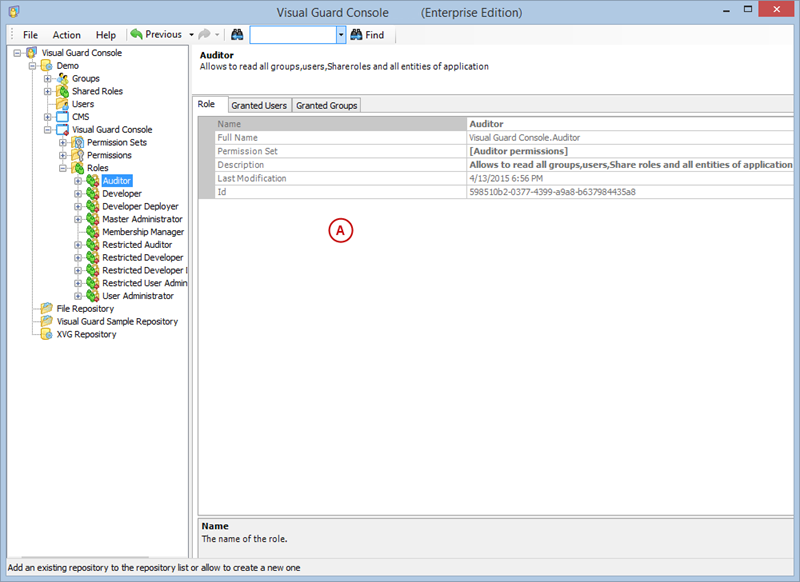
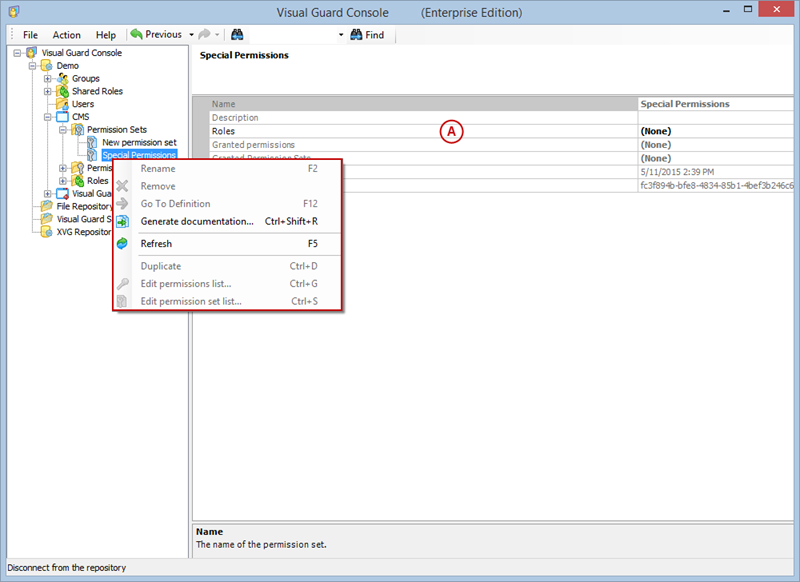
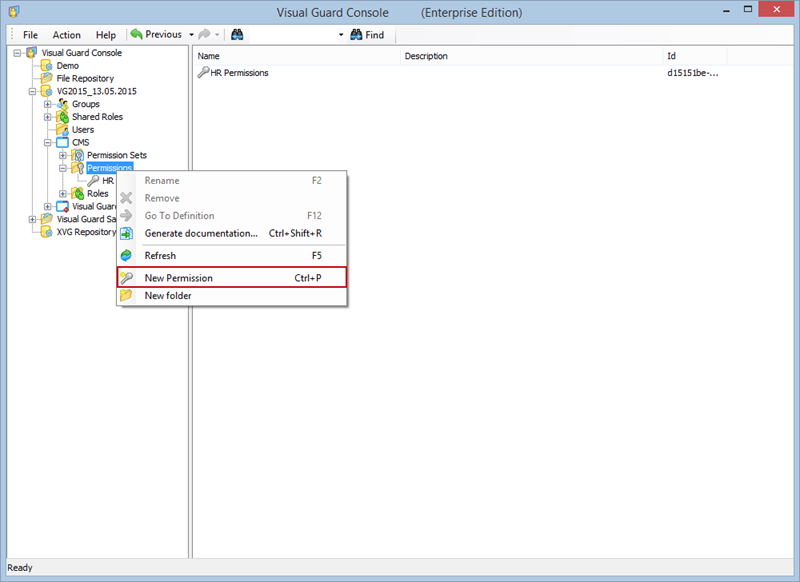
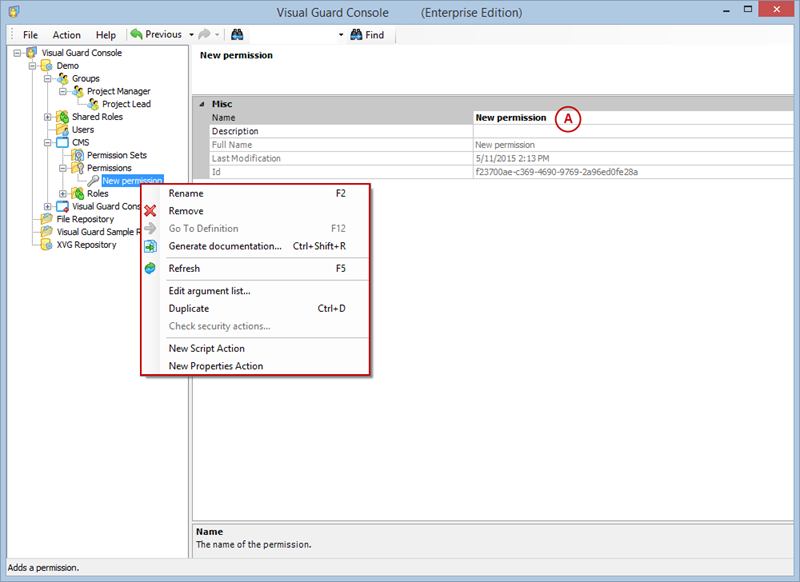
- Navigate to the permissions section and assign the relevant permissions to the role.
