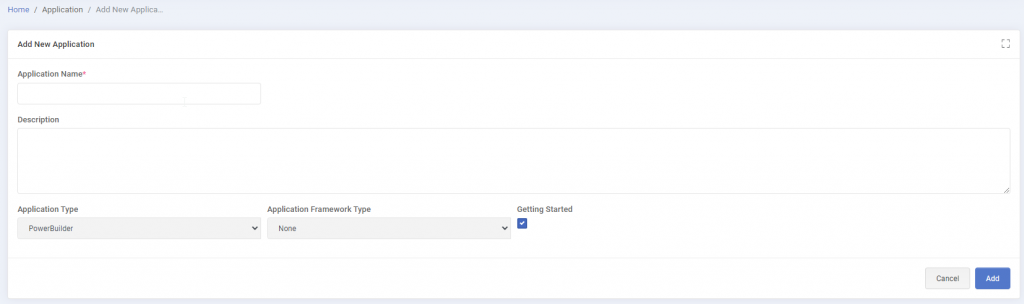
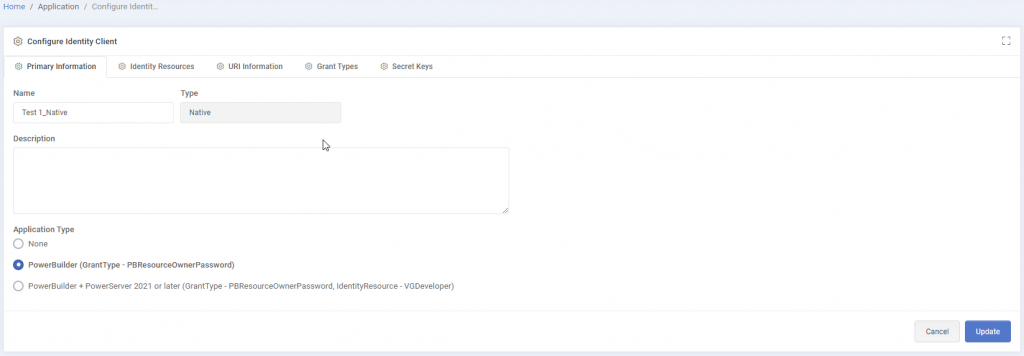
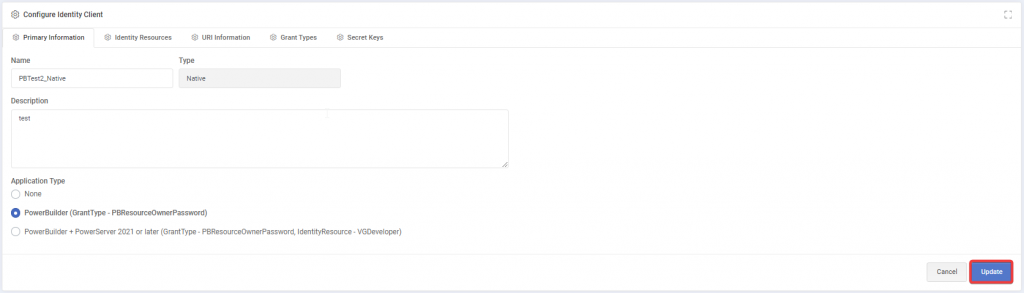
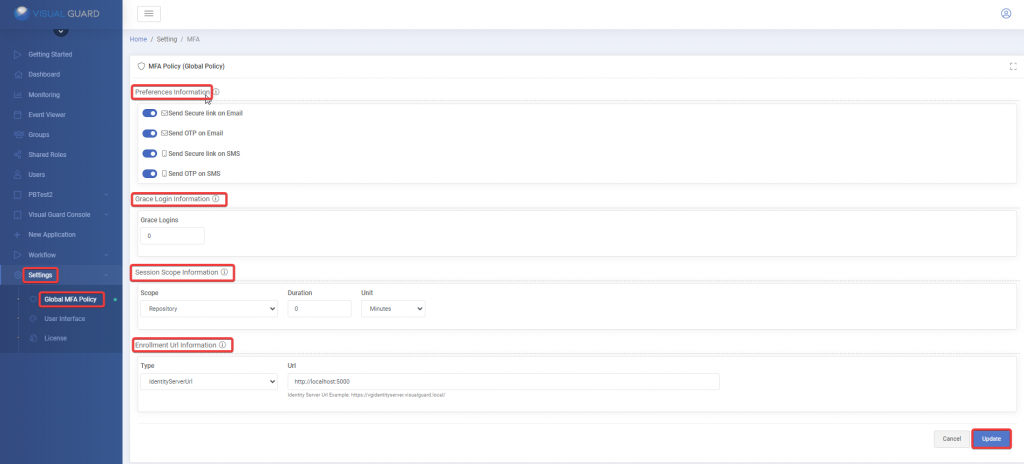
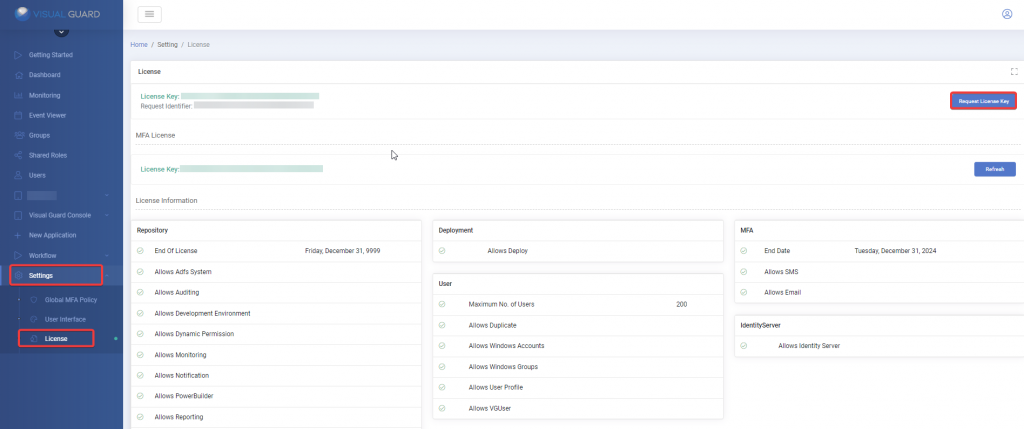
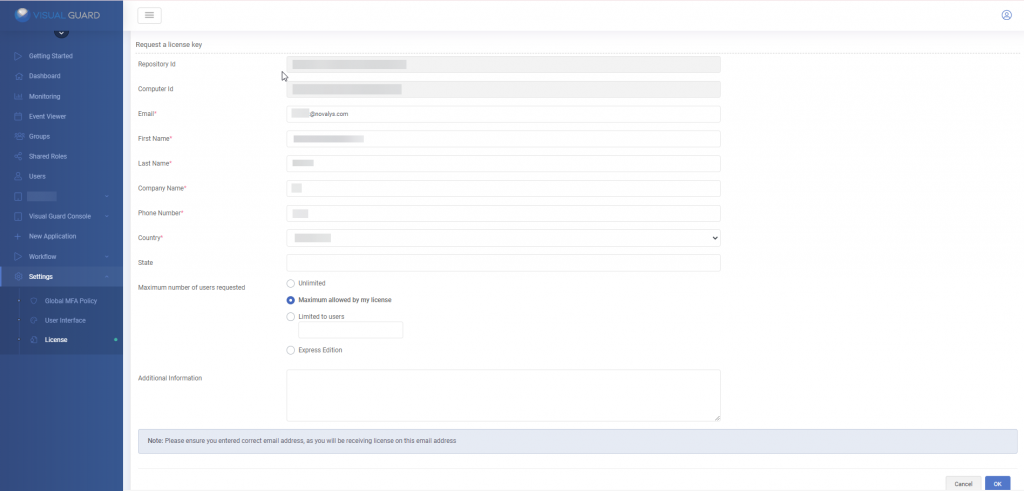
1. Installation Setup
System Requirements
- Operating System: Windows Server 2012, 2016, 2019, 2022
- Hard Drive: 512 GB to 1 TB Fast drive recommended – ideally SSD.
- CPU: Minimum of 4 cores, operating at 3 GHz or higher.
- RAM: At least 8 GB.
- Software:
- Web browser with JavaScript support.
- .Net Core hosting bundle 6.0.You can download the hosting bundle (dotnet-hosting-6.0) from the official Microsoft website. (https://dotnet.microsoft.com/en-us/download/dotnet/thank-you/runtime-aspnetcore-6.0.26-windows-hosting-bundle-installer)
- IIS with the necessary Windows features should be installed as described below.