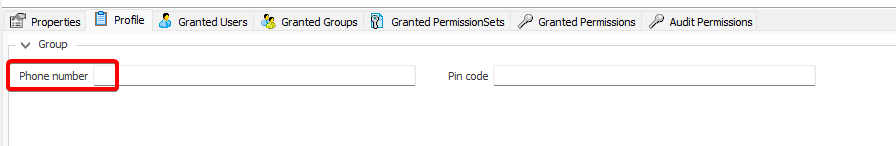
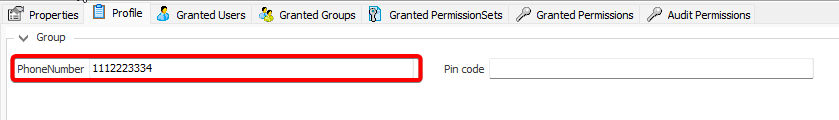
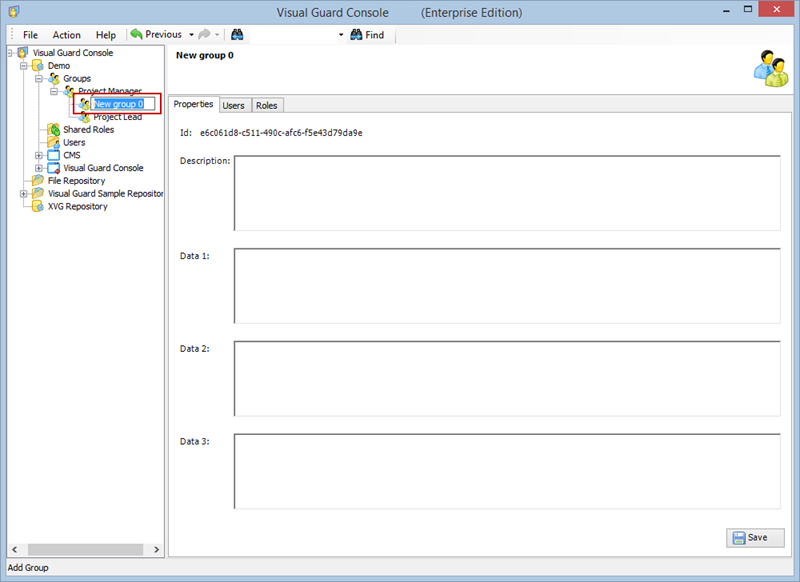
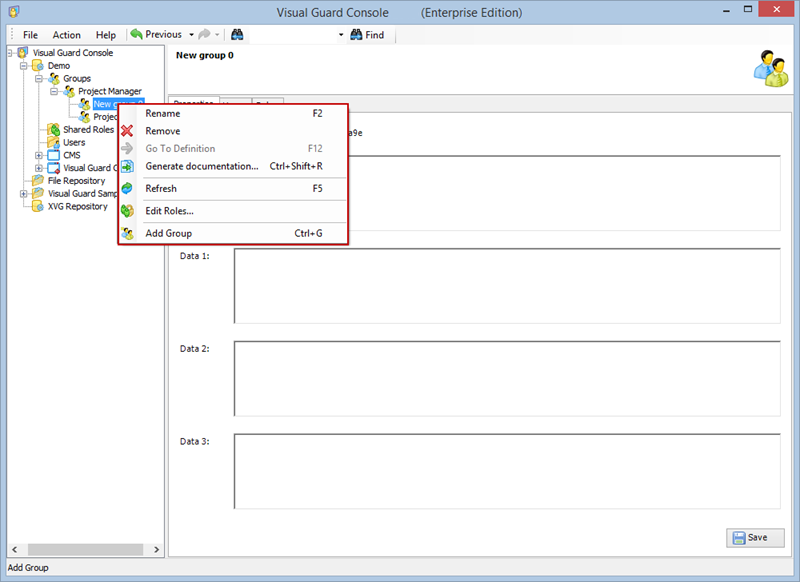
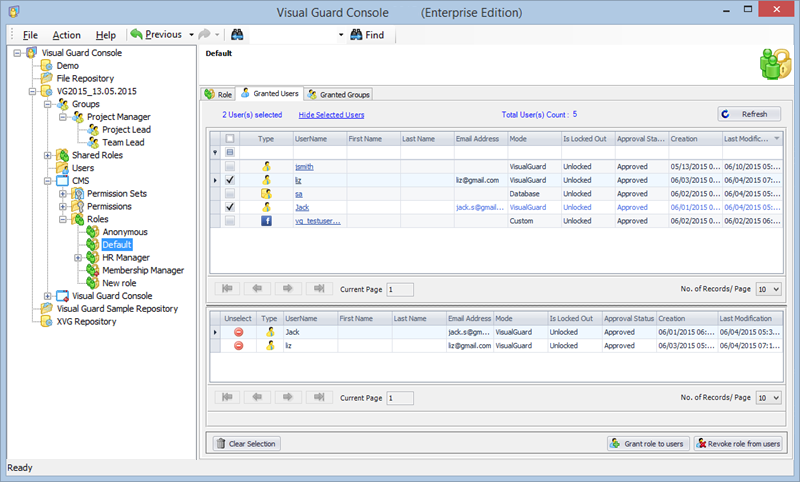
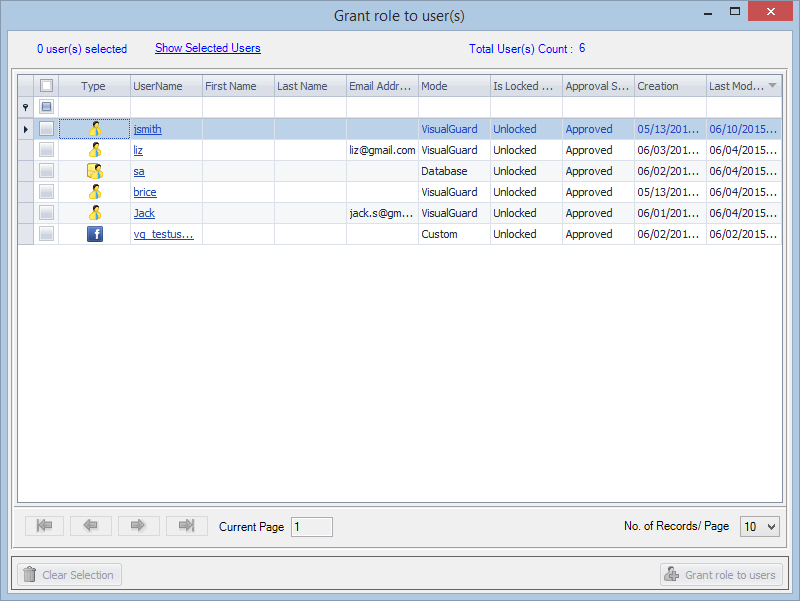