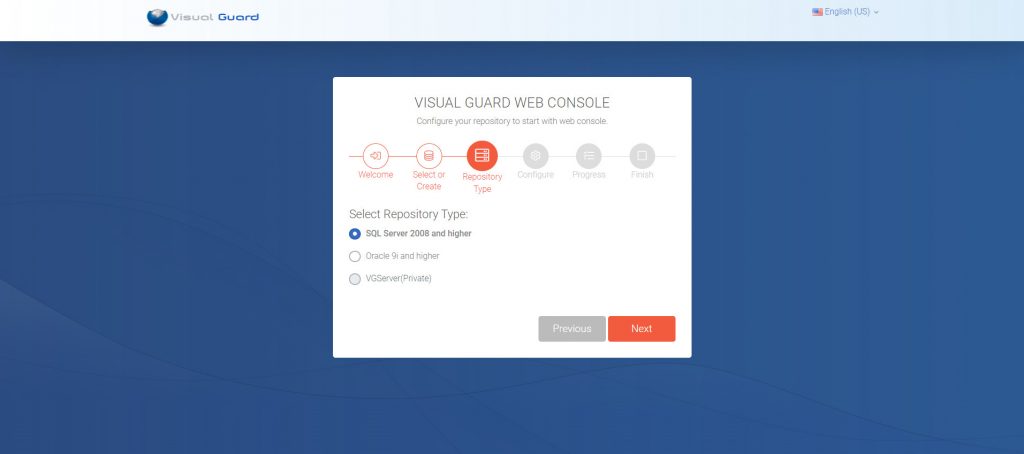
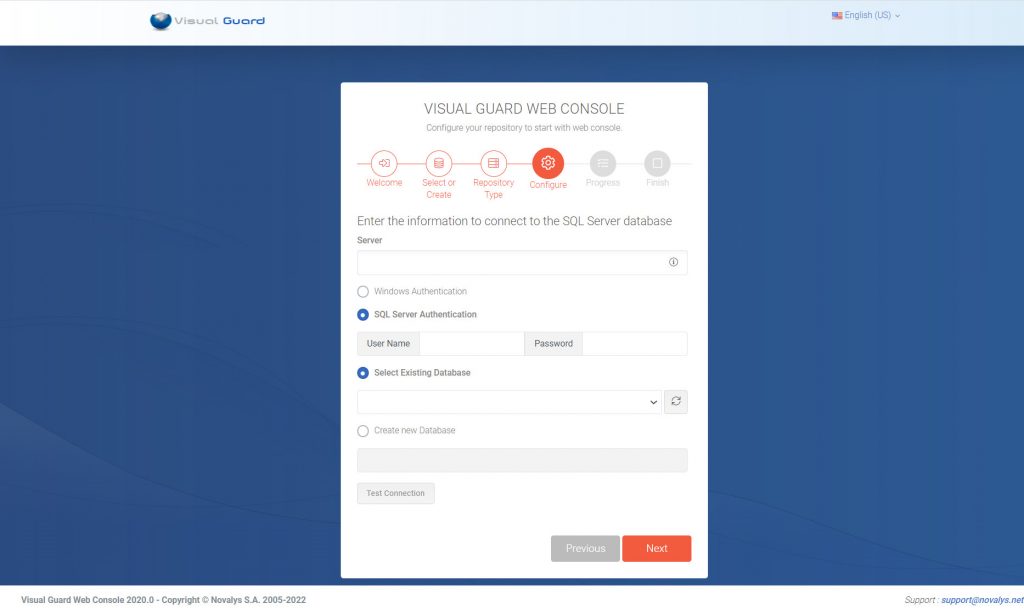
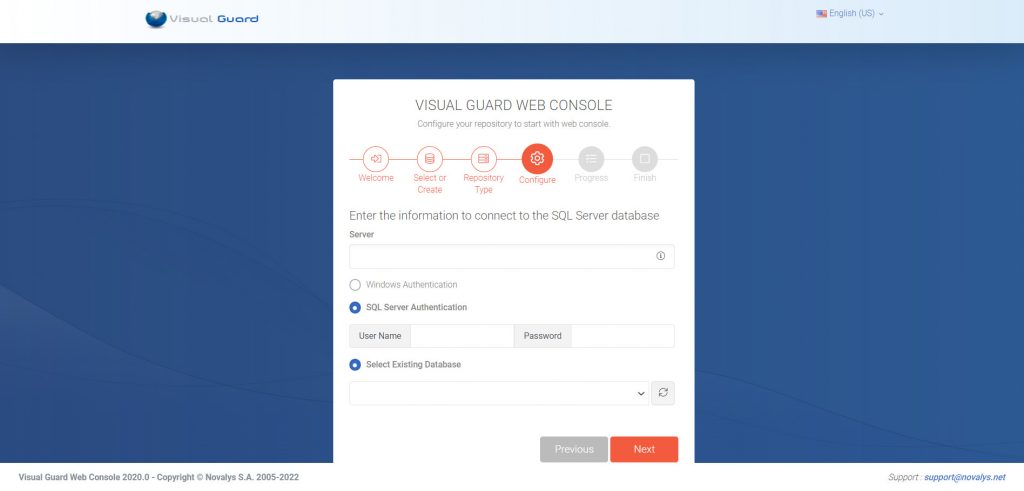
- VGRepository
- Require SQL Server 2012 or later, with a minimum of the Standard Edition.
- Require Oracle Database with Oracle9i or later. Please ensure the Oracle Driver is installed.
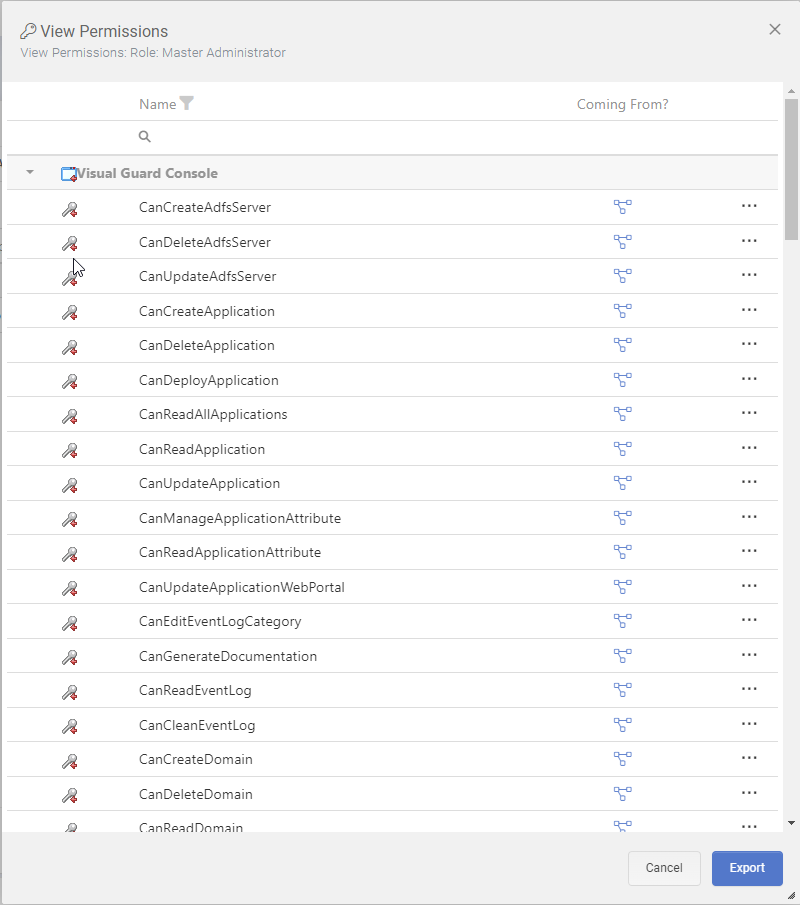
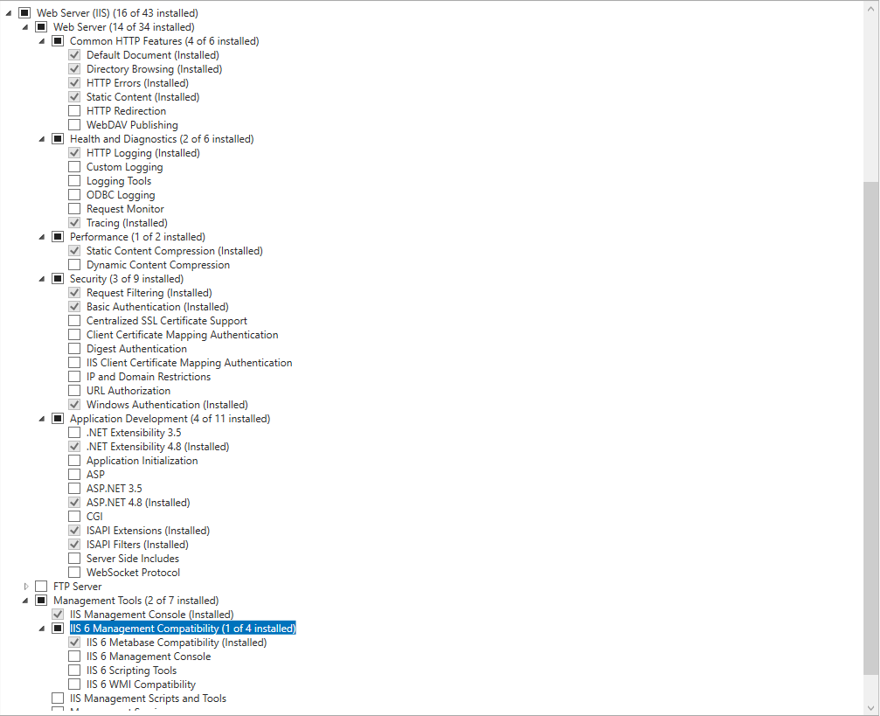
- Install Internet Information Services (IIS): IIS is a web server software package designed for Windows. It’s used for hosting websites and other content on the web. You can install it through the “Turn Windows features on or off” menu in the Control Panel. The below screenshot shows which functions should be checked and vice verse.