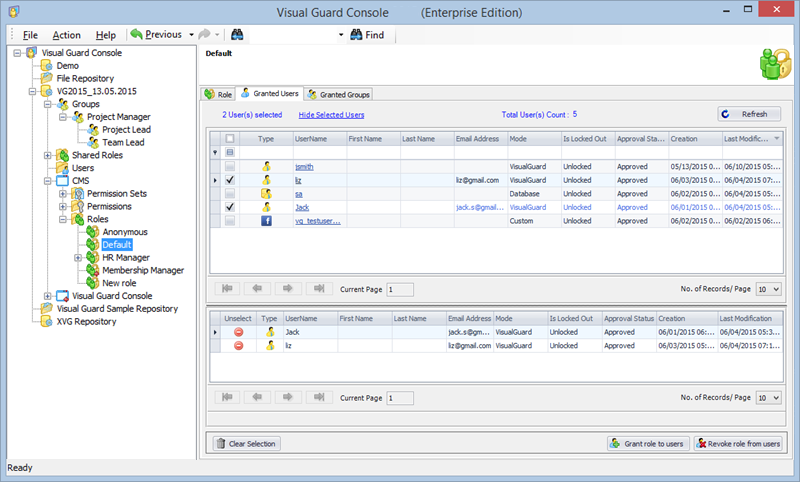
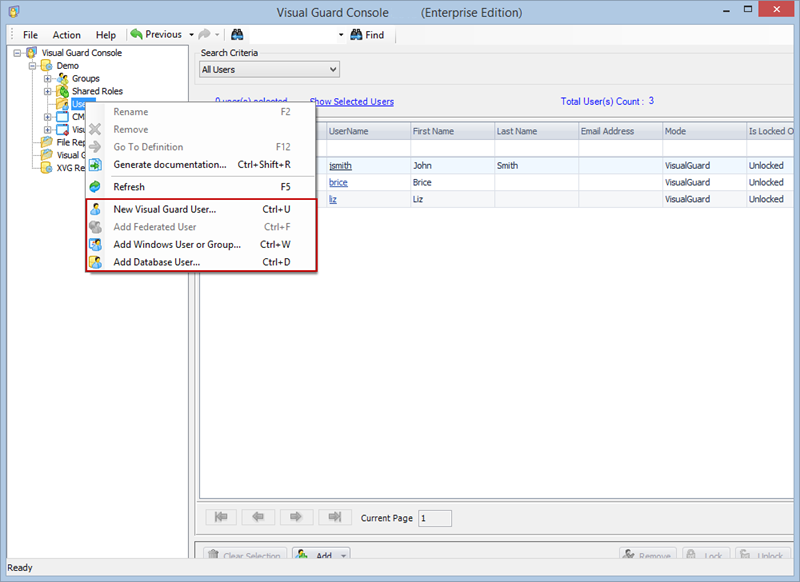
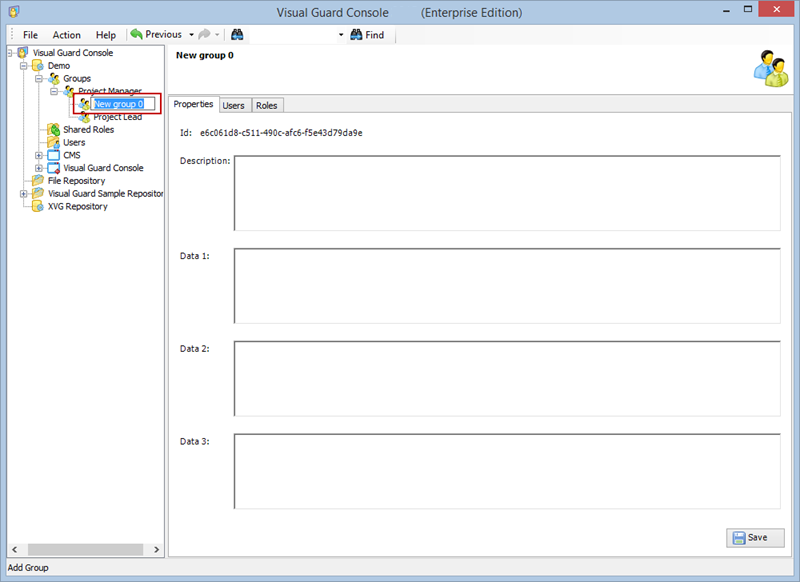
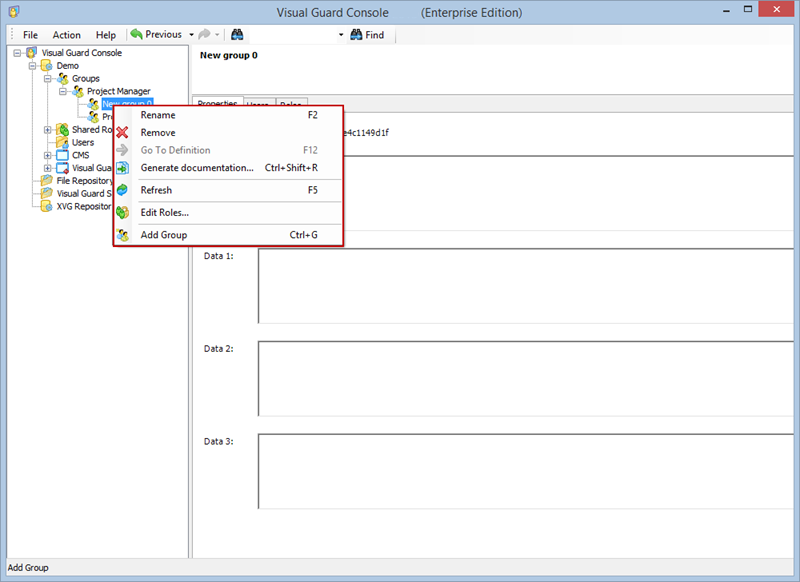
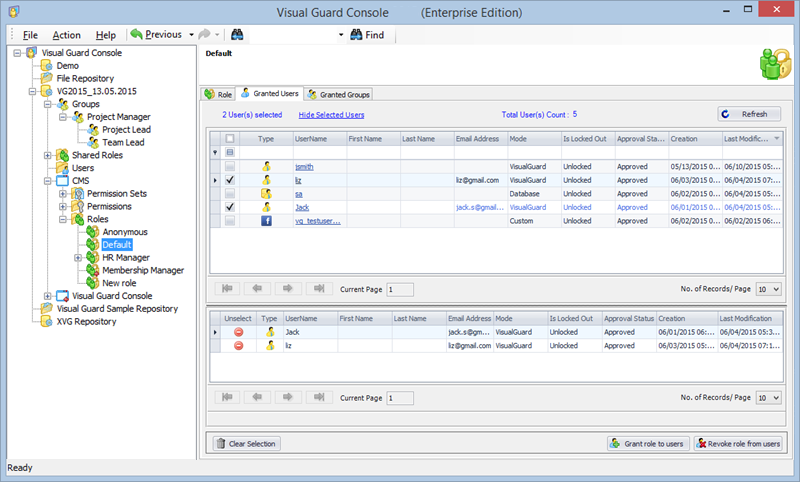
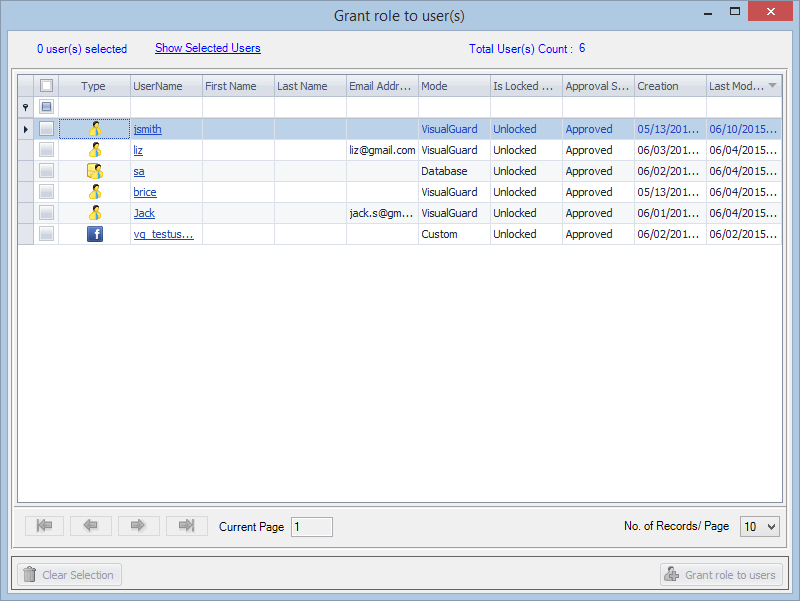
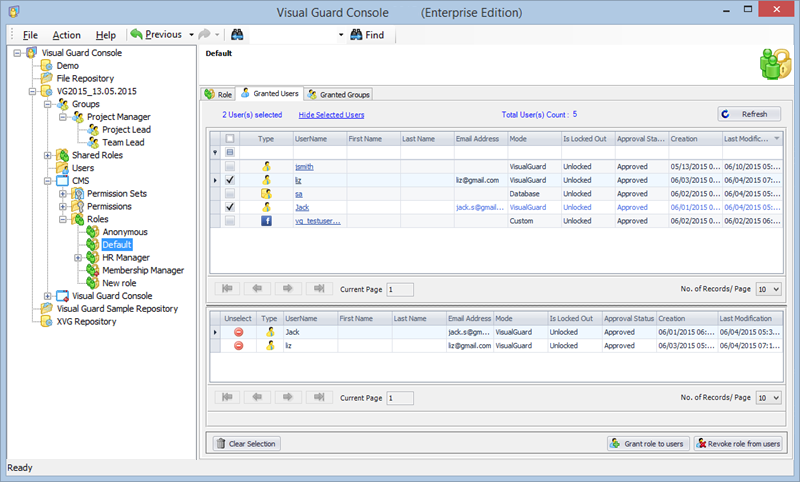
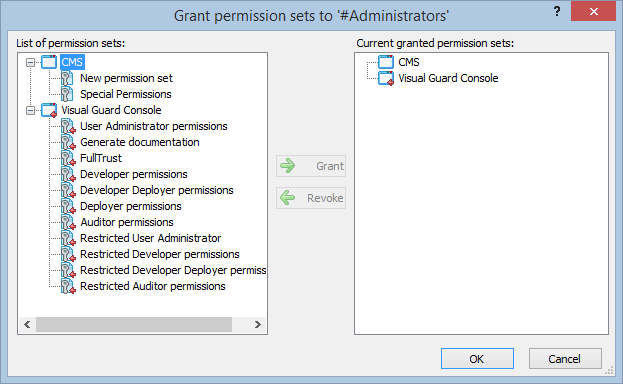
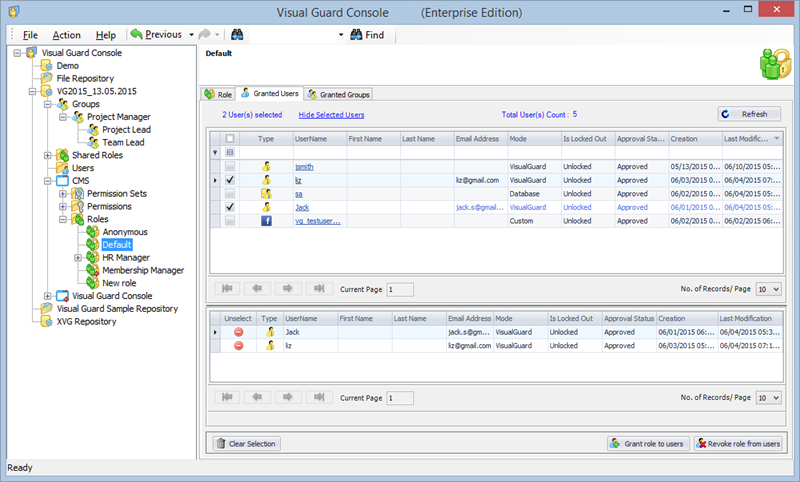
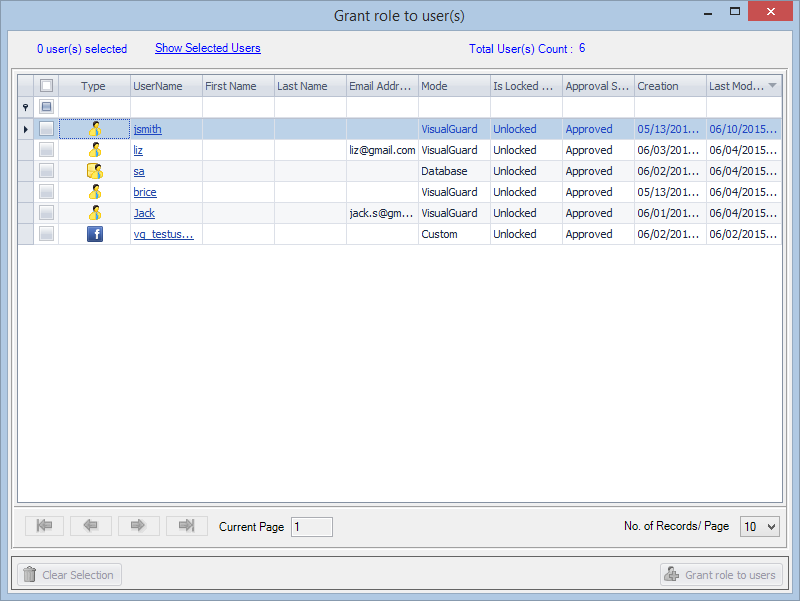
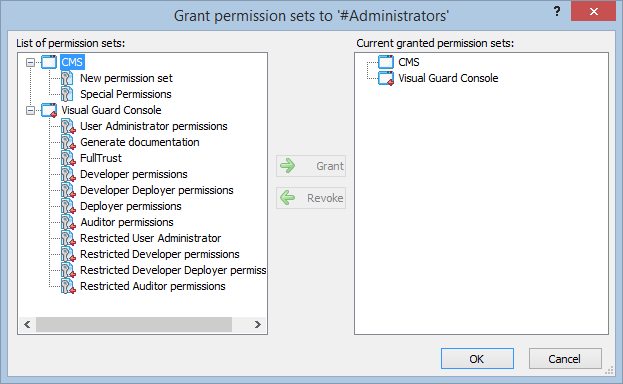