2. Download and Install .NET Core Hosting Bundle: The hosting bundle includes the .NET Core Runtime 6.0, .NET Core Library, and the ASP.NET Core Module. The ASP.NET Core Module is a necessary component for hosting ASP.NET Core applications on IIS. You can download the hosting bundle (dotnet-hosting-6.0) from the official Microsoft website. (https://dotnet.microsoft.com/en-us/download/dotnet/thank-you/runtime-aspnetcore-6.0.26-windows-hosting-bundle-installer)
3. Restart IIS: After installing the .NET Core Hosting Bundle, you should restart the IIS to ensure the changes take effect. You can do this by opening a command prompt as an administrator and running the command iisreset.
4. Verify the Installation: You can verify that .NET SDK and ASP.NET Core Runtime are correctly installed by opening a command prompt and running the following commands:
- For ASP.NET Core Runtime:
dotnet --list-runtimes
These commands should display the versions of ASP.NET Core Runtime that are installed on your machine.
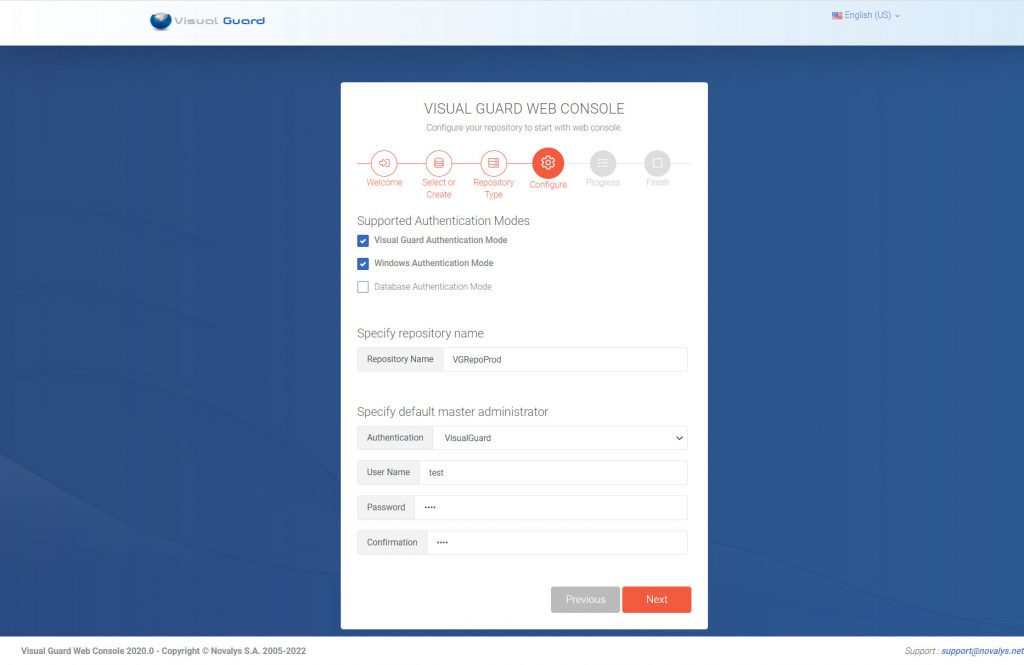
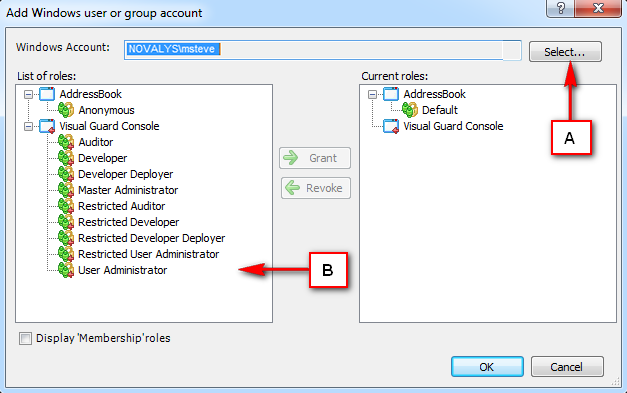
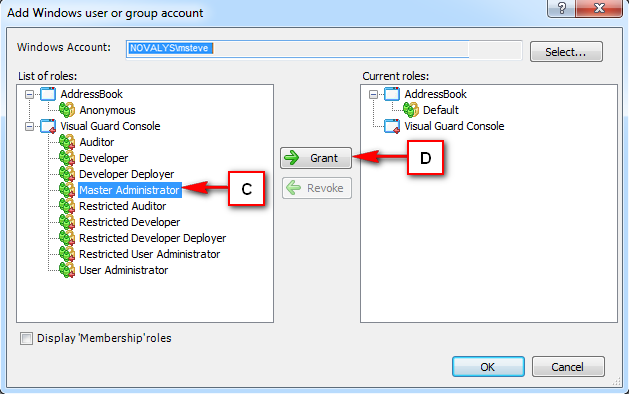
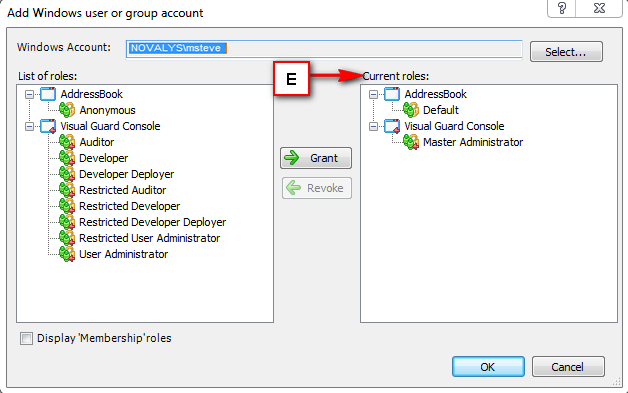
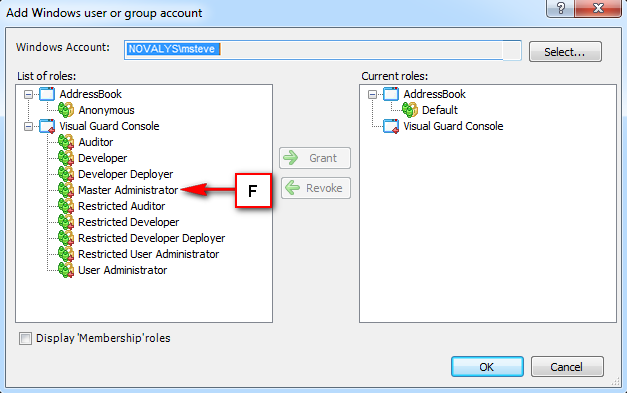
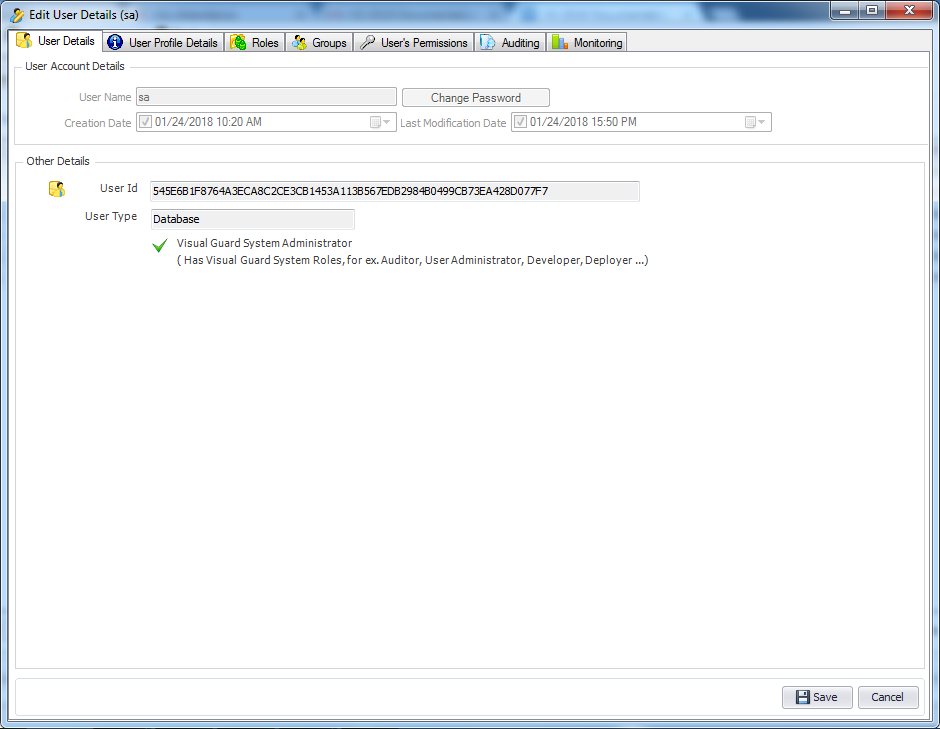
5. Install Visual-Guard WebConsole: Once IIS, .NET Core SDK, and ASP.NET Core Runtime are installed, you can proceed with the installation of Visual-Guard WebConsole. Follow the instructions provided by Visual-Guard for this process.