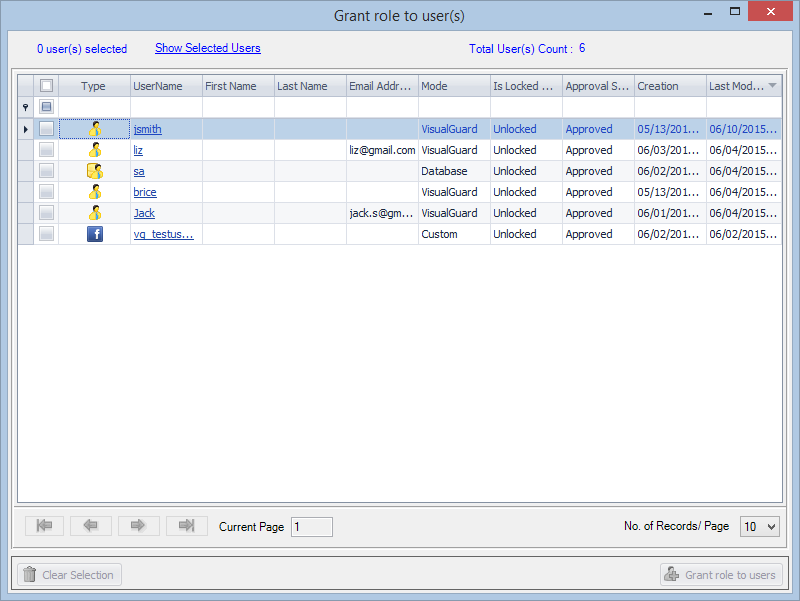
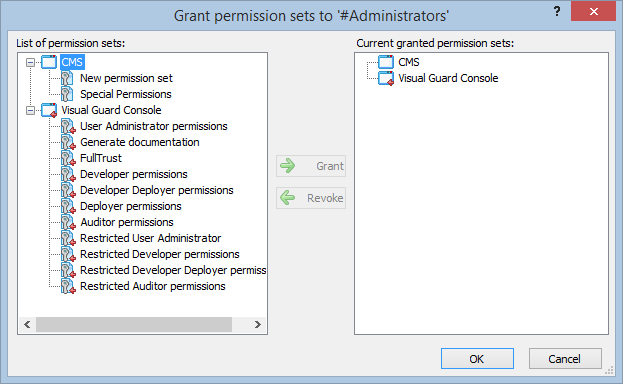
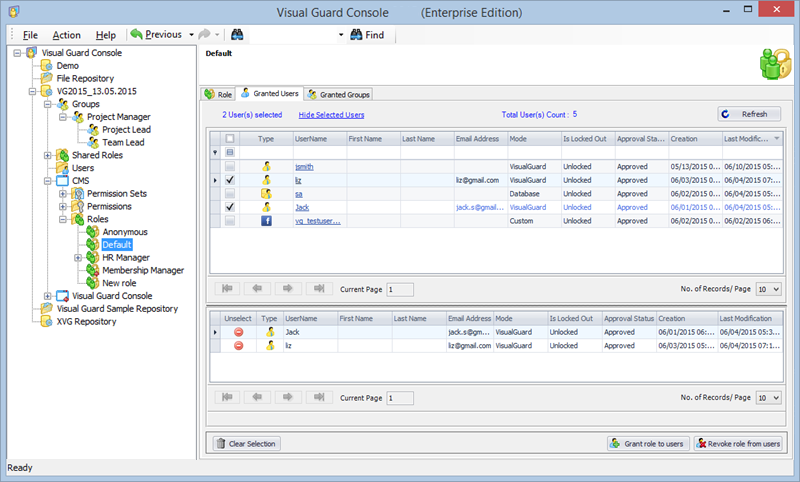
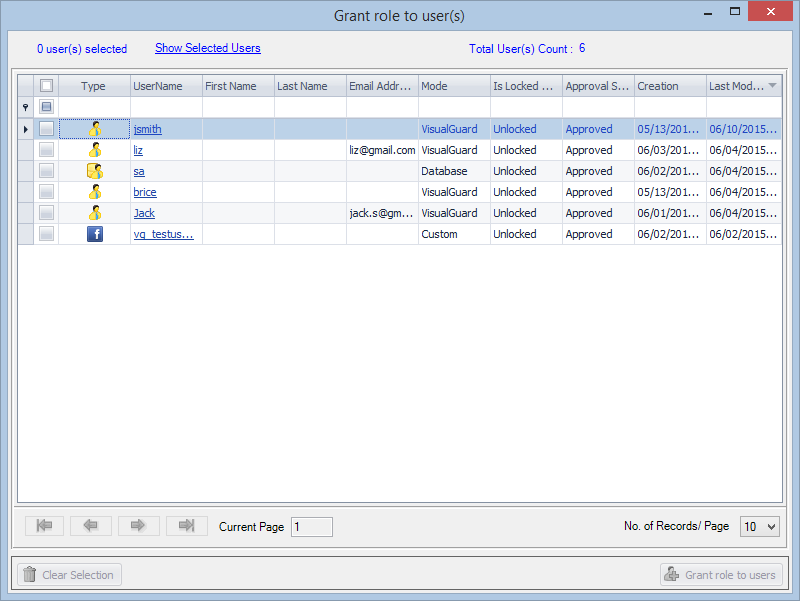
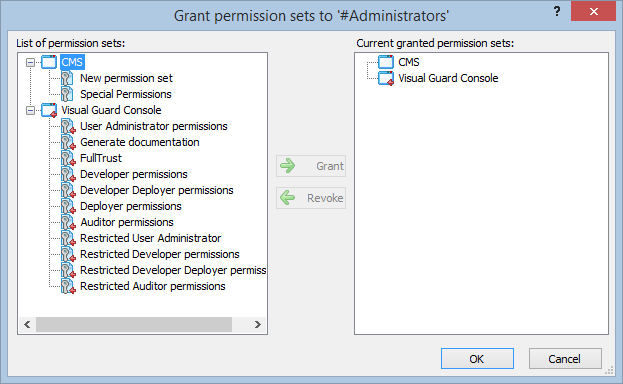
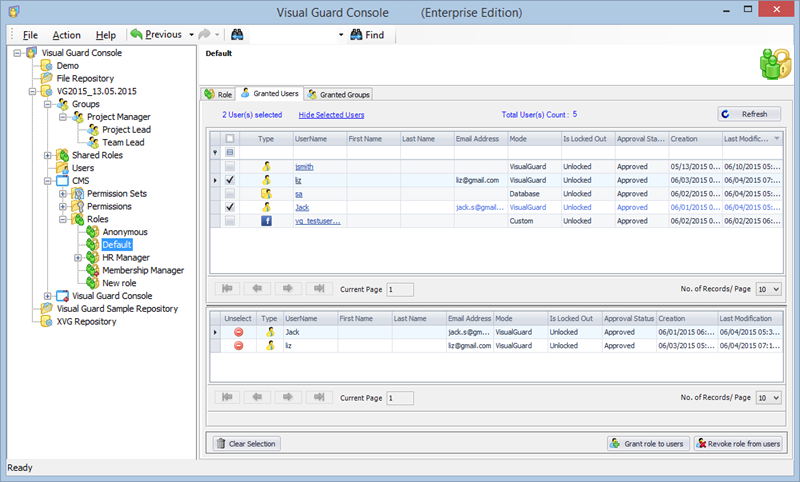
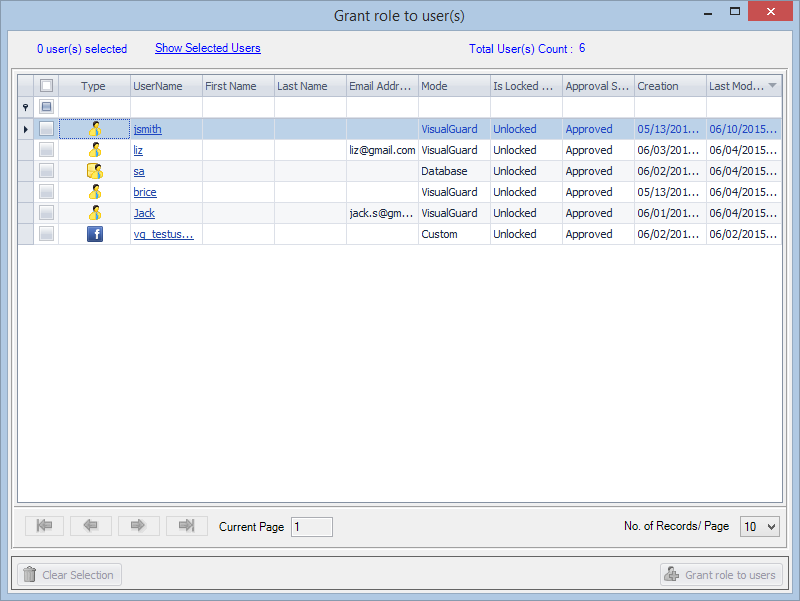
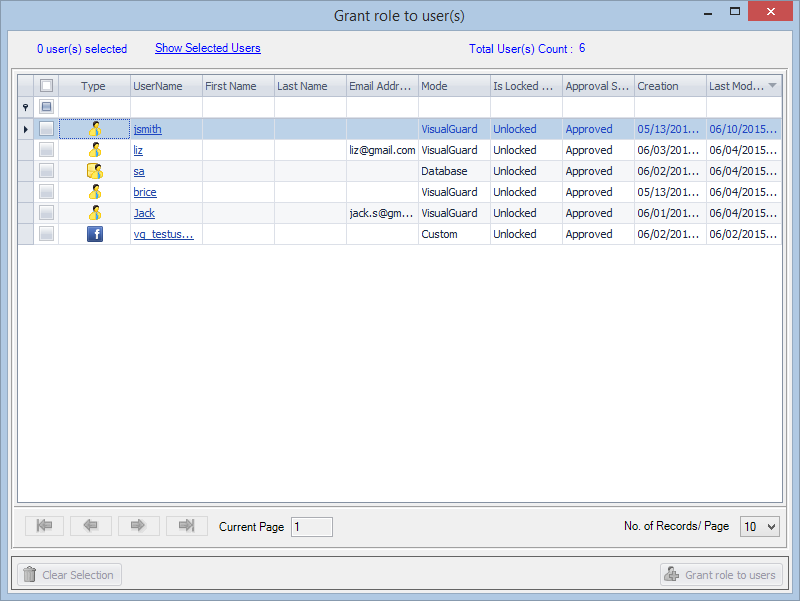
- Navigate to the groups section and create a new group. Assign roles and users to the group as needed.