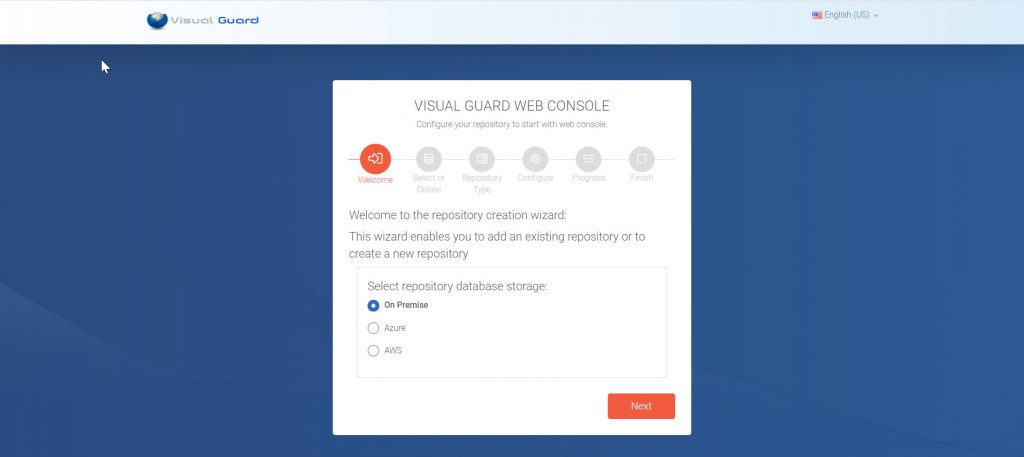
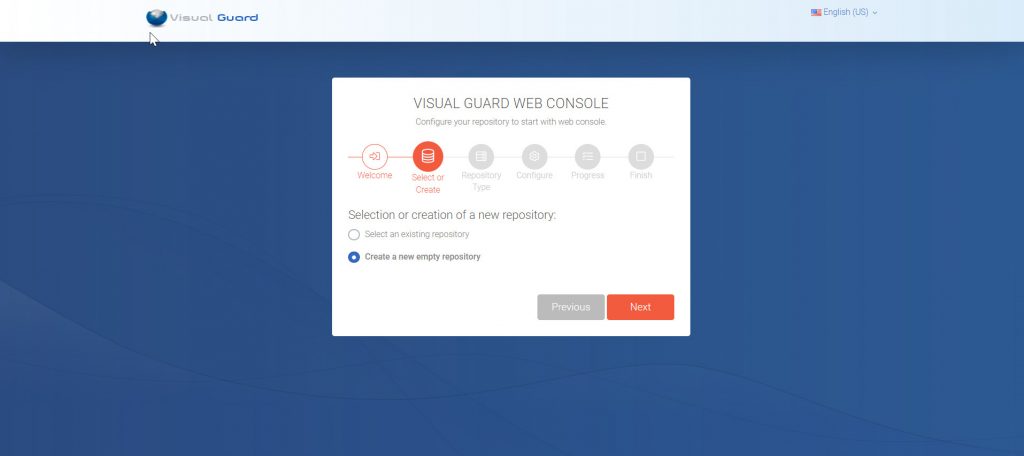
Installation Guide
The Visual Guard WebConsole needs to be installed on your server. Follow these steps for a successful installation:
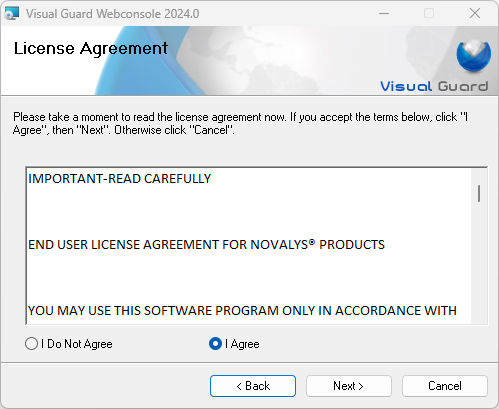
- License Agreement: Accept the license agreement to proceed with the installation.