- Save your changes.
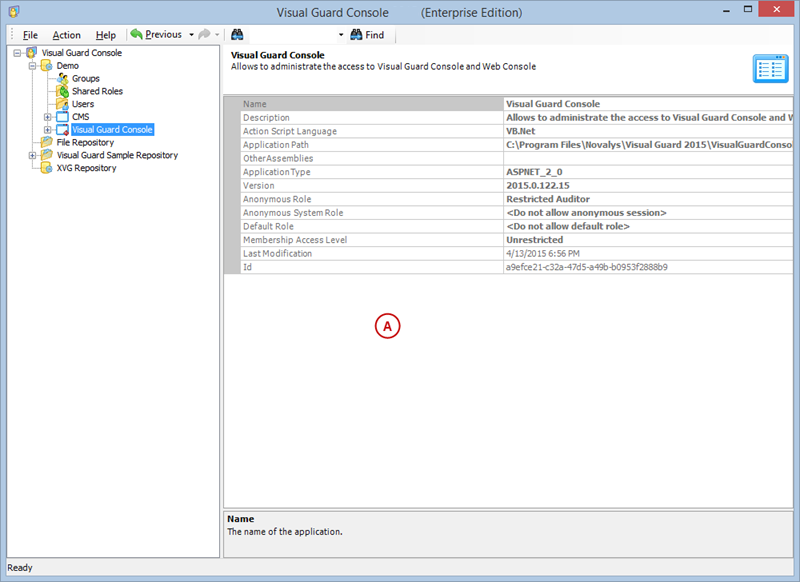
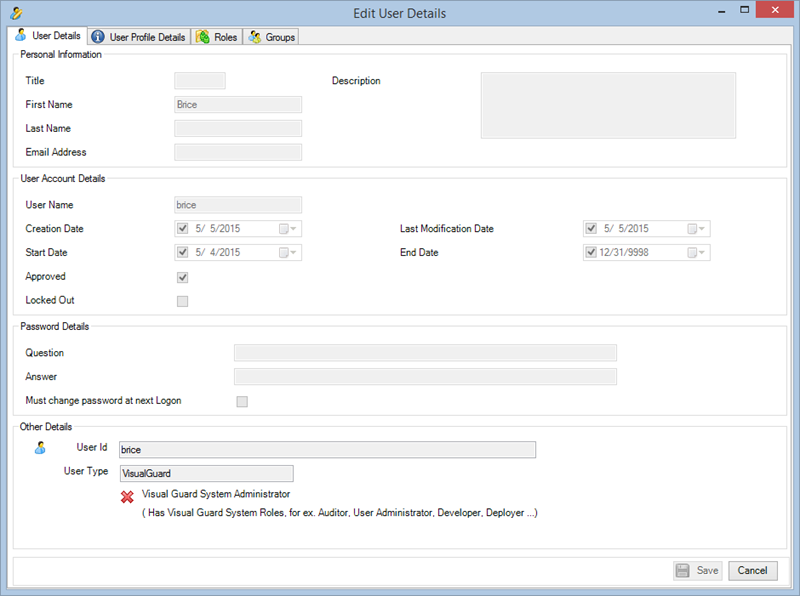
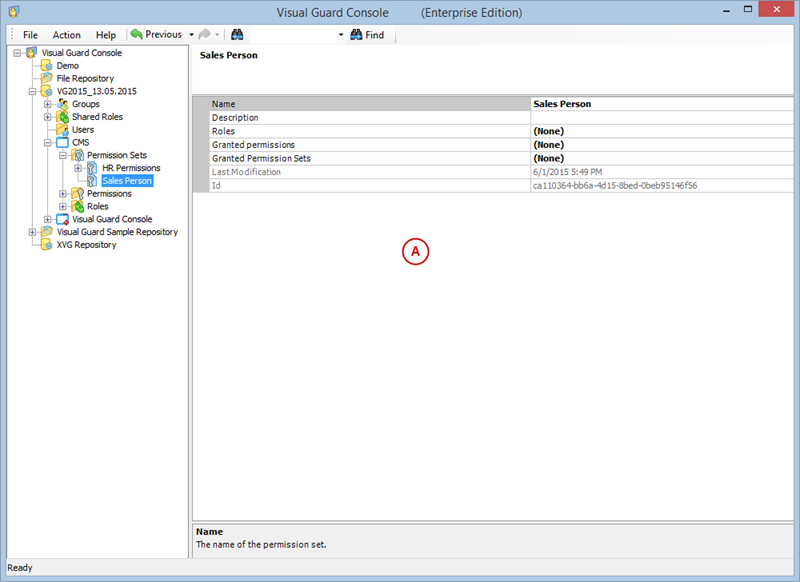
User Roles, Permissions, and Groups
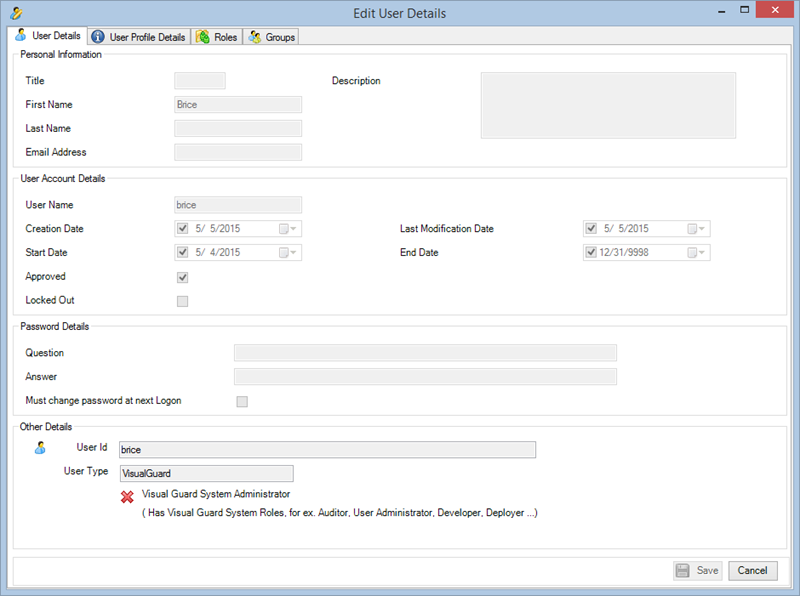
With Visual Guard, you can create and manage different user roles, each with its own set of permissions. You can also create groups to manage multiple roles and users simultaneously.
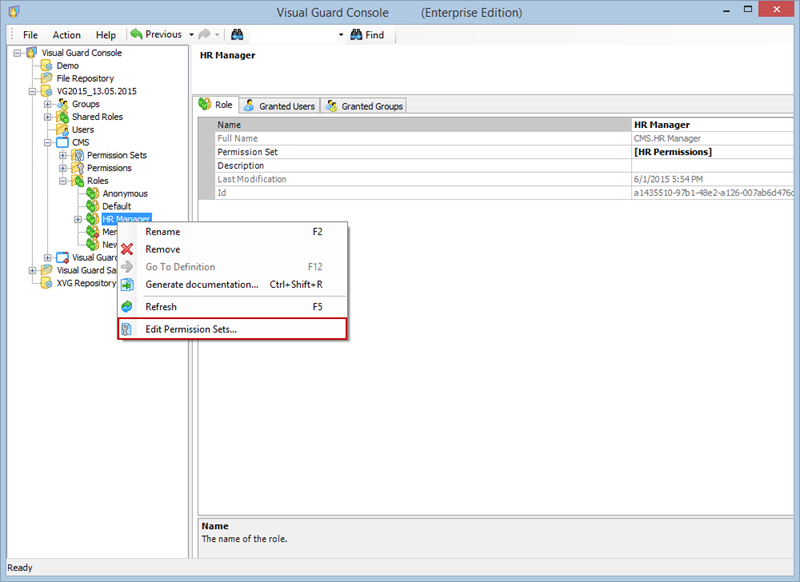
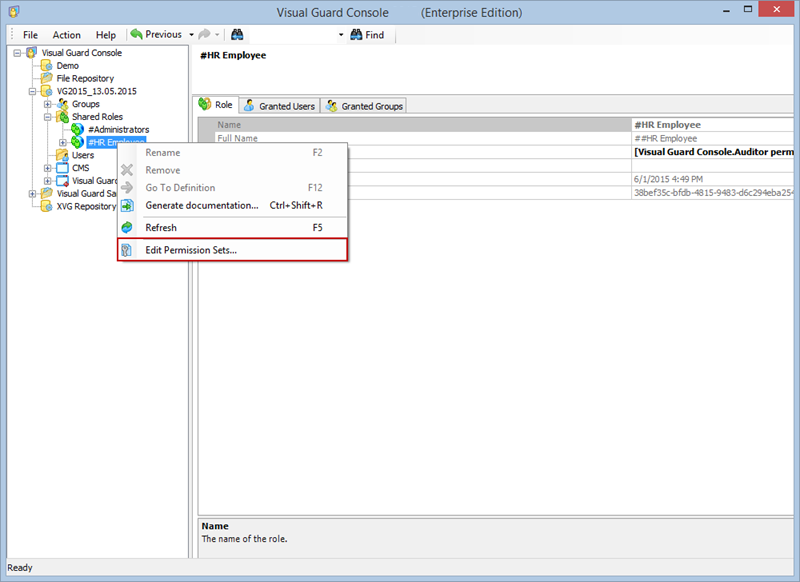
Creating a User Role, Assigning Permissions, and Setting up Groups
- Open Visual Guard WinConsole or WebConsole.
- Navigate to the user roles section.
- Click on ‘Add new role’ and name the role.
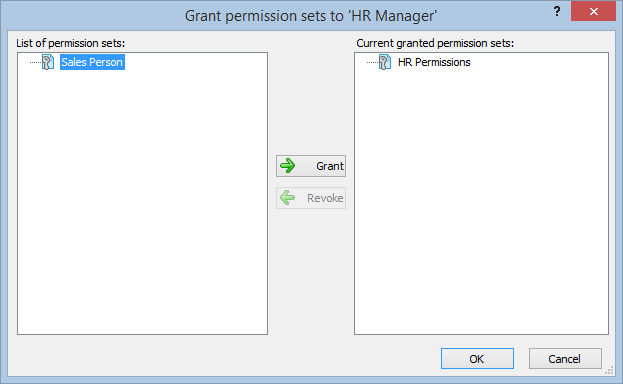
- Navigate to the permissions section and assign the relevant permissions to the role.
- Navigate to the groups section and create a new group. Assign roles and users to the group as needed.
- Save your changes.
 Note
Note