- Installation Details: Provide the necessary information, including:
- The site
- The virtual directory
- The application pool (“No Managed Code” as .NET CLR Version)
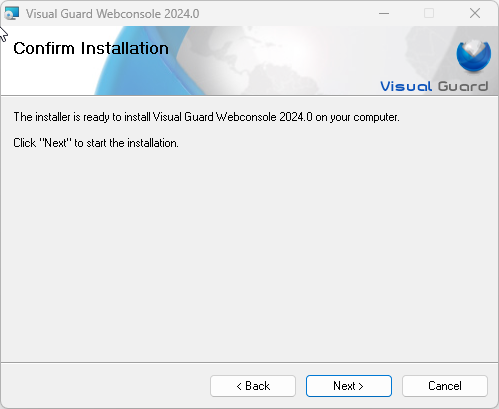
- Confirmation: Confirm to initiate the installation of the console on your server.
- Installation Process: Please be patient while the installation process is underway.
Installation
- Step 1: The Visual Guard WebConsole needs to be installed on your server. Follow these steps for a successful installation:
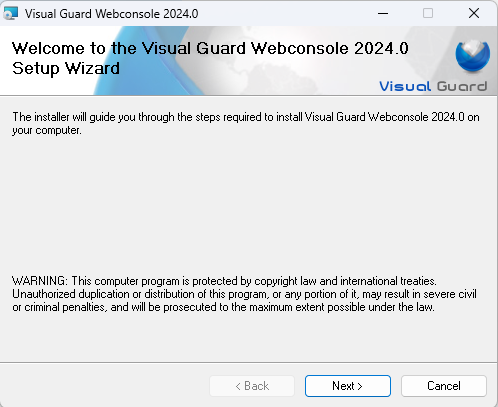
- Step 2: License Agreement: Accept the license agreement to proceed with the installation.
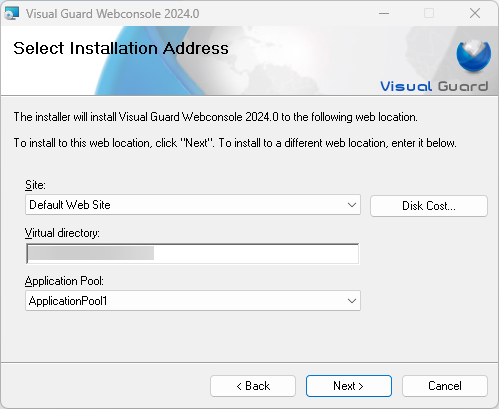
- Step 3: Installation Details: Provide the necessary information, including:
- The site
- The virtual directory
- The application pool
Click ‘Next’ to continue with the installation.
- Step 4: Confirmation: Confirm to initiate the installation of the console on your server.
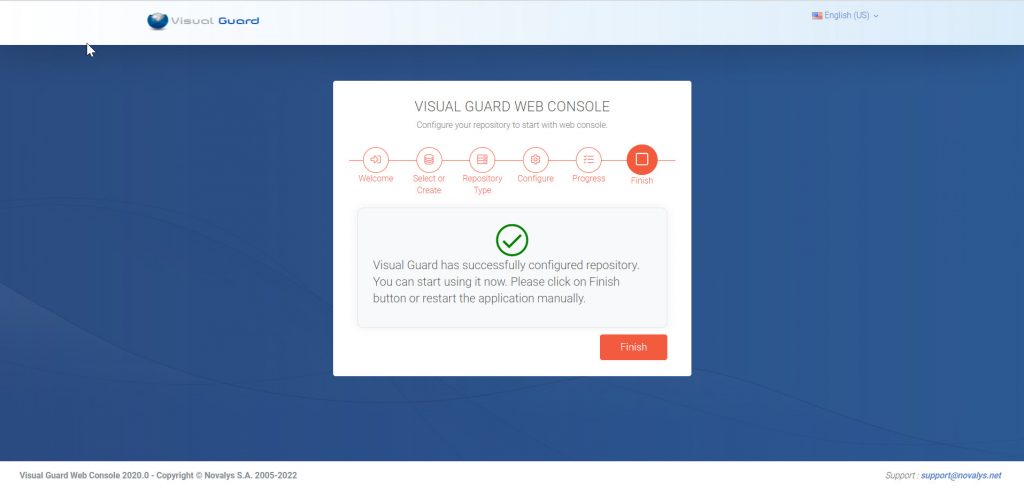
- Step 5: Installation Process: Please be patient while the installation process is underway.
- Step 6: Installation Complete